Recent Entries
Tech (63)
Latest news about Django, the Python web framework.
From The Django weblog at 2025-07-02 12:00:00
Django bugfix release issued: 5.2.4
Today we've issued the 5.2.4 bugfix release.
The release package and checksums are available from our downloads page, as well as from the Python Package Index.
The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E
From The Django weblog at 2025-06-30 11:00:00
Django has always been more than just a web framework; it’s a testament to what a dedicated community can build together. Behind every Django release, bug fix, or DjangoCon is a diverse network of people working steadily to strengthen our open-source ecosystem. To celebrate our collective effort, the Django Software Foundation (DSF) is excited to share our 2024 Annual Impact Report 🎉
In this report, you’ll discover key milestones, narratives of community folks, the impact of the events running throughout the year, and much more, ramping up to how we’re laying the groundwork for an even more resilient and inclusive Django community.
Why we publish this report
Transparency is essential for our community-driven organization. Everyone deserves to know how our work and investments translate into real impact. It’s more than just statistics. It’s our way to:
- Show how your contributions make a difference, with vibrant highlights from the past year.
- Reflect on community progress, recognizing the people and ideas that keep Django thriving.
- Invite more individuals and organizations to get involved.
Looking ahead: call to action
As we make progress through 2025, the Django Software Foundation remains dedicated to strengthening the ecosystem that supports developers, contributors, and users around the world. With a growing network of working groups, community initiatives, and the commitment of volunteers, we’re focused on nurturing the people and executing ideas that make Django what it is: the web framework for perfectionists with deadlines.
Help keep this momentum strong by supporting Django through any of the following ways:
- Donate to Django to support future development
- Convince your company to become a Corporate Member
- Join the Foundation as an Individual Member
- Get involved with the working groups
- Join our community on the Django Forum or Discord server.
- Follow and re-share our posts on Mastodon, on Bluesky, or on X.
- Follow our page on LinkedIn.
Thank you, everyone, for your dedication and efforts. Here’s to another year of collaboration, contribution, and shared success!
From The Django weblog at 2025-06-27 07:51:21
Watch the DjangoCon Europe 2025 talks
They’re now all available to watch on YouTube, with a dedicated playlist ⭐️ DjangoCon Europe 2025 Dublin. For more quality Django talks in 2025, check out our next upcoming events!
All the DjangoCon Europe talks




























From The Django weblog at 2025-06-17 18:09:45
DSF member of the month - Elena Williams
For June 2025, we welcome Elena Williams as our DSF member of the month! ⭐

Elena is a dedicated member of the Django community. She is part of the Code of Conduct Working Group and she is a Django Girls organizer in Australia. She has been a DSF member since July 2014.
You can learn more about Elena by visiting Elena's website and her GitHub Profile.
Let’s spend some time getting to know Elena better!
Can you tell us a little about yourself (hobbies, education, etc)
My background is that I was always interested in computers, though my parents were more creative types, my Dad was an Architect (of built structures). When I was a kid we had computers for CAD around the house before it was common. I was always into STEM subjects, but unfortunately in that era for girls to do engineering it was a bit too hostile for me, so I trained in finance instead and worked in that industry (finance and banking, MNE orgs) for nearly a decade. I kept coming back to coding and was always building computers, and was obsessed with the internet as a technology from pretty early on. Just after I discovered Django I did a Masters in Computing at ANU. To this day my main hobbies are programming/webdev (very much a person who codes for fun) and the open source community. My persistent other hobbies are hackspace activities, I like CNC and laser stuff, but will pick up any and all tools/mediums and give them a go, lately been spending time with blender and cabinetry. When I can, I like to get away to snowboard or kitesurf, and this wild Australian long distance endurance navigation sport called rogaining. Really at the moment I’m mostly focussed on being a parent (which is an awesome experience), my friends (mostly python related), my job and working on the community here in Australia. With my family we go camping/hiking more than most. I’ve also continued to be a sessional academic at ANU teaching software engineering for many years.
How did you start using Django?
Golly, I’ve been using Django forever. I’d started doing web stuff in the early ‘00s and worked in a range of languages and paradigms. I was working in a physics research institute at a high profile university in Australia doing web stuff and made friends with a bunch of the doctoral students. In around 2007, one of these students, and my good mate, Dave, randomly recommended this new framework Django and Python (and emacs also actually but that’s a different story). Basically I got into it immediately and never looked back and went on to build a career around Django (actually Dave later gave up physics and did the same thing too). I’ve been engaged with the Python and Django communities to varying degrees since about 2011 as well. To be honest when I discovered the language and the framework I really didn’t expect to still be passionate about them all these years later but I really am! Hopefully I can continue to be well into the future also.
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
Over the years (being a curious person) I’ve worked with many many web frameworks and technologies, the vast majority of the big ones. In recent years I’ve been spending time with FastAPI and SQLAlchemy as well as non-python technologies. Django is better though.
Not using Django as much at the moment makes me love it even more and realise how lucky we are with such a well designed and well supported framework. It’s not perfect but it’s outstanding.
Having said that: at a technical level I’d love to have “cheaper” ways (in every sense) to deploy. Even though deployment methods have changed beyond recognition several times over the years, I always thought this would get easier over time and am kind of surprised that it hasn’t.
Very specific to me is that I need Django to have stronger support for many database schemas in the same project, but honestly this is just a specific problem I have inherited in a project at the moment, but it’ll pass eventually.
What projects are you working on now?
Over the last few years I’ve helped organise a number of events, including PyConAU, though realised I’d been taking on too many projects and trying to pull back actually! Still: Internationally I’m on DSF CoC with a great team. Nationally this year I’ve been serving on the committee of our main Australian open source foundation body, Linux Australia, as well as working in a small team trying to bring together all of the Australian python user groups under a banner we hope to call Python Australia and I’ve had a keen interest in python user groups around the world. In my home town I’ve been organising our local user groups for some time with an awesome team, as well as our fantastic local PyLadies.
For work I’m flat-chat working in a senior role on a Platform team in a small data company that provides “critical digital infrastructure” for Australia. Though my most important project of all at the moment really is my family, and I do really prioritise my friends and being healthy nowadays. I’m an avid hackerspace person and do have a couple of purportedly active projects (I’m obsessed with maps among other things) but these are relatively neglected at the moment as I just don’t have the bandwidth.
Which Django libraries are your favorite (core or 3rd party)?
I just love the ORM. We’re so spoiled in the Django community we don’t realise how mature and feature-rich the ORM is. Maybe I’m biased because I’ve been using it for so long I just “think” in Django ORM and I’ve been working away from it lately. It’s such a (comparative) pleasure to use. You can nit-pick at it but compared to anything else it’s so beautifully thought through.
The admin was the Django “killer app” in 2008 and I’d argue still is in 2025. To be some dozens of seconds away from a custom CMS backend at any time is still magical. Pony magical. It’s still as impressive as ever to show off to people. Also in the same way that Guido says python makes a great calculator: Django makes a great quick tool for really fast data munging, can’t describe how liberating it feels using it for this purpose.
Writing tests in Django is under-rated too.
There are so many amazing 3rd party libraries, too many to mention. For shout-outs I don’t think I have any projects without Debug Toolbar. The 3rd party caching libraries Memcache and Redis are both great. I’m also usually happy when I turn on Celery, and excited to see DEP-0014 on its way. Danny and Audrey’s Django Cookiecutter project is a great reference even if you don’t take the whole enchilada.
What are the top three things in Django that you like?
I’ve been lucky to generally have had a pretty great time with Django. Generally I’ve used it for projects where it was a really good fit and so it wasn’t painful. As such I like weird little quirky things about Django. Haters-can-hate but I actually really like a bunch of this controversial stuff, for example I like settings.py as a pattern for projects that aren’t out of control; I enjoy using and customising the management commands framework; I think Meta class as an approach to that type of awkward problem is neat; I’ve generally had a pretty nice time with the template language; I dig into utils and reuse them probably more often than most; ORM and the Tests obviously (it’s trivial to plugin pytest of course). Everything is a trade-off in software engineering and while I’m very biased: I just like the trade-offs that Django has chosen, they’re some of the best-in-class.
The top 3 things though? This is tough. I just like it. To nail down actual answers though:
- the framework workflow overall;
- that the project has stayed so consistently high quality and battle-hardened for so many years;
- and the community and my friends (shout out sp-wg)
I know you have start Django with one of the first version, what do you think of the evolution of the framework?
This is a great question! Thanks for being interested in this history, the Django history is a nice story of having good values and persisting and this actually being successful over the long run.
For me there’s all the “back in my day” stuff that’s not obvious now, like Python not being taken seriously as a “real” programming language, let alone javascript, but now those tides have very much turned, and web development is considered extremely respectable and high profile, which was unimaginable when I started. Django started in Web1.0 (whatever that meant), and actually grew substantially during Web2.0 and now even in the modern Web3 era is kind of establishing itself into being part of the backbone of the large parts of the internet that aren’t obvious. Thibaud has a list he maintains of websites that he believes use Django, this is great if you haven’t seen it.
One of the most impressive parts of the evolution has been how decisions have been made and implemented. In normal “work” you just have to make things as fast as possible and endlessly add features consequences-be-damned. Open source gets to be fundamentally the opposite. Traditionally one of the defining characteristics of Open Source is that “time is no object”. That is good design and implementation can be allowed the time to breathe and be excessively thought through. There is no rush or deadline. While there’s always conflict and drama I think there has been less so in Django than in most other projects as design decisions have been painstakingly threshed out and perfected in mailing lists, tickets, DEPs and forums over the months and years it takes to make them. The people inside see the drama but we’re in the news almost never compared to most projects in the same space. The point is that hypothetically it’s possible to try to make the best possible design decisions. In practice most projects don’t do this, but I think Django has demonstrated exemplary maturity in trying to pursue this ideal, and is regularly recognised for it.
The original founding team deserve full credit for instilling this culture and each successive group of stewards deserve credit for preserving it.
There have (and always will be) missteps. For example CBVs are such an obviously good idea on paper, but in practice people don’t think so. On the other hand Andrew Godwin’s implementation of migrations back in the day, that was completely re-writing South from scratch, was truly lovely, even though it was a battle to get to the point of having migrations at all. There’s the history around the db module, which pretty much everyone was too scared to touch after Malcolm died until there were some impressive breakthroughs in it during the “under the hood” sessions not long after DjangoGirls people started coming on board.
Django consciously has decided to be extremely considered in its adoption of change and this has been a great thing. Other frameworks have generally been more cavalier, while Django has been steady, careful and reliable. The other full-feature frameworks are kind of in decline, or have hurt themselves by too-much-change-too-fast, while Django has steadily slowly grown and is the trusty go-to tool for a certain kind of job.
Now moving forward I see focus on the very subtle things that make the framework nicer to use and understand, On just making the core capabilities better and more reliable and performant, and only very very carefully adding features.
In an age where so much quality degradation is occurring, it inspires hope that projects like Django can persist as beacons of high quality, held together by a small group and big community of thoughtful, caring individuals. Hopefully this is something we can continue for a long time into the future also!
You are part of the Code of Conduct working group, how is it to work with the working group? Do you have space available for new members? What does it require according to you?
Code of Conduct WGs are slightly niche and exposed to a certain kind of work and responsibility. Not to mention that respecting many sensitives and view-points is necessary. It also means having the guts to tell people “that’s not how it’s done here” when it needs to be said. Personally it’s a kind of work I’ve grown to be passionate about. I truly believe having a great culture is at the core of community (and really anything good) and can be a complex balancing act of competing factors and emotions. It’s certainly not the kind of thing everyone is into, but if you are, the WG is looking for more diversity, if nothing else it’s tending slightly older at the moment.
Having said that: Within all of the open source communities from local to international levels there’s always space for people who are willing to turn up and help!
Join your local community! Find the parts of community that “speak” to you. Maybe it’s starting a meetup, helping your local conference, running a DjangoGirls. Maybe it’s something engineer-related like finally adding something to an open source library that you’re into, adding some beginner docs somewhere, or engaging with Djangonaut Space. Maybe it’s something online like helping out in forum.djangoproject.com, Reddit or Discord.
As organisers we have this cheat code for finding new people to invite to help more, it’s called “looking for chair-stackers”, that is people who engage to help in the little ways, such as helping stack chairs at the end of an event or generally pack down, wipe up, carry boxes or put things away. Or online: people who go out of their way to try to understand and chip in to manage extra rules, or answer the unanswered thing that’s been sitting there for a while. Or people who just ask “can I help out with that?” when the organisers seem tired or stressed out. Having people around who help in these ways has huge value and has been the beginning of many people being involved in communities and making life-long friends and connections.
Now more than ever though, it’s so important to connect to your community. We are stronger, better and healthier when we are connected to and relied on by other people and we have others we can share our experiences with.
Particularly us computer people tend not to be as good with connecting with other people, but everyone should find their way to get out and connect! It’s sometimes hard but it’s always better.
You have organized many DjangoGirls in Australia, how did you start? Do you have any advice for someone who would like to organize a DjangoGirls event?
In 2014 I was living in Perth, Australia, where Russell Keith Magee is based and we had a budding Python/Django User Group. At one of the meetings news emerged about how Ola and Ola were running this thing called “DjangoGirls” at EuroPython in a few weeks. PyConAU was scheduled a couple of weeks after this. I was like, that’s a great idea, I can absolutely have a go at doing that and emailed them immediately asking if I could copy their materials and plan. We pulled it together with an amazing bunch of people and I think this was technically the 2nd DjangoGirls event ever. In the following years I’ve been involved in many more, including the first North American DjangoGirls. From our Perth series of events a successful organisation was spun off called SheCodes.
In the more-than-a-decade since then the world has changed so much! Particularly in the tech world. I would say specifically for DjangoGirls events, they are very region specific. My first advice for organising an event in your region is to see if there’s been one previously and reach out to the event organisers, or at least the nearest organisers – I think these days there are few places on earth that haven’t had a DjangoGirls event nearish-by. The resources on the website are actually great for getting going and the international DjangoGirls team are lovely, but also always looking for more help.
Where I live now, back in the capital, Canberra, we are very well supported for education services. We held a DjangoGirls event a couple of years ago, but for the attendees what emerged was that what we really wanted was just to connect with other technical women.
Now what has been very successful for us is an ongoing PyLadies/Women’s Software group who meet up regularly and talk about things that matter to our experience. We use the “lean-coffee” model and it’s been unexpectedly functional. This has been one of the best groups I’ve ever been in with a range of technical women regularly sharing our weird and statistically unusual experiences together, it feeds the soul, and is strongly recommended if you don’t participate in a group like this already.
Is there anything else you’d like to say?
A final shout out to the original leaders of the Django community, for me personally Russell, Jeff, Jacob, Andrew and Baptiste in particular, but everyone who has persisted over the years in just turning up over the long haul and keeping our part of the world as beautiful as can be. My friends Dave, Matt and Jonah. Thibaud is a great president right now. Rarely is there a dedicated Django person who is not absolutely delightful and I feel both proud and honoured to be part of this community. A big thank you to everyone (especially you Sarah! And all the Sarahs, Natalias, Lillys and Olas) who help to make Django what it is.
Thank you for doing the interview, Elena !
From The Django weblog at 2025-06-10 09:06:32
Django bugfix releases issued: 5.2.3, 5.1.11, and 4.2.23
Following the June 4, 2025 security release, the Django team is issuing releases for Django 5.2.3, Django 5.1.11, and Django 4.2.23 to complete mitigation for CVE-2025-48432: Potential log injection via unescaped request path (full description).
These follow-up releases migrate remaining response logging paths to a safer logging implementation, ensuring that all untrusted input is properly escaped before being written to logs. This update does not introduce a new CVE but strengthens the original fix.
We encourage all users of Django to upgrade as soon as possible.
Affected supported versions
- Django main
- Django 5.2
- Django 5.1
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.2, 5.1, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2025-48432: Potential log injection via unescaped request path
- On the main branch
- On the 5.2 branch
- On the 5.1 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.2.3 (download Django 5.2.3 | 5.2.3 checksums)
- Django 5.1.11 (download Django 5.1.11 | 5.1.11 checksums)
- Django 4.2.23 (download Django 4.2.23 | 4.2.23 checksums)
The PGP key ID used for this release is : 3955B19851EA96EF
From The Django weblog at 2025-06-09 18:00:00
DSF calls for applicants for a Django Fellow
The Django Software Foundation is announcing a call for Django Fellow applications. A Django Fellow is a contractor, paid by the Django Software Foundation, who dedicates time to maintain the Django framework.
The Fellowship program was started in 2014 as a way to dedicate high-quality and consistent resources to the maintenance of Django. The Django Software Foundation currently supports two Fellows –Natalia Bidart and Sarah Boyce– and has approved funding for a new full-time Fellow. This position will be initially for a period of one year, but may be extended depending on fundraising levels.
Beyond keeping Django running, a fellow is a representative of Django itself. They embody the welcoming culture of Django and aid the community to progress the framework. Fellows are often called upon to speak at Django conferences and events.
They are also usually leading Django Sprints occurring in conferences or other setups. Hence a Django Fellow often engages in both informal and formal mentorship.
Responsibilities
Fellow duties include (but are not limited to):
- Monitoring security reports and ensuring security issues are acknowledged and responded to promptly
- Fixing release blockers and helping to backport fixes to these and security issues
- Ensure timely releases including being a release manager for a new version of Django
- Triaging tickets on Trac
- Reviewing and merging pull requests
- Answering contributor questions on the Forum
- Helping new Django contributors land patches and learn our philosophy
Requirements
A Django fellow reviews a very large amount of Django contributions. This requires knowledge in every aspect of web development that the Django framework touches. This turns out to be an intimidatingly-large list of technical topics, many of which are listed below. It’s not our expectation that you come into the job knowing everything on this list! We hope you’ll have solid experience in a few of these topics, particularly some of the “core” technologies important to Django (Python, relational databases, HTTP). But we fully expect that you’ll learn most of this on the job. A willingness to learn, and a demonstrated history of doing so, is more important than comprehensive knowledge.
The technical topics you can expect to work on includes (and is not limited to):
- SQL and Databases: SQLite, MySQL, Postgres, Oracle
- Technical Documentation
- Javascript
- CSS
- Semantic HTML
- Accessibility
- UI/UX design (Web and CLI)
- Python async
- Python features (and versions), compatibility matrix, etc.
- Everything around HTTP
- Security best practices
There are also:
- Complex processes which need adhering to
- Multiple discussions which need opinions and direction
- Requirements for both formal and informal mentorship
And required professional skills such as:
- Conflict resolution
- Time management and prioritization expertise
- Ability to focus in short periods of time and do substantial context switches
- Self-awareness to recognize their own limits and reach out for help
- Relationship-building and coordination with Django teams, working groups, and potentially external parties.
- Tenacity, patience, compassion and empathy are essential
Therefore a Django Fellow requires the skills and knowledge of a senior generalist engineer with extensive experience in Python and Django. Open source experience, especially in contributing to Django, is a big plus.
Being a Django contributor isn't a prerequisite for this position — we can help get you up to speed. We'll consider applications from anyone with a proven history of working with either the Django community or another similar open-source community. While no geographical location is required, we have a slight preference for timezones between around -8 and +3 UTC to allow for better working hours to overlap the current fellows.
If you're interested in applying for the position, please email us at fellowship-committee@djangoproject.com describing why you would be a good fit along with details of your relevant experience and community involvement. Lastly, please include at least one recommendation.
The current hourly rate for a fellow is $82.26 USD.
Applicants will be evaluated based on the following criteria:
- Details of Django and/or other open-source contributions
- Details of community support in general
- Understanding of the position
- Clarity, formality, and precision of communications
- Strength of recommendation(s)
Applications will be open until midnight AoE, 1 July, 2025, with the expectation that the successful candidate will start around August 1, 2025.
From The Django weblog at 2025-06-04 12:00:00
Django security releases issued: 5.2.2, 5.1.10, and 4.2.22
In accordance with our security release policy, the Django team is issuing releases for Django 5.2.2, Django 5.1.10, and Django 4.2.22. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2025-48432: Potential log injection via unescaped request path
Internal HTTP response logging used request.path directly, allowing control characters (e.g. newlines or ANSI escape sequences) to be written unescaped into logs. This could enable log injection or forgery, letting attackers manipulate log appearance or structure, especially in logs processed by external systems or viewed in terminals.
Although this does not directly impact Django's security model, it poses risks when logs are consumed or interpreted by other tools. To fix this, the internal django.utils.log.log_response() function now escapes all positional formatting arguments using a safe encoding.
Thanks to Seokchan Yoon (https://ch4n3.kr/) for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.2
- Django 5.1
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.2, 5.1, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2025-48432: Potential log injection via unescaped request path
- On the main branch
- On the 5.2 branch
- On the 5.1 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.2.2 (download Django 5.2.2 | 5.2.2 checksums)
- Django 5.1.10 (download Django 5.1.10 | 5.1.10 checksums)
- Django 4.2.22 (download Django 4.2.22 | 4.2.22 checksums)
The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum. Please see our security policies for further information.
From The Django weblog at 2025-05-22 10:12:02
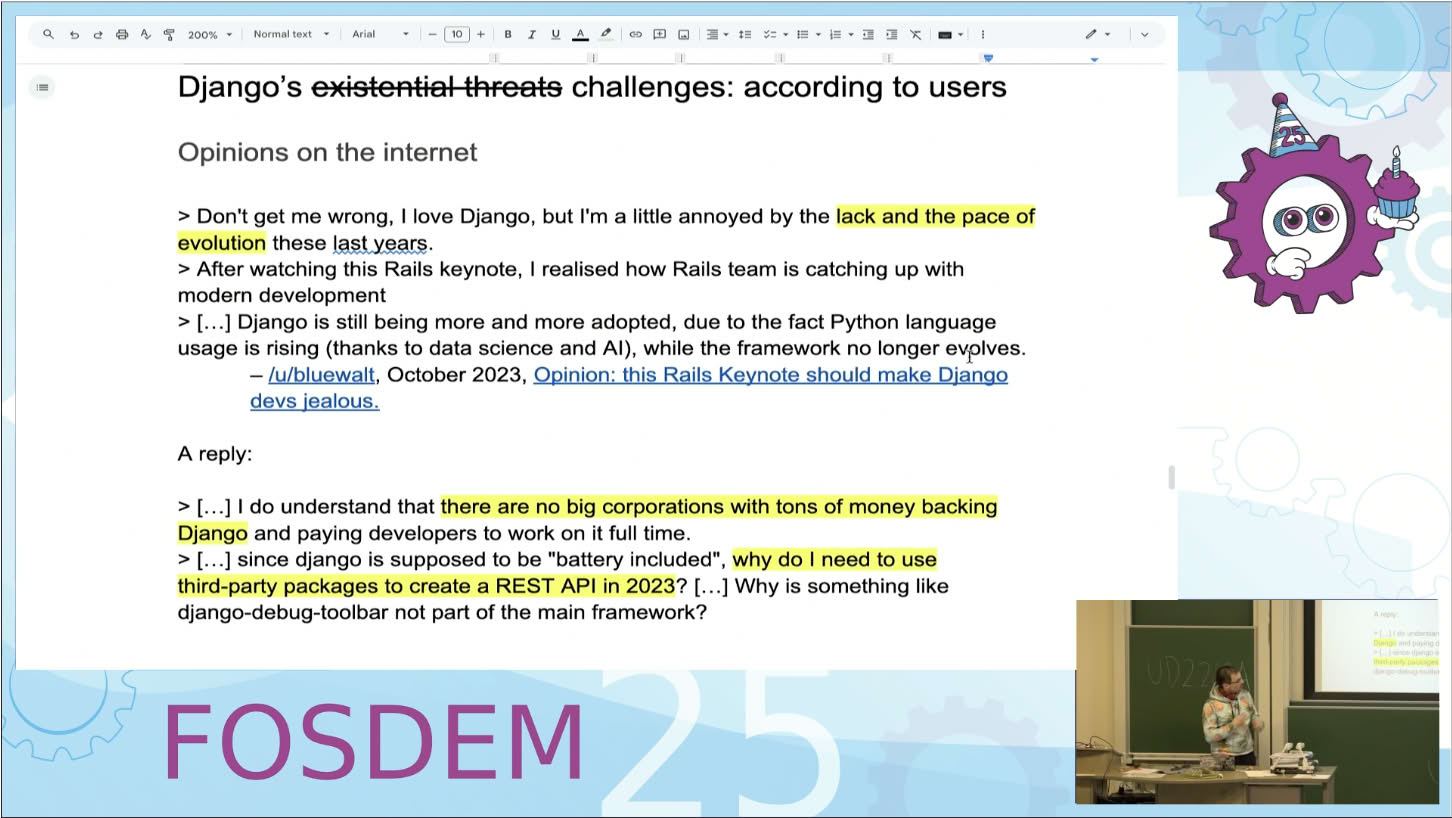
Why, in 2025, do we still need a 3rd party app to write a REST API with Django?
The question was asked to the president of the DSF this year at FOSDEM, after his talk. And it is clearly a legitimate one!
But… is it True? Do we actually need a 3rd party app to write an API with Django?
In a lot of cases, when you require a complex and full-featured API, I would recommend you do use one. Django REST Framework and Django Ninja being very sound choices with a bunch of nifty things you might need in a bigger project.
But… what if what you need is a simple REST API that does CRUD? Do you really need a 3rd party app to do that?
Let's try not to!
Let's first ask what is a REST API in the context of this article. Let's limit ourselves to building this:
- a URL that answers to
GETrequests with a list of records of a single model type POST-ing to that same URL should create a new record- a second URL with the primary key of a record tagged to the end. When
GET-ing that URL, one should receive only that single record, in a similar format as in the list PUT-ing data to that URL should update the record and return that record with updated valuesDELETE-ing to that same URL should delete the record- everything should be achieved using JSON
Listing records from a model
Chances are you have heard of generic class-based views (CBVs) in Django, the one that comes to mind when it comes to listing records is the built-in django.views.generic.ListView.
ListView extends 2 other classes, BaseListView and MultipleObjectTemplateResponseMixin. Since we want to build an API, we clearly don't need to extend anything template-related. Looking at what BaseListView provides, one can notice the only thing really missing there is a render_to_response method. And this is going to be the case for most of the other base classes.
This sets our starting point!
The type of response we want to render is a json response and Django already provides one. So let's build a JsonViewMixin that looks like this for now:
class JsonViewMixin(View):
response_class = JsonResponse
content_type = 'application/json'
def render_to_response(self, context, **response_kwargs):
response_kwargs.setdefault("content_type", self.content_type)
return self.response_class(context, **response_kwargs)
The next thing we have to tackle is that the context returned by BaseListView's get_context_data returns much more data than what we strictly need for this article. Also the list of records returned is not serialized to json.
Serializers for mutliple formats already exist in Django core (see django.core.serializers) but I will go a different route here. There is another way to serialize data in Django that you are likely familiar with but is not labelled as clearly: forms.
Forms are used in regular views to serialize models to simple types, understandable by HTML forms (mostly text) and vice-versa. This is very close to what we need, since json is also mostly text-based.
To start with, using forms as serializers requires creating a new form instance for each record in the list we want to return.
Let's add that to the mixin!
def serialize_many(self, obj_list):
return [self.serialize_one(obj) for obj in obj_list]
def serialize_one(self, obj)
form = self.get_form_for_object(obj)
serialized = form.initial
serialized['pk'] = obj.pk # forms strip pk's from their data
return serialized
def get_form_for_object(self, obj):
form_class = self.get_form_class()
kwargs = self.get_form_kwargs()
kwargs['instance'] = obj
return form_class(**kwargs)
Why use forms?
ModelForms are a built-in and robust Django tool that are built around the idea of handling the transition between Model fields and simple (and also JSON-serializable) types (mostly text and numbers). Which is exactly what we want from (de-)serializers in a lot of cases.
If you need to (de-)serialize a custom field type, Django documents creating a custom form field and this covered in various places like StackOverflow.
Moving on to our first View
Now that we have a tool to serialize the records list returned by BaseListView let's write the first version of JsonListView. As I alluded to earlier, we need to strip down what is returned from get_context_data.
class JsonListView(JsonViewMixin, BaseListView):
def get_context_data(self, **kwargs):
context = super().get_context_data(**kwargs)
# wrapping this in a dict for security reasons
return {
'results': self.serialize_many(context['object_list'])
}
This won't work yet because get_form_class that I used in the JsonViewMixin is only provided by classes that descend from FormMixin. Since we want this view to handle both listing and creating records, let's go and fix that in the next section!
1 down, 3 to go: Adding records
First thing first, let's rebrand JsonListView and make it inherit from BaseCreateView.
class JsonListCreateView(JsonViewMixin, BaseCreateView, BaseListView):
Form creation and validation will be handled automatically by Django!
Almost…
The first concern will be with populating the form with POST data. While Django does this for you when dealing with URL encoded or multipart form data, it does not (yet) handle json-encoded POST content.
But this can be handled by taking advantage of the modularity of Django's generic class-based-views and overwritting get_form_kwargs.
Let's address this (in a naïve way) within the mixin as it will be applicable to any JSON view:
def get_form_kwargs(self):
kwargs = super().get_form_kwargs()
if (
len(kwargs.get("data", {})) == 0
and self.request.content_type == "application/json"
and len(self.request.body)
):
# The request has a JSON body that we did not decode
kwargs["data"] = json.loads(self.request.body)
return kwargs
An issue that could arise here is that a JSONDecoderError could be triggered. get_form_kwargs does not return a response so I don't think it is the right place to handle the exception.
The post method does return a response, let's wrap the original one with a try/except (still in the mixin):
def post(self, request, *args, **kwargs):
try:
return super().post(request, *args, **kwargs)
except json.decoder.JSONDecodeError as e:
return self.response_class(
{"error": f"json decode error: {e.msg}"},
status=HTTPStatus.UNSUPPORTED_MEDIA_TYPE,
)
Speaking of returning responses, the BaseCreateView class is built around HTML principles and its form_valid and get methods are both designed to render a form (via get_context_data).
In the case of our REST API, the "create" part of things should not be involved with GET requests.
Furthermore the reply to an invalid form submission should only comprise of an error (status + message) and should not require anything provided by get_context_data.
Still, in regards to form validation, a valid form should not result in a redirect (behaviour of BaseCreateView) but rather in a 201 response optionally containing the representation of the created record.
The form handling part is generic enough to put it in the mixin itself.
The behaviour of GET is specific to the list/create view though.
Let's write the code accordingly:
class JsonViewMixin(View):
...
def form_invalid(self, form):
return self.response_class(
{'errors': form.errors},
status=HTTPStatus.UNPROCESSABLE_CONTENT
)
def form_valid(self, form):
self.object = form.save()
context = self.serialize_one(self.object)
return self.response_class(
context,
status=HTTPStatus.CREATED
)
class JsonListCreateView(JsonViewMixin, BaseCreateView, BaseListView):
...
def get_context_data(self, **kwargs):
# Explicitly point to BaseListView instead of `super()`
# to prevent actions taken by
# BaseCreateView's implementation of `get_context_data`
context = BaseListView.get_context_data(self, **kwargs)
return {
'results': self.serialize_many(context['object_list'])
}
Halfway there!
That was everything needed to handle the create and list portions of our CRUD REST application. Now we can move on to the read, update, delete part. We'll do that in a second View class as it requires a slightly different URL, one that contains the pk of the resource.
Both read and update functionalities are provided by Django BaseUpdateView but, as with the create/list view, the major difference in this case will be that we need a much simpler context.
class JsonReadUpdateView(JsonViewMixin, BaseUpdateView):
def get_context_data(self, **kwargs):
return self.serialize_one(self.object)
That's it!!!
Well, almost…
BaseUpdateView is wired to answer to POST requests for updating a record while REST good practices want us to use PUT instead. The fix for this is to raise an error in reply to POST calls while directing PUTs to the parent's post implementation.
def post(self, request, *args, **kwargs):
return self.response_class(status=HTTPStatus.METHOD_NOT_ALLOWED)
def put(self, request, *args, **kwargs):
return super().post(self, request, *args, **kwargs)
One more fix…
Our mixin implementation returns a 201 on form_valid. In case of any view which is not creating a record, this should be 200. Here are the necessary changes:
class JsonViewMixin(View):
form_valid_status = HTTPStatus.OK # new property
def form_valid(self, form):
self.object = form.save()
context = self.serialize_one(self.object)
return self.response_class(
context, status=self.form_valid_status # use the new property
)
...
class JsonListCreateView(JsonViewMixin, BaseCreateView, BaseListView):
form_valid_status = HTTPStatus.CREATED # override in case of creation
Why PUT and not PATCH?
BaseUpdateView builds a form that expects all fields to be filled. Non-present fields would be reset to empty on the existing record for partial updates.
I'll leave it as an exercise to the reader to override that behaviour in case of a PATCH request in order to "pre-fill the form" with existing values, maybe by using the form's initial property… 😉
Finally…
The last bit of logic we have to implement is for deleting objects. Most of the code from Django's BaseDeleteView is related to creating and validating a form for confirming the user's intend on deleting the resource. This is usually not the expected behaviour for a REST API, this part being handled by whatever is calling the API.
Furthermore, it doesn't implement a delete method. In the HTML world of Django's BaseDeleteView, everything is done using GET and POST. So we are (mostly) on our own for this last part.
We can still leverage the get_object implementation provided by BaseUpdateView though.
Here is what implementing the delete operation for our read/update/delete view looks like:
class JsonReadUpdateDeleteView(JsonViewMixin, BaseUpdateView): # name changed
...
def delete(self, request, *args, **kwargs):
self.get_object().delete()
# data is required by JsonResponse
return self.response_class(data={}, status=HTTPStatus.NO_CONTENT)
Conclusion
This implementation is basic and clearly naïve. But it gets the job done!
And this can all be done by leveraging Django-provided tools and mechanisms, mainly using Django's generic CBVs.
Generic class-based views have been built in such a modular fashion that implementing one's own mini REST framework can be done in less than 100 lines of code.
A non-negligible advantage of such an approach is that most libraries written to work with Django's generic CBVs are also likely to work with this implementation.
This rather simple approach can certainly be improved (handling exceptions in delete… anyone?) and is clearly not going to cover everybody's use cases. And it most likely misses handling a bunch of edge cases!
And if you are building a large REST API, I would say you are probably still better off using a 3rd party library but… to me, the answer to the question “Why do you need a 3rd party application to write a simple REST application with Django?” is: "You don’t"
If you enjoyed this article, read more from Emma on Emma has a blog, which is where this piece was from. Or watch the FOSDEM talk that Emma reacts to:
From The Django weblog at 2025-05-16 12:54:21
Our Google Summer of Code 2025 contributors
We’re excited to introduce our Google Summer of Code 2025 contributors!

These amazing folks will be working on impactful projects that will shape Django’s future.\ Meet the contributors 👇
A. Rafey Khan
Project: Django Admin – Add Keyboard Shortcuts & Command Palette. Mentors: Tom Carrick, Apoorv Garg
Rafey will work on making Django Admin faster and more accessible through keyboard-driven workflows. Excited to see this land!
Farhan Ali Raza
Project: Bring django-template-partials into core. Mentor: Carlton Gibson
Farhan will be enhancing Django’s template system by adding first-class support for partials—making componentized templates easier than ever.\
Saurabh K
Project: Automate processes within Django’s contribution workflow. Mentor: Lily Foote
Saurabh will work on streamlining how contributors interact with Django repo—automating repetitive tasks and improving dev experience for all. \ A huge shoutout to our mentors (and Org Admin Bhuvnesh Sharma) and the broader Django community for supporting these contributors! 💚\ \ Let’s make this a summer of learning, building, and collaboration.
From The Django weblog at 2025-05-15 15:00:00
Our new accessibility statement
Happy Global Accessibility Awareness Day! We thought this would be a fitting occasion to announce our brand new Django accessibility statement 🎉
Did you know that according to the WebAIM Million survey, 94.6% of sites have easily-detectable accessibility issues? We all need to work together to build a more inclusive web (also check out our diversity statement if you haven’t already!). There are accessibility gaps in Django itself too. This statement improves transparency, and clearly states our intentions. And we hope it encourages our community and the industry at large to more widely consider accessibility.
How to use this statement
Read it, share it with your friends, or in a procurement context!
- Use it to understand where there are gaps in Django that need to be addressed on projects.
- And opportunities to contribute to Django and related projects ❤️
- Factor it into legal compliance. For example with the European Accessibility Act. Starting June 2025, accessibility becomes a legal requirement for large swaths of the private sector in the European Union.
- Share it with venues for Django events to demonstrate the importance of accessibility for their competitiveness.
How you can help
Take a moment to provide any feedback you might have about the statement on the Django Forum. Let us know if you would prefer additional reporting like an ATAG audit, or VPAT, ACR, or any other acronym. Let us know if you’d like to contribute to the accessibility of the Django community! 🫶
From The Django weblog at 2025-05-15 05:55:48

We had a blast at DjangoCon Europe 2025, and hope you did too! Events like this are essential for our community, delighting both first-timers and seasoned Djangonauts with insights, good vibes, and all-around inspiration. This year’s conference brought together brilliant minds from all corners of the globe. And featured early celebrations of Django’s 20th birthday! ⭐️🎂🎉
After launching in 2005, Django turns 20 in 2025, and the conference was a great occasion for our community to celebrate this. And work on the sustainability of the project together.
We need more code reviews
Our Django Fellow Sarah Boyce kicked off the conference with a call for more contributions – of the reviewing kind. In her words,
Django needs your help. Every day, contributors submit pull requests and update existing PRs, but there aren't enough reviewers to keep up. Learn why Django needs more reviewers and how you can help get changes merged into core.

We need more fundraising
Our Vice President Sarah Abderemane got on stage to encourage more financial support of Django from attendees, showcasing how simple it is to donate to the project (get your boss to do it!). We have ambitious plans for 2025, which will require us to grow the Foundation’s budget accordingly.

Annual meeting of DSF Members
Our Board members Tom Carrick, Thibaud Colas, Sarah Abderemane, and Paolo Melchiorre were at the conference to organize a meeting of Members of the Django Software Foundation. This was a good occasion to discuss long-standing topics, and issues of the moment, such as:
- Diversity, equity and inclusion. Did you know we recently got awarded the CHAOSS DEI bronze badge? We need to keep the momentum in this area.
- Management of the Membership at the Foundation. With different visions on how much the membership is a recognition or a commitment (or both). There was interest in particular in sharing more calls to action with members.
- Content of the website. A long-standing area for improvement (which we’re working on!)
All in all this was a good opportunity for further transparency, and to find people who might be interested in contributing to those areas of our work in the future.

Birthday celebrations
There was a cake (well, three!). Candles to blow out. And all-around great vibes and smiles, with people taking pictures and enjoying specially-made Django stickers!



Up next
We have a lot more events coming up this year where the Foundation will be present, and bringing celebrations of Django’s 20th birthday!
PyCon US 2025
It’s on, now! And we’re present, with a booth. Come say hi! There will be Django stickers available:

PyCon Italia 2025
Some of the PyCon Italia team was there at DjangoCon Europe to hype up their event – and we’ll definitely be there in Bologna! They promised better coffee 👀, and this will have to be independently verified. Check out their Djangonauts at PyCon Italia event.

EuroPython 2025
We got to meet up with some of the EuroPython crew at DjangoCon Europe too, and we’ll definitely be there at the conference too, as one of their EuroPython community partners 💚. There may well be birthday cake there too, get your tickets!

Django events
And if you haven’t already, be sure to check out our next flagship Django events!
- DjangoCon Africa 2025, in Arusha, Tanzania 🇹🇿 in August.
- DjangoCon US 2025, in Chicago, USA 🇺🇸 in September.
Thank you to everyone who joined us at DjangoCon Europe, and thank you to the team behind the conference in particular ❤️. DjangoCon Europe continues to show the strength and warmth of our community, proving that the best part of Django is truly the people. See you at the next one!
From The Django weblog at 2025-05-14 13:00:00
DSF member of the month - Simon Charette
For May 2025, we welcome Simon Charette as our DSF member of the month! ⭐

Simon Charette is a longtime Django contributor and community member. He served on the Django 5.x Steering Council and is part of the Security team and the Triage and Review team. He has been a DSF member since November 2014.
You can learn more about Simon by visiting Simon's GitHub Profile.
Let’s spend some time getting to know Simon better!
Can you tell us a little about yourself (hobbies, education, etc)
My name is Simon Charette and I'm based in Montréal. I've been contributing to Django for over a decade mainly to the ORM and I have a background in software engineering and mathematics. I work as a principal backend engineer at Zapier where we use Python and Django to power many of our backend services. Outside of Django and work I like to spend time cycling around the world, traveling with my partner, and playing ultimate frisbee.
Out of curiosity, your GitHub profile picture appears to be a Frisbee, is it correct? If so, have you been playing for a long time?
I've been playing ultimate frisbee since college which is around the time I started contributing to Django. It has been a huge part of my life since then as I made many friends and met my partner playing through the years. My commitment to ultimate frisbee can be reflected in my volume of contributions over the past decade as it requires more of my time during certain periods of the year. It also explains why I wasn't able to attend most DjangoCon in spring and fall as this is usually a pretty busy time for me. I took part in the world championships twice and I played in the UFA for about 5 years before retiring three years ago. Nowadays I still play but at a lower intensity level and I am focused on giving back to the community through coaching.
How did you start using Django?
Back in college I was working part time for a web agency that had an in house PHP framework and was trying to determine which tech stack and framework they should migrate to in order to ease onboarding of their developers and reduce their maintenance costs. I was tasked, with another member of the team, to identify potential candidates and despite my lack of familiarity with Python at the time we ended up choosing Django over PHP's Symphony mainly because of its spectacular documentation and third-party app ecosystem.
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
If I had magical powers I'd invent Python ergonomics to elegantly address the function coloring problem so it's easier for Django to be adapted to an async-ready world. I'm hopeful that the recent development on the GIL removal in Python 3.13+ will result a renewed interest in the usage of threading, which Django is well equipped to take advantage of, over the systematic usage of an event loop to deal with web serving workloads as the async world comes with a lot of often overlooked drawbacks.
What projects are you working on now?
I have a few Django related projects I'm working on mainly relating to ORM improvements (deprecating extra, better usage of RETURNING when available) but the main one has been a tool to keep track of the SQL generated by the Django test suite over time to more easily identity unintended changes that still pass the test suite. My goal with this project is to have a CI invokable command that would run the full Django test suite and provide a set of tests that generated different SQL compared to the target branch so its much easier to identify unintended side effects when making invasive changes to the ORM.
Which Django libraries are your favorite (core or 3rd party)?
- DRF
- django-filter
django-seal(shameless plug)
What are the top three things in Django that you like?
- The people
- The ORM, unsurprisingly
- The many entry points the framework provides to allow very powerful third-party apps to be used together
You've contributed significantly to improving the Django ORM. What do you believe is the next big challenge for Django ORM, and how do you envision it evolving in the coming years?
The ORM's expression interface is already very powerful but there are effectively some remaining rough edges. I believe that adding generalized support for composite virtual fields (a field composed of other fields) could solve many problems we currently face with how relationships are expressed between models as we currently lack a way to describe an expression that can return tuples of values internally. If we had this building block, adding a way to express and compose table expressions (CTE, subquery pushdown, aggregation through subqueries) would be much easier to implement without denaturing the ORM by turning it into a low level query builder. Many of these things are possible today (e.g. django-cte) but they require a lot of SQL compilation and ORM knowledge and can hardly be composed together.
How did you start to contribute to the ORM? What would be the advice you have for someone interested to contribute to this field?
I started small by fixing a few issues that I cared about and by taking the time to read through Trac, mailing lists, and git-blame for changes in the area that were breaking tests as attempted to make changes. One thing that greatly helps in onboarding on the ORM is to at least have some good SQL fundamentals. When I first started I already had written a MSSQL ORM in PHP which helped me at least understand the idea behind the generation of SQL from a higher level abstraction. Nowadays there are tons of resources out there to help you get started on understand how things are organized but I would suggest this particular video where I attempt to walk through the different phases of SQL generation.
Is there anything else you’d like to say?
It has been a pleasure to be able to be part of this community for so long and I'd like to personally thank Claude Paroz for initially getting me interested in contributing seriously to the project.
Thank you for doing the interview, Simon !
From The Django weblog at 2025-05-07 15:00:00
Django security releases issued: 5.2.1, 5.1.9 and 4.2.21
In accordance with our security release policy, the Django team is issuing releases for Django 5.2.1, Django 5.1.9 and Django 4.2.21. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2025-32873: Denial-of-service possibility in strip_tags()
django.utils.html.strip_tags() would be slow to evaluate certain inputs containing large sequences of incomplete HTML tags. This function is used to implement the striptags template filter, which was thus also vulnerable. django.utils.html.strip_tags() now raises a SuspiciousOperation exception if it encounters an unusually large number of unclosed opening tags.
Thanks to Elias Myllymäki for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.2
- Django 5.1
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.2, 5.1, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2025-32873: Denial-of-service possibility in strip_tags()
- On the main branch
- On the 5.2 branch
- On the 5.1 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.2.1 (download Django 5.2.1 | 5.2.1 checksums)
- Django 5.1.9 (download Django 5.1.9 | 5.1.9 checksums)
- Django 4.2.21 (download Django 4.2.21 | 4.2.21 checksums)
The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum. Please see our security policies for further information.
From The Django weblog at 2025-04-26 15:58:08
New-features github repo and project
New Feature Request/Proposal Process with GitHub Repository
Django is experimenting with a new GitHub repository specifically designed to manage feature ideas and their progression. This is a significant shift away from the previous process of posting those to the forum.
Introducing the Django Features Repository
The Django Steering Council has launched a new GitHub repository at https://github.com/django/new-features dedicated to managing feature requests and ideas. This repository works in conjunction with a GitHub project to provide more efficient tracking of feature ideas as they move through various stages of consideration.
Why This Matters for Django Developers
This new approach aims to addresses several challenges the Django community has faced with feature requests:
- Community involvement: Clear guidelines on how to participate in feature discussions
- Structured workflow: A defined path from idea to implementation
- Better resource allocation: Prioritization based on community support and feasibility
The New Feature Process Flow
The process follows a workflow with several key decision points:
- New Idea Submission: Community members submit feature ideas as GitHub issues
- Community Support Phase: The community reacts with emojis and comments to express support or concerns
- Evaluation for Core Inclusion: The Steering Council determines if the feature belongs in Django core or whether it is more appropriate as a 3rd party package
- Implementation Planning: Through an expedited DEP (Django Enhancement Proposal) process
How to Participate
Have a Feature Idea?
If you have an idea for improving Django, the process starts by creating an issue in the new repository. Before submitting, review the new feature process documentation to understand what to expect.
Want to Help Shape Django's Future?
There are three key areas where community involvement is needed:
- Community Support Assessment: Review open tickets and share your support using emoji reactions
- 👍 For features you would use
- 👎 For features that might cause problems
- 😕 For features you're indifferent about
-
🎉 For easy wins
-
Core Evaluation: Help determine whether features should exist in Django core or as third-party packages
-
Implementation Volunteering: Assist with implementing, reviewing implementations, and maintenance of approved features
Benefits for the Django Community
We believe this new process can help with:
- Clearer communication: Understanding where a feature stands in the process
- More efficient feature development: Resources directed to features with demonstrated community support
- Better separation of concerns: Distinguishing between features that belong in core versus those better suited as third-party packages
- Reduced friction: Expedited processes for smaller feature requests
Providing Feedback
If you have thoughts about the new process itself, we'd love to get feedback through the Django Forum.
Conclusion
The experimental new feature repository represents is one of several steps Django is taking in order to try and improve the contributor experience journey. By providing a structured, transparent process for feature requests, Django aims to better serve its community while maintaining the framework's quality and sustainability.
For developers interested in contributing to Django or proposing new features, this new system should provide clearer expectations while making it easier to locate and participate in the discussion around a specific feature.
Check out the repository at https://github.com/django/new-features to learn more and start participating in this new adventure.
From The Django weblog at 2025-04-18 15:19:46
Django Admin Theme Roundup 2025
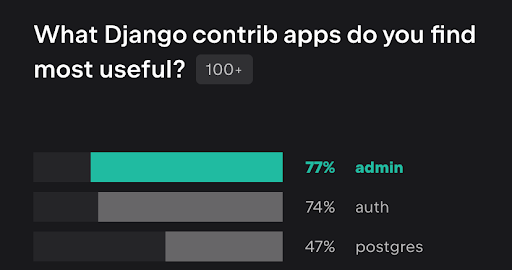
One of Django’s most appreciated features is the built-in admin functionality. In fact, it was ranked as the most useful contrib app in the 2023 Django developer survey.
With a few lines of code, Django automatically generates an administrative interface to add, update, and edit objects in your database. While it's not meant to replace a full-featured frontend, the admin makes rapid prototyping possible and provides a lot of functionality out of the box.
However, the admin’s focus is not on a flashy user interface and some people have found it to be a little plain – some have even called it ugly! But fortunately, like all Django applications, the admin’s CSS and HTML templates can be overridden and tweaked. Here are a few projects which have done that, and are recently updated as of early 2025.
Chime in on the Django forum thread here with your favorite Django admin theme or if I missed any other options!
Note that these packages are listed in the order of the “easiest” integration to the hardest. However, the later libraries also tend to provide more features.
Dracula
A dark (and light) theme for the Django Admin based on the very popular Dracula which has themes for 400+ applications. This library is a quick win to give the admin a bit of pizazz without requiring much setup or changing the default admin functionality.
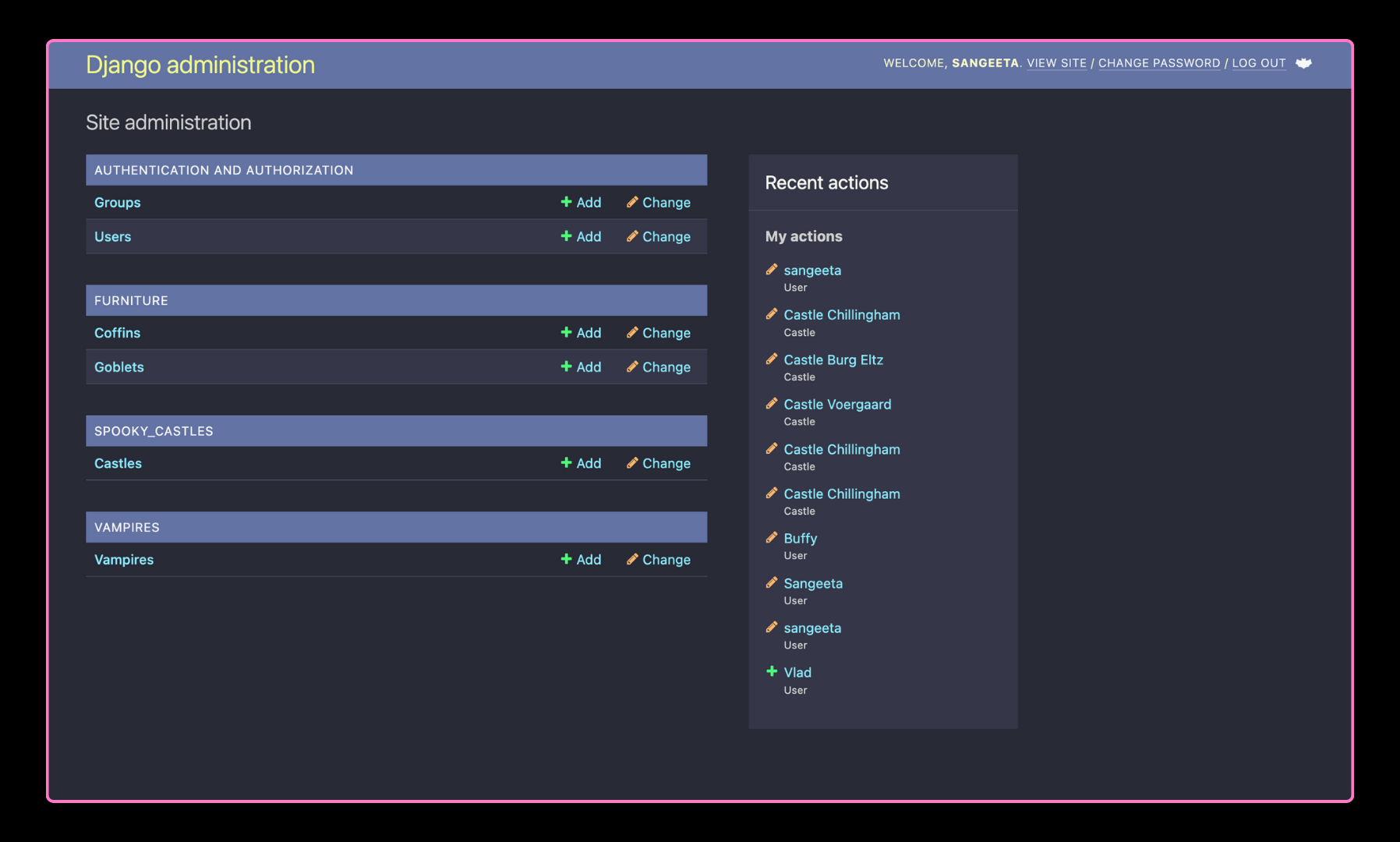
Django Daisy
Django Daisy is a responsive admin built with DaisyUI and TailwindCSS. Application icons can be added by utilizing Font Awesome. Very minimal (and completely optional!) configuration.
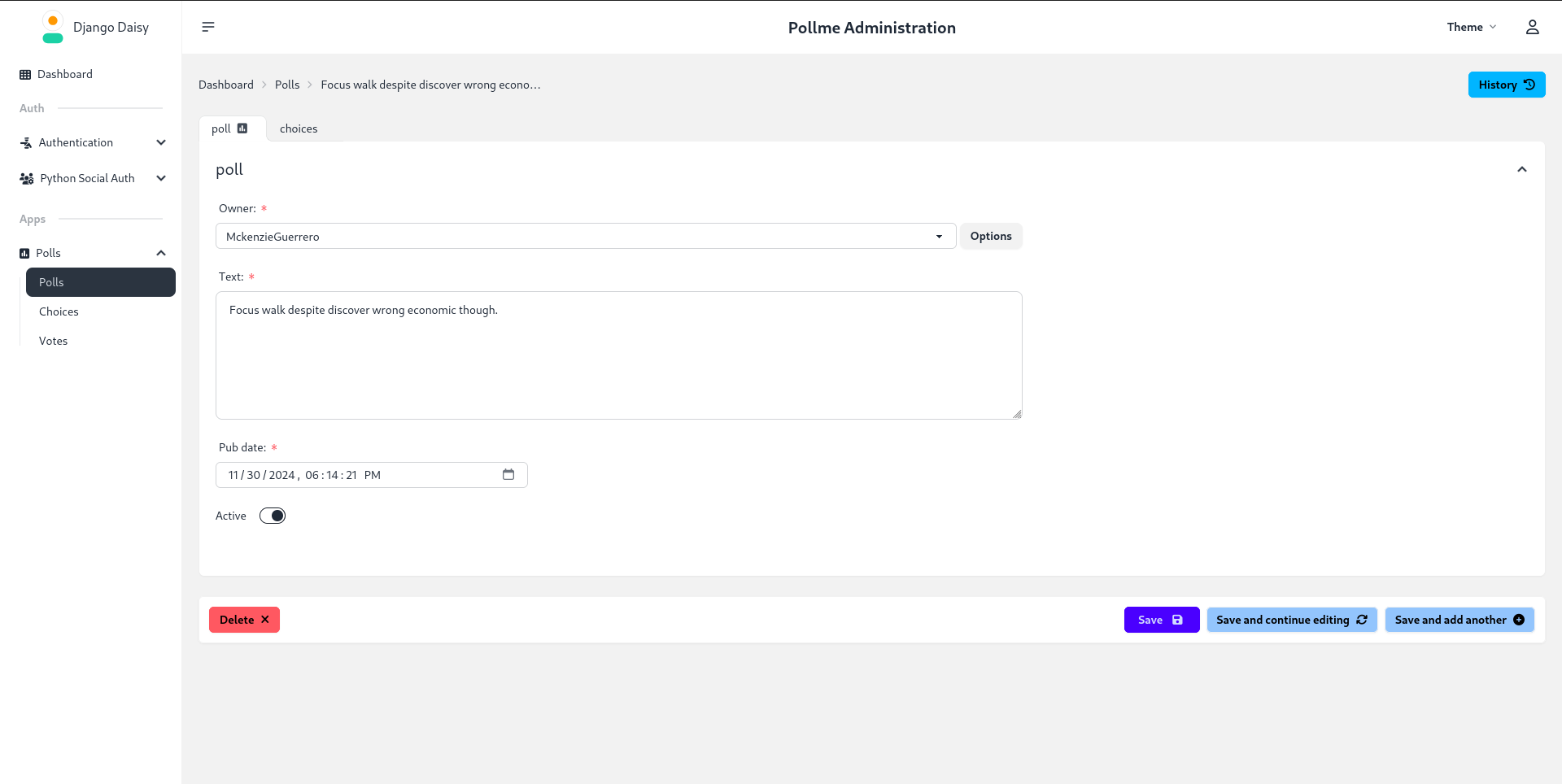
django-jazzmin
A drop-in theme for the Django admin that utilises AdminLTE 3.2 & Bootstrap 5. All of the configuration is optional which means the installation is very straight-forward. However, it also includes the ability to create custom menus, convert all pop-ups to modals, and a slick UI customizer. django-jazzmin also includes a wide selection of built-in themes.
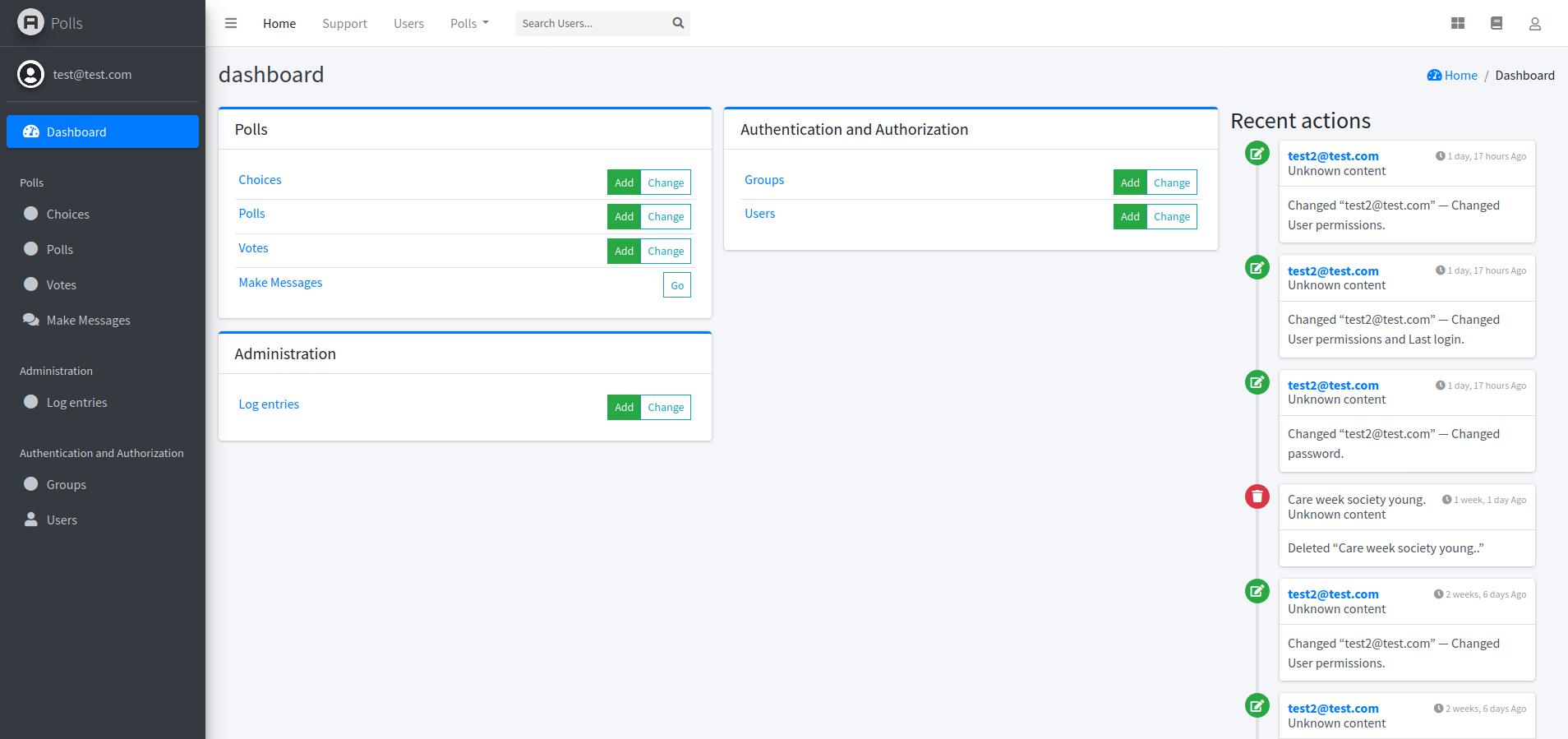
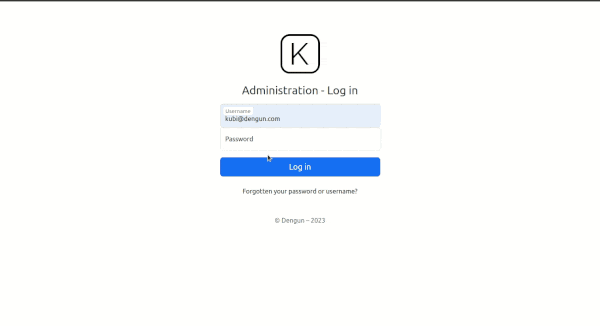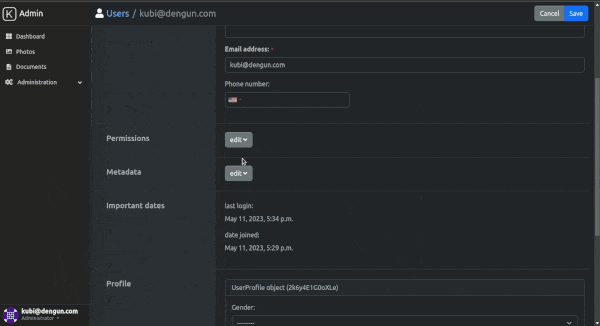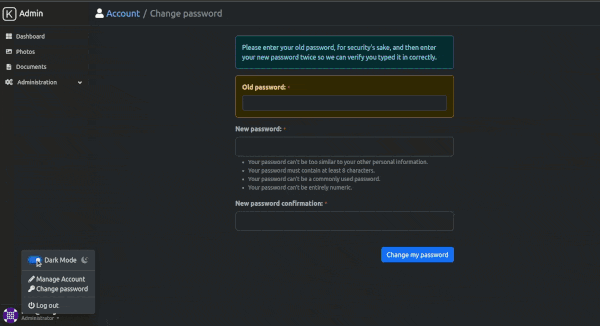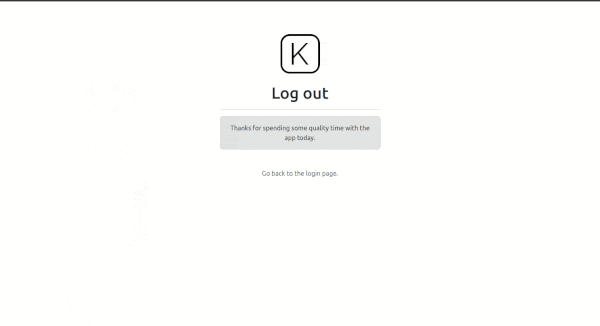
django-admin-kubi
Kubi applies a Bootstrap 5 facelift to the Django admin, but also adds Sass support for custom styling and Font Awesome icons. It includes a sidebar menu for easy navigation and support for some third-party packages, including django-modeltranslation, django-modeltrans, django-import-export, django-two-factor-auth, and django-colorfield.
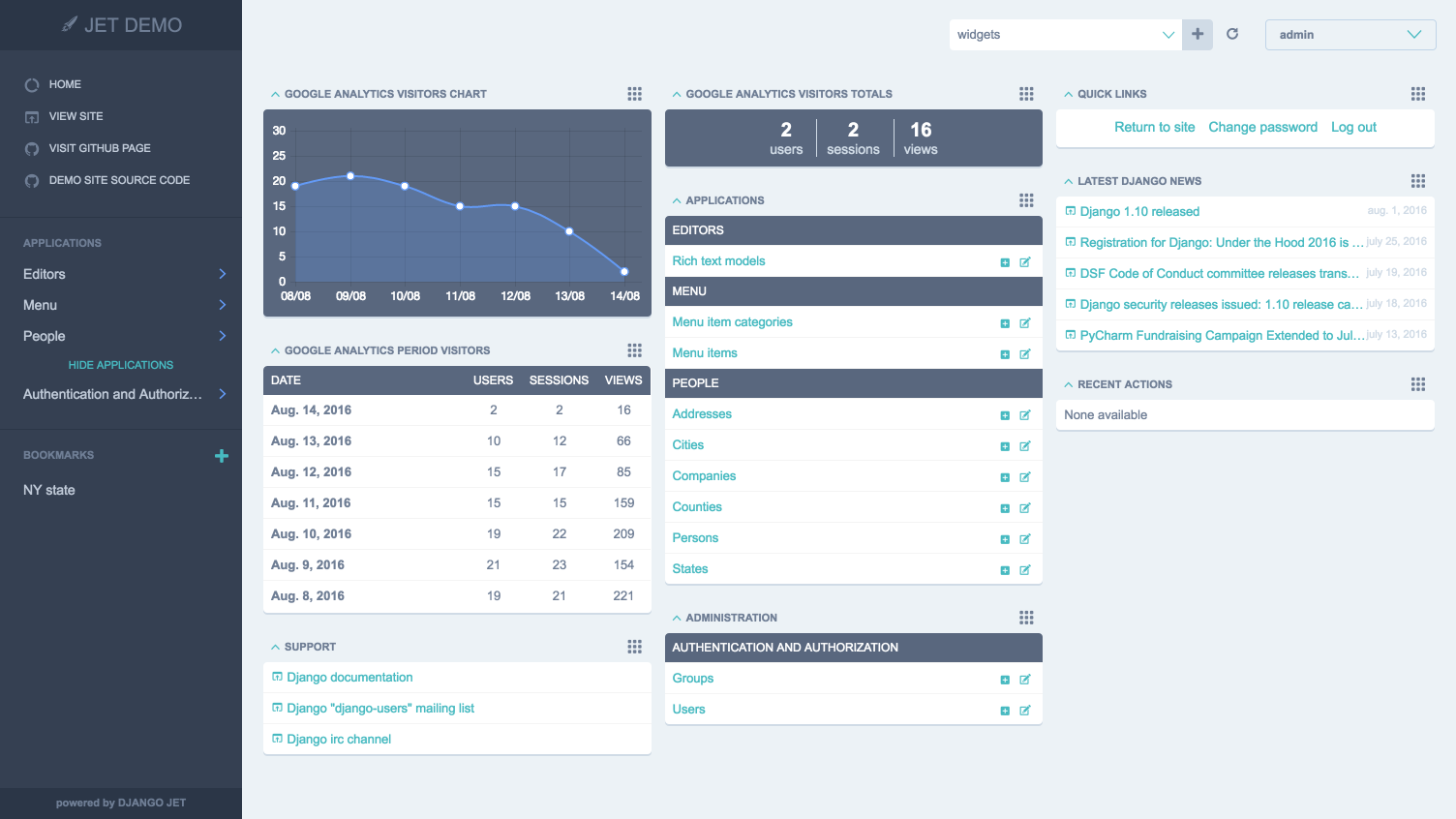
django-jet-reboot
Modern template for the Django admin interface with improved functionality. It provides the ability to create a custom dashboard and modules. Also includes user-selectable themes through the UI.
django-semantic-admin
A responsive Django admin theme based on Semantic UI. Includes JavaScript datepicker and timepicker components. Includes support for django_filter and django-import-export.
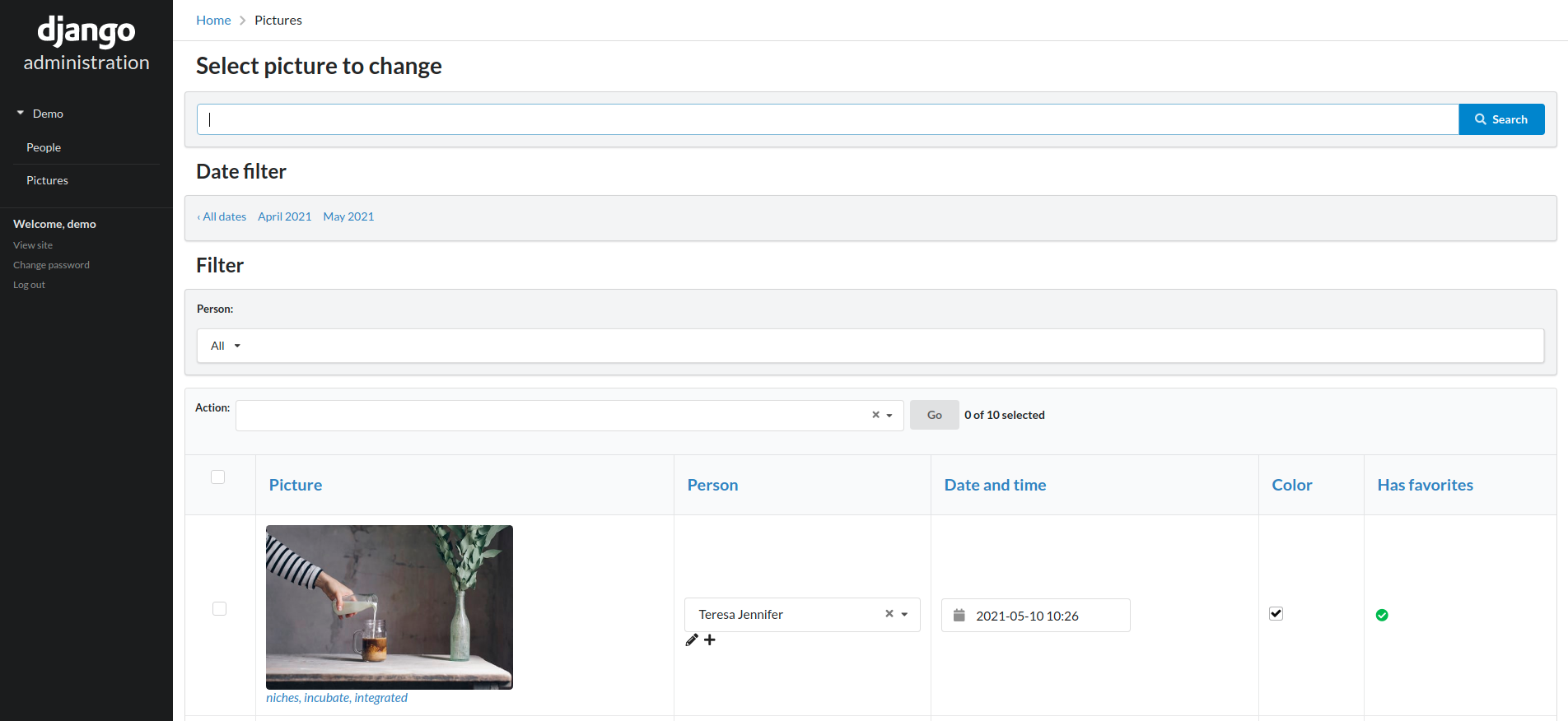
Simple UI
A modern theme based on vue + element-ui which comes with 28 different themes. The documentation is originally in Chinese, but there is a translation in English.
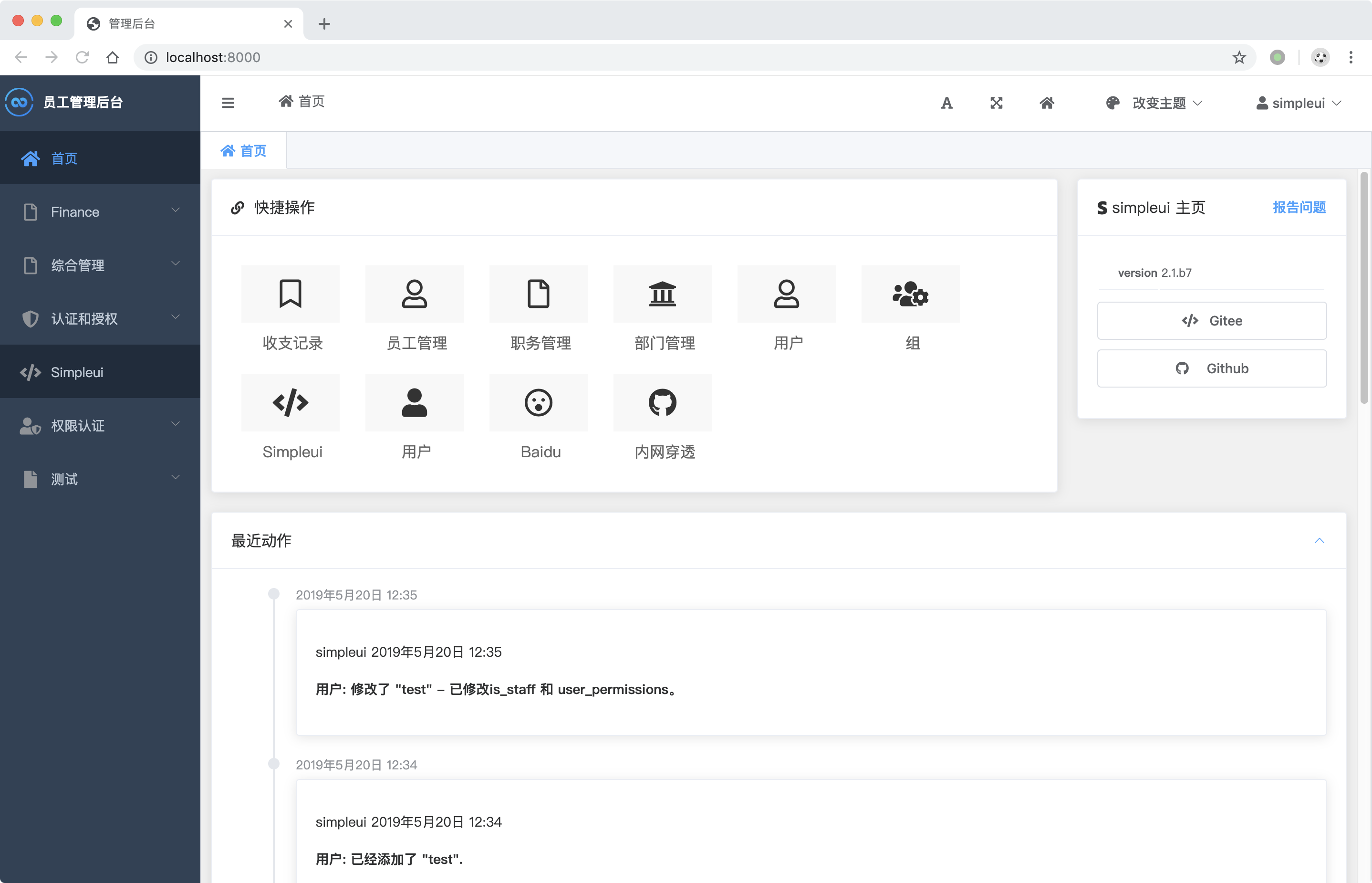
Grapelli
Grappelli is a grid-based alternative to the Django admin which provides a few nifty features such as a custom TinyMCE integration, customizable dashboard, and inline sortables which can be updated by drag and drop.
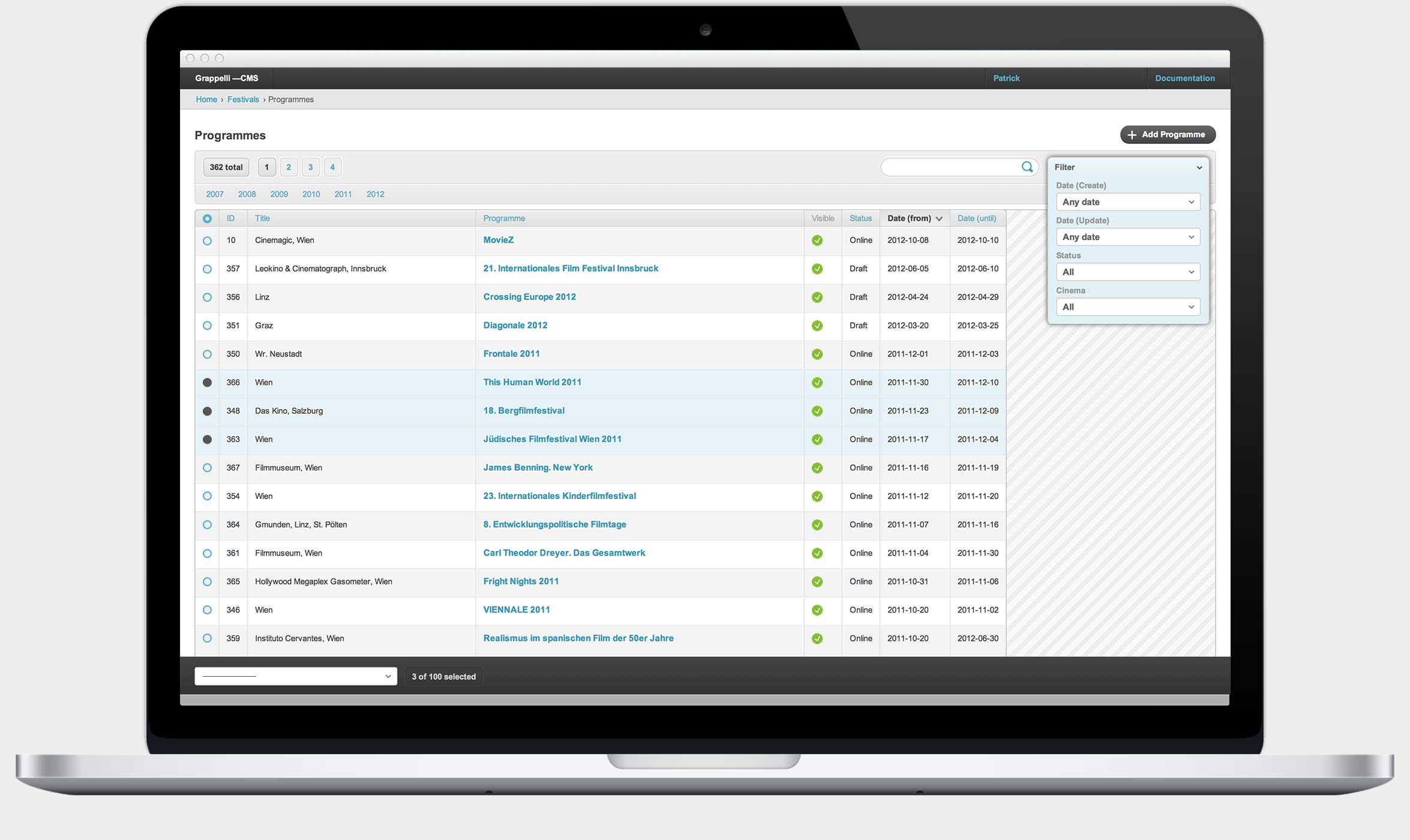
django-admin-interface
A modern responsive flat admin interface which comes with optional themes that can be installed for Bootstrap, Foundation, and U.S. Web Design Standards, and customizable by the admin itself. Other features include replacing admin pop-ups with modals, accordions in the navigation bar to collapse applications, sticky filters and buttons to prevent them from scrolling off the screen, and a language switcher. Also includes support for django-ckeditor, django-dynamic-raw-id, django-json-widget, django-modeltranslation, django-rangefilter, django-streamfield, django-tabbed-admin, and sorl-thumbnail.
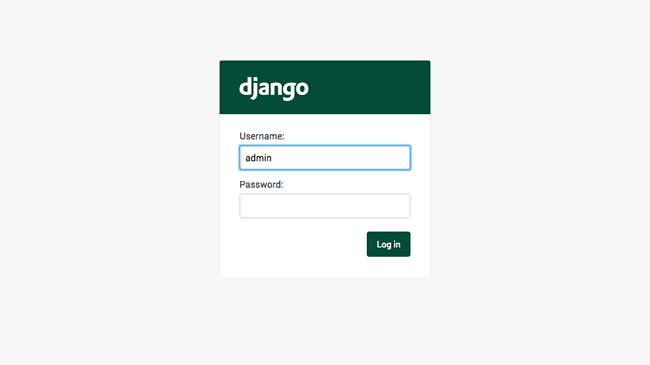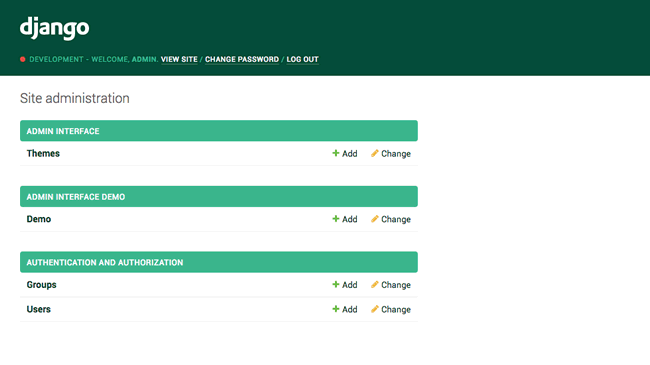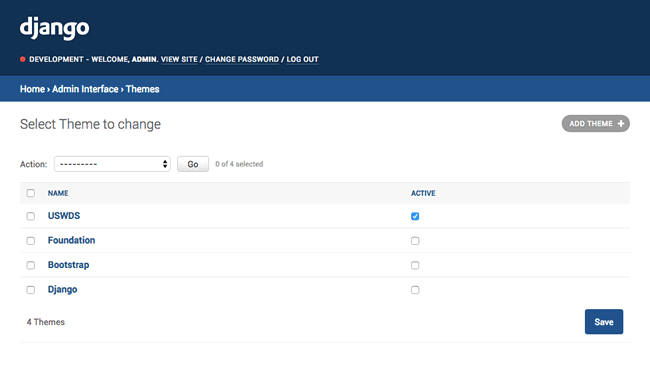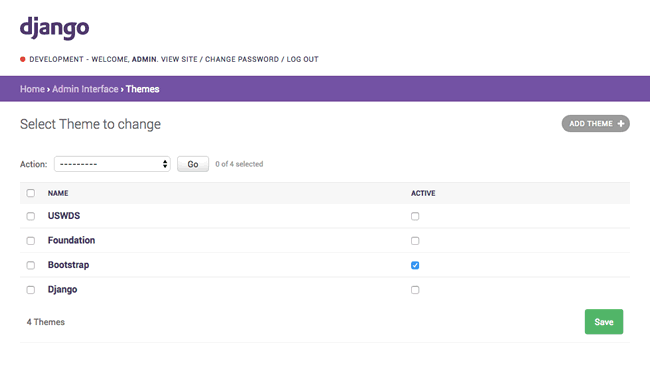
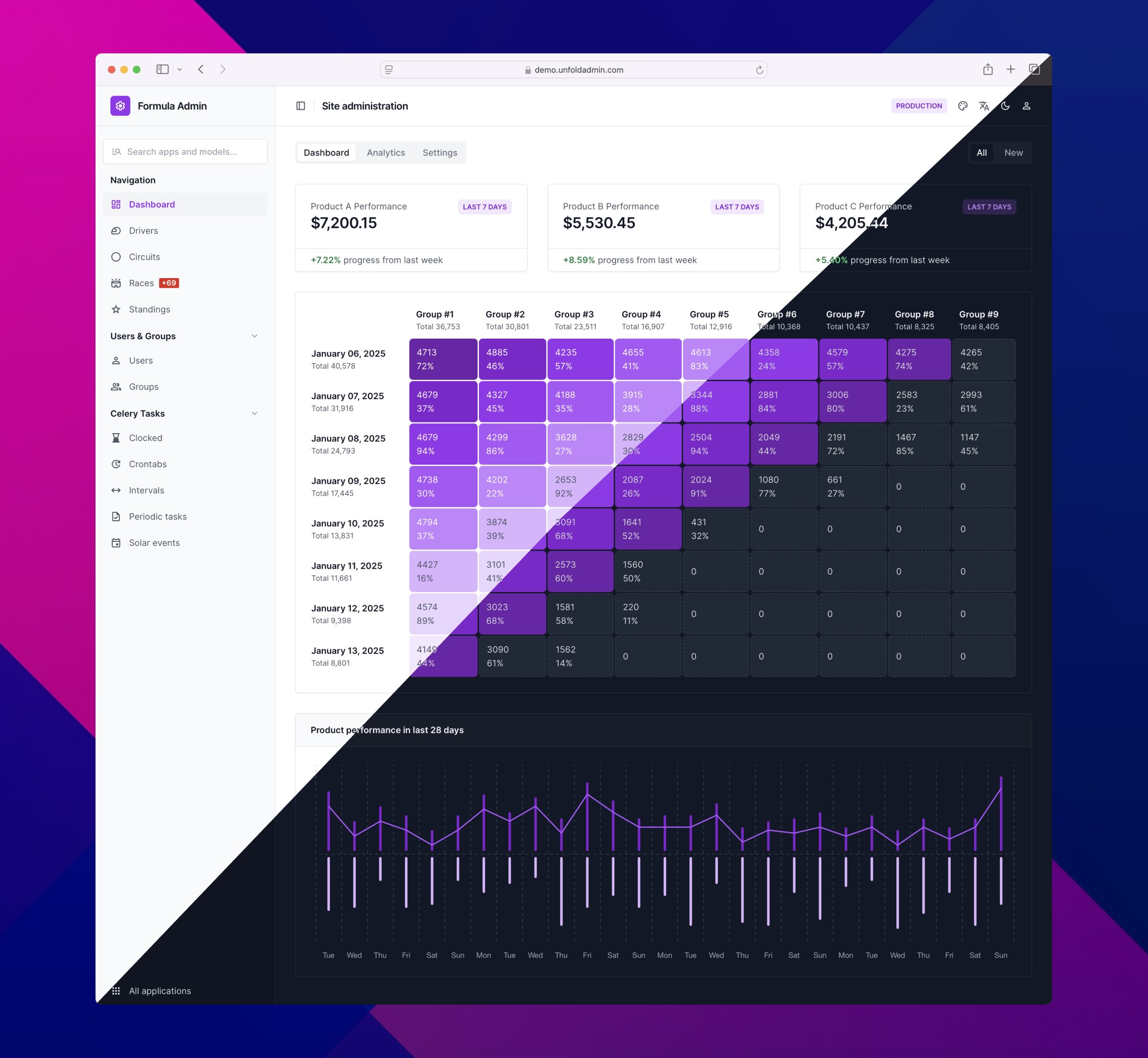
Unfold
Unfold transforms the Django admin and is built with TailwindCSS. It includes custom widgets, pages, and admin sites. Also provides a language selector, conditional fields, custom filters, tabs, and additional features for actions. There are a lot of available settings and it is extremely customizable.
From The Django weblog at 2025-04-18 08:07:28
See you at PyCon US in Pittsburgh!

We’ll be at PyCon US 2025, and hope to see the Django community and all our Python friends there ❤️! We have been granted a community booth at the conference – come say hi in the Expo Hall during open hours. There may be Django stickers available to pick up!
Represent Django
For our Individual Members – if you’d like to help us showcase Django, we’re looking for help staffing the booth (members-only forum)! This is a great opportunity to give back to support our project – consider it!

Credit: Paolo Melchiorre (CC-BY-SA)
From The Django weblog at 2025-04-17 10:00:00
Run your tests against Django's main!
This is the blog version of a talk! If you prefer, watch the recording on YouTube:

Django is known for its stability. The framework makes a strong commitment to API stability and forwards-compatibility, ensuring that developers can rely on it for building long-term, maintainable projects. A key aspect of this commitment involves extensive testing and structured releases—an area where testing by Django users can significantly enhance Django’s reliability. Here’s a closer look at how this works, and how you can contribute 🤝.
How Django stays stable
Django's stability is upheld through rigorous testing. As of Django 5.2, there are more than 18,000 tests run against all officially supported database backends, Python versions, and operating systems. Additionally, Django follows a well-structured deprecation policy, ensuring that public APIs are deprecated over at least two feature releases before being removed.
The feature release schedule is systematic and structured:
- Active development happens on the
mainbranch. - A stable branch (for example
stable/5.2.x) is forked when an alpha release is made. - After a month, the beta release follows, where only release-blocking bug fixes are allowed.
- A month later, a release candidate (RC) is published, marking the translation string freeze.
- If no critical bugs are found, the final release is published after a couple of weeks.
With this structured approach, Django ensures that releases are stable. However, bugs can and do occasionally slip through the cracks!
Catching issues early
The best time to catch issues is before they reach the final release. Ideally, potential bugs should be caught at the pull request stage, but keeping up with all changes is challenging. This is where the community can help—by running their tests with Django's main branch.
How you can help
You can set up your test suite to run with Django's main branch in your tests pipeline. Here's an example using GitHub Actions, a popular Continuous Integration platform:
test:
runs-on: ubuntu-latest
continue-on-error: ${{ matrix.experimental }}
strategy:
matrix:
include:
- python: "3.13"
django: "git+https://github.com/django/django.git@main#egg=Django"
experimental: true
steps:
- uses: actions/checkout@v4
- uses: actions/setup-python@v5
with:
python-version: ${{ matrix.python }}
- run: pip install -r requirements.txt
- if: ${{ matrix.experimental }}
run: pip install "${{ matrix.django }}"
- run: python -Wd manage.py test
If you maintain a Django package, you likely already test with multiple Django versions. Adding the main branch ensures that your project stays ahead of potential breaking changes.
Why this helps you
Running tests with Django main allows you to detect when changes in Django break your project. Sometimes, this happens due to the removal of internal APIs (that were never intended for reuse outside Django 🙈). If your tests fail, you can identify which commit caused the issue and adjust your code accordingly.
For example, on the Wagtail CMS project, recently caught an issue when an internal class, SubqueryConstraint, was removed from Django. This wasn't a bug in Django—it was the removal of an internal workaround that was no longer needed. If your project relies on internal APIs, testing against main is crucial to avoid surprises.
Why this helps Django
Testing with main doesn't just help your project—it helps Django too. Sometimes, your tests may fail due to legitimate regressions in Django that its test suite doesn't cover. Reporting these issues ensures they get fixed before the next release.
For example, just two days before Django 5.2 alpha was released, Wagtail tests on main helped detect a bug where calling .full_clean() on a child model in a multi-table inheritance setup triggered an unintended database query. This regression was promptly fixed, ensuring a smoother release for all users.
Take action: test against Django's main and report issues
By running your tests against Django's main branch and reporting any issues you find, you contribute to a more stable framework for everyone. It's a small step that makes a big impact.
So, take a few minutes today to update your automated tests setup and help keep Django as reliable as ever!
From The Django weblog at 2025-04-14 22:10:40
DSF member of the month - Öykü Gümüş
For April 2025, we welcome Öykü Gümüş as our DSF member of the month! ⭐
Öykü Gümüş has been Django developer for many years. She has been DjangoCon Europe organizer in 2018 and Django Girls mentor in Istanbul for multiple years. She has been a DSF member since November 2019.
You can learn more about Öykü by visiting Öykü's GitHub Profile.
Let’s spend some time getting to know Cory better!
Can you tell us a little about yourself (hobbies, education, etc)
Hi, I am Öykü, software engineer currently based in Germany.
I studied Computer Engineering in Istanbul, and during my university years, I realised I really enjoy being part of tech communities such as Django Girls, PyLadies and etc.. And I have been trying to play an active role in such groups ever since! Apart from that, I like drawing, and currently trying to improve my illustration skills. In general, I enjoy learning new things. For example started learning cello after 25 years of age, and loving every minute of my attempts to play it. I also love cycling and hiking. Germany is offering so much in those areas and I am always looking for a chance to get on the road.
How did you start using Django?
During my university studies, I started working as a part time developer and my first ever job was with Django. Loved how versatile it was!
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
Besides Django, I’ve used Flask, which gives you more control and is great for microservices, and FastAPI, which I really like for its async capabilities and performance. If I had magical powers to add something to Django, I’d probably improve its async support to make it more seamless throughout the stack. Right now, you can work around it, but it’s not as smooth as in FastAPI, for example.
What projects are you working on now?
Lately, I’ve been diving into GraphQL—experimenting with Graphene in Django and playing around with Apollo Client on the frontend. It’s been interesting to compare it with traditional REST APIs and explore how it can streamline data fetching in more complex UIs.
Which Django libraries are your favorite (core or 3rd party)?
There are a few Django libraries I keep reaching for, both core and third-party. Core-wise, I really appreciate how solid the django.contrib.admin is. It saves so much time in early development. Also, Django’s ORM and authentication system are very well designed—I rarely need to look elsewhere unless I’m doing something super custom. For third-party libraries, a few that I really enjoy using: django-rest-framework django-allauth and graphene-django
What are the top three things in Django that you like?
The ORM, the "Batteries Included" policy and Django's amazing community ❤️
You have been mentor for DjangoGirls+ multiple times, how did you start to mentor? Do you have any recommendation for potential folks interested to mentor?
Oh yes, I met with Django Girls in Istanbul and immediately wanted to take part by mentoring and couldn't love it more! It has great atmosphere and provides such a supportive environment, that I can safely suggest everyone just at least try it once. It's amazing to see the direct impact you can make on people by simply being there. One thing anyone interested in mentoring should never forget is to always maintain an inclusive and safe space.
You were part of the DjangoCon Europe organization in 2018, what makes you volunteer for this event?
The kindness of the organisers of another conference actually. It was Europython 2017 folks, and they kindly provided me, student at the time, a financial aid to join the conference and it was my first tech conference ever! Loved it so much, that I thought I should pay it forward. 🙂
Is there anything else you'd like to say?
Thanks so much for the chat—really enjoyed it! I also just want to say how valuable communities like this are, especially for folks starting out or navigating their path. Having spaces where people can share, support, and learn from each other makes a huge difference.
Thank you for doing the interview, Öykü !
From The Django weblog at 2025-04-09 07:22:15
Annual meeting of DSF Members at DjangoCon Europe
We’re organizing an annual meeting for members of the Django Software Foundation! It will be held at DjangoCon Europe 2025 in two weeks in Dublin, bright and early on the second day of the conference. The meeting will be held in person at the venue, and participants can also join remotely.
Register to join the annual meeting
What to expect
This is an opportunity for current and aspiring members of the Foundation to directly contribute to discussions about our direction. We will cover our current and future projects, and look for feedback and possible contributions within our community.
If this sounds interesting to you but you’re not currently an Individual Member, do review our membership criteria and apply!
From The Django weblog at 2025-04-02 11:16:11
The Django team is happy to announce the release of Django 5.2.
The release notes showcase a composite of new features. A few highlights are:
- All models are automatically imported in the shell by default.
- Django now supports composite primary keys! The new django.db.models.CompositePrimaryKey allows tables to be created with a primary key consisting of multiple fields.
- Overriding a BoundField got a lot easier: this can now be set on a form, field or project level.
You can get Django 5.2 from our downloads page or from the Python Package Index. The PGP key ID used for this release is: 3955B19851EA96EF
With the release of Django 5.2, Django 5.1 has reached the end of mainstream support. The final minor bug fix release, 5.1.8, which was also a security release, was issued today. Django 5.1 will receive security and data loss fixes until December 2025. All users are encouraged to upgrade before then to continue receiving fixes for security issues.
Django 5.0 has reached the end of extended support. The final security release, 5.0.14, was issued today. All Django 5.0 users are encouraged to upgrade to Django 5.1 or later.
See the downloads page for a table of supported versions and the future release schedule.
From The Django weblog at 2025-04-02 10:37:50
Django security releases issued: 5.1.8 and 5.0.14
In accordance with our security release policy, the Django team is issuing releases for Django 5.1.8 and Django 5.0.14. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2025-27556: Potential denial-of-service vulnerability in LoginView, LogoutView, and set_language() on Windows
Python's NFKC normalization is slow on Windows. As a consequence, django.contrib.auth.views.LoginView, django.contrib.auth.views.LogoutView, and django.views.i18n.set_language were subject to a potential denial-of-service attack via certain inputs with a very large number of Unicode characters.
Thanks to sw0rd1ight for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.2 (currently at release candidate status)
- Django 5.1
- Django 5.0
Resolution
Patches to resolve the issue have been applied to Django's main, 5.2 (currently at release candidate status), 5.1, and 5.0 branches. The patches may be obtained from the following changesets.
CVE-2025-27556: Potential denial-of-service vulnerability in LoginView, LogoutView, and set_language() on Windows
- On the main branch
- On the 5.2 branch
- On the 5.1 branch
- On the 5.0 branch
The following releases have been issued
- Django 5.1.8 (download Django 5.1.8 | 5.1.8 checksums)
- Django 5.0.14 (download Django 5.0.14 | 5.0.14 checksums)
The PGP key ID used for this release is : 3955B19851EA96EF
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum. Please see our security policies for further information.
From The Django weblog at 2025-03-19 07:49:49
Django 5.2 release candidate 1 released
Django 5.2 release candidate 1 is the final opportunity for you to try out a composite of new features before Django 5.2 is released.
The release candidate stage marks the string freeze and the call for translators to submit translations. Provided no major bugs are discovered that can't be solved in the next two weeks, Django 5.2 will be released on or around April 2. Any delays will be communicated on the on the Django forum.
Please use this opportunity to help find and fix bugs (which should be reported to the issue tracker), you can grab a copy of the release candidate package from our downloads page or on PyPI.
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
From The Django weblog at 2025-03-14 11:53:00
DSF member of the month - Cory Zue
For March 2025, we welcome Cory Zue (@coryzue.com) as our DSF member of the month! ⭐
Cory Zue is a Django developer for many years. He is currently a member of the DSF Social Media Working Group and he has been a DSF member since octobre 2022.
You can learn more about Cory by checking out his website or visiting Cory's GitHub Profile.
Let’s spend some time getting to know Cory better!
Can you tell us a little about yourself (hobbies, education, etc)
I'm a programmer-turned-manager-turned-entrepreneur and currently run a portfolio of businesses on my own (using Django of course!).
I grew up in Massachusetts and studied Computer Science at MIT where I met the founders of Dimagi, where I ended up as CTO for 10 years before starting my own businesses. In 2016, I moved to Cape Town, South Africa for a "temporary" relocation, and have been here ever since. These days my main hobbies include surfing, trail running, and exploring nature with my wife and two boys.
How did you start using Django?
My first major Django project was working on an SMS-based system that helped with the distribution of millions of bednets in Nigeria. It was built on top of a Django-based platform called RapidSMS that was initially developed by UNICEF. After that I worked on several other RapidSMS systems before eventually leading Dimagi's CommCare server team. CommCare eventually became -- to my knowledge -- the largest open source Django codebase in terms of contributions/commits.
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
I still love Django and use it for most projects that need a backend. That said, I find Django's "hands off" approach to modern front end development to be a big barrier for people who aren't already familiar with the framework.
If I had magical powers I would convince the Django community that it is worth providing some out-of-the-box support for modern front end tooling like TailwindCSS or a JavaScript bundler. I'd also try to get official "starter projects" built into the framework that show how you can use Django with some of the more popular front end options like React and HTMX.
What projects are you working on now?
My main project right now is SaaS Pegasus, which is a Django codebase creator that helps you spin up new projects more efficiently by bundling in even more batteries than Django itself. This includes things like configuring auth, front end, and deployment, but also has some more powerful features like multi-tenancy and billing baked in.
One of the great things about running Pegasus is that I can justify building new Django apps as dogfooding the product. So I always have other Django projects I'm working on. Right now the biggest one is a RAG chat-with-your-data LLM project called Scriv.ai.
Within the Django community my main contributions are in the form of writing in-depth guides to using Django, as well as pitching in on the Social Media working group to help grow Django's audience.
Which Django libraries are your favorite (core or 3rd party)?
It's hard to go with anything other than the ORM (and migrations framework), which I still feel is Django's greatest and most important feature. It just fits my brain much better than SQLAlchemy or other options I've used.
One lesser-known library I'll shout out that I have been enjoying lately is django-cotton, which provides a nice little layer of syntactic sugar and tooling that makes working with components in Django templates much nicer.
What are the top three things in Django that you like?
-
The ORM + migrations.
-
The community.
-
That nearly every backend use case I have already has a feature that's been built to accommodate it (e.g. middleware, messages, i18n, etc.). I feel like the modern JavaScript frameworks I've used are way behind on this front.
What would you recommend to someone who wants to start out as an entrepreneur like you?
I have an entire talk/article about this!
But if I were to emphasize the most important part that worked for me, it was creating enough space in my life for deep, uninterrupted work and structuring it in a way that I never ran out of money or energy while I was trying (by working part time while I was getting started). In general, the path to success usually takes a long time, so giving yourself plenty of time is really important. The tactics you can figure out as you go, but the space and time to do it is the most important thing to have in place. Your main goal is not to quit.
Is there anything else you'd like to say?
Thank you for including me in this series!
Thank you for doing the interview, Cory!
From The Django weblog at 2025-03-13 14:00:00
Accessibility and inclusivity at FOSDEM 2025
For this year’s FOSDEM conference, our Django accessibility team organized the "Inclusive Web" track. Here’s a recap of how it went!
The idea for the Inclusive Web devroom started at FOSDEM 2024, where we discussed the importance of showcasing accessibility and inclusivity work in open source, in web development and beyond. The Django accessibility team got to work on a FOSDEM 2025 proposal. Lo and behold, it got accepted, and here we are with a room full of people interested in those topics, and a great lineup of speakers!

The room was full for most of the day with about 70 attendees, with the conference also providing a livestream for remote participants. We had a great mix of talks, covering a lot of the aspects of the Inclusive Web that we wanted to showcase.
The talks
Top Accessibility Errors Found in Open Source Through Automated Testing
In the first talk of the day, Raashi Saxena shares insights on the most common accessibility errors in open-source projects, based on manual and automated testing. She highlights real-world case studies to help developers improve accessibility in their projects – and warn against the legal risks of poor accessibility!

Solving the world’s (localization) problems
Eemeli Aro and Ujjwal Sharma introduce MessageFormat 2, a new standard to address long-standing localization challenges. They discuss its potential applications and the tools being built around it. This standard is very promising for Django developers working on multilingual applications to provide better translations for users, and better capabilities for translators.

Alternative Text for Images: How Bad Are Our Alt-Text Anyway?
Mike Gifford explores the importance of alt text in web accessibility and how often it misses the mark. He demonstrates his alt text scan Python script for auditing alt-text across websites. Alt text is a common issue on Django projects, and the AI generation showcased by Mike has the potential to move the needle.

Secure and Inclusive: WebAuthn for (Multi-Factor) Authentication
Storm Heg explains how WebAuthn (Passkeys) offers a secure and user-friendly alternative to traditional authentication methods. This talk covers how it works, its accessibility benefits, and how Django developers can integrate it into their projects. Storm showcases his django-otp-webauthn package and other alternatives.

How do we work out the environmental savings from accessibility?
Chris Adams discusses how supporting older devices through accessible digital services can reduce e-waste. He explores research on hardware obsolescence, data-driven methods for measuring environmental impact, and policy changes in digital sustainability. This builds upon previous work by Chris showcasing the parallels between web accessibility and sustainability.

Growing inclusive communities: Djangonaut Space program
Raffaella Suardini shares the success of the Djangonaut Space mentorship program in fostering sustainable contributions and welcoming new contributors. She provides strategies for building inclusive tech communities, which are crucial to the success of open-source projects like Django 💜.

Multilingual Speech Technologies That Understand You
Jessica Rose discusses how Common Voice’s crowdsourced speech dataset helps developers build speech technologies for underrepresented languages. She highlights the challenges of linguistic diversity in tech – which are very relevant for a project with such an international and multiligual user base as Django.

ATAG accessibility audits: worth your while
Thibaud Colas introduces the Authoring Tool Accessibility Guidelines (ATAG) and explains why they are essential for content creation tools, like the Django admin. He shares highlights of where projects can learn a lot from ATAG, making this talk valuable for Django developers working with content publishing.

All recordings
You can watch them all on the FOSDEM website:






See you in 2026
We had a blast running this devroom, and we’re looking forward to doing it again in 2026 if we get the chance! Thank you to our speakers, devroom organizers (Saptak, Tom, Sarah, Thibaud, Eli), and helpers (Alex and Storm) for making this event a success! 🎉

From The Django weblog at 2025-03-06 12:35:38
Django security releases issued: 5.1.7, 5.0.13 and 4.2.20
In accordance with our security release policy, the Django team is issuing releases for Django 5.1.7, Django 5.0.13 and Django 4.2.20. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2025-26699: Potential denial-of-service in django.utils.text.wrap()
The django.utils.text.wrap() and wordwrap template filter were subject to a potential denial-of-service attack when used with very long strings.
Thanks to sw0rd1ight for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.2 (currently at pre-release beta status)
- Django 5.1
- Django 5.0
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.2, 5.1, 5.0, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2025-26699: Potential denial-of-service in django.utils.text.wrap()
- On the main branch
- On the 5.2 branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.1.7 (download Django 5.1.7 | 5.1.7 checksums)
- Django 5.0.13 (download Django 5.0.13 | 5.0.13 checksums)
- Django 4.2.20 (download Django 4.2.20 | 4.2.20 checksums)
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum. Please see our security policies for further information.
From The Django weblog at 2025-02-24 09:05:03
Call for Proposals for DjangoCon Africa 2025 is now open!
The call for proposals for DjangoCon Africa 2025 is officially open! 💃🏻 Come be a part of this headline event by submitting a talk.
Submit a proposal for DjangoCon Africa 2025
Why speak at DjangoCon Africa
Simply put, it’s an excellent opportunity to put your ideas out there, share knowledge with fellow Djangonauts, and give back to our community. You get to reach both a passitonate local audience, and the global Django community once your talk is published online.
If you’re interested in our Opportunity Grants, being an approved speaker or tutorial presenter also puts you first in line to receive that.
What to cover
We’re looking for proposals from first-time speakers as well as veterans. We want talks (20 - 45 min), workshops and tutorials, (60 - 90 min), and also lightning talks (5 min). As far as topics, here are suggested ones:
- Django internals and challenges in modern web development.
- Wild ideas, clever hacks, surprising or cool use cases.
- Improving Django and Python developers’ lives.
- Pushing Django to its limits.
- The Django and Python community, culture, history, past, present & future, the why, the who and the what of it all.
- Security
- Emerging technologies and industries – AI, Blockchain, Open Source etc.
- Diversity, Equity and Inclusion
- Whatever you deem appropriate - it’s your conference after all
Ubuntu
In addition to Django, this year's edition will feature a new Pan-African open source event running alongside DjangoCon Africa - UbuCon at DjangoCon Africa!
We invite proposals on any of these topics, and more: Desktop, Cloud and Infrastructure, Linux Containers and Container Orchestration, DevOps, Virtualisation, Automation, Networking Windows Subsystem for Linux(WSL), IoT, Embedded, Robotics, Appliances, Packaging, Documentation, QA and Bug triage, Security, Compliance and Kernel, Data and AI, Video, Audio and Image editing, Open source tools, Community, Diversity, Local Outreach and Social Context.
I’m in! What do I do?
Great! 🤘 Go submit your proposal. You have until the end of March to do that but no need to wait – submit now and you can always edit the proposal later.
And if you’d like to increase your changes, make sure to review our Speaking at DjangoCon Africa 2025 documentation, and the Speakers resources.
Submit a proposal for DjangoCon Africa 2025
Not convinved yet? Check out our Connections that count: Reflecting on DjangoCon Africa 2023 in Zanzibar to hear from our 2023 participants on what the conference meant for them.
From The Django weblog at 2025-02-19 07:55:07
Django 5.2 beta 1 is now available. It represents the second stage in the 5.2 release cycle and is an opportunity for you to try out the changes coming in Django 5.2.
Django 5.2 brings a composite of new features which you can read about in the in-development 5.2 release notes.
Only bugs in new features and regressions from earlier versions of Django will be fixed between now and the 5.2 final release. Translations will be updated following the "string freeze", which occurs when the release candidate is issued. The current release schedule calls for a release candidate in a month from now, and a final release to follow about two weeks after that, scheduled for April 2nd.
Early and frequent testing from the community will help minimize the number of bugs in the release. Updates on the release schedule are available on the Django forum.
As with all alpha and beta packages, this is not for production use. But if you'd like to take some of the new features for a spin, or to help find and fix bugs (which should be reported to the issue tracker), you can grab a copy of the beta package from our downloads page or on PyPI.
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
From The Django weblog at 2025-02-14 22:12:10
DjangoCongress JP 2025 Announcement and Live Streaming!
DjangoCongress JP 2025, to be held on Saturday, February 22, 2025 at 10 am (Japan Standard Time), will be broadcast live!
It will be streamed on the following YouTube Live channels:
This year there will be talks not only about Django, but also about FastAPI and other asynchronous web topics. There will also be talks on Django core development, Django Software Foundation (DSF) governance, and other topics from around the world. Simultaneous translation will be provided in both English and Japanese.
Schedule
ROOM1
- DRFを少しずつオニオンアーキテクチャに寄せていく
- The Async Django ORM: Where Is it?
- FastAPIの現場から
- Speed at Scale for Django Web Applications
- Django NinjaによるAPI開発の効率化とリプレースの実践
- Implementing Agentic AI Solutions in Django from scratch
- Diving into DSF governance: past, present and future
ROOM2
- 生成AIでDjangoアプリが作れるのかどうか(FastAPIでもやってみよう)
- DXにおけるDjangoの部分的利用
- できる!Djangoテスト(2025)
- Djangoにおける複数ユーザー種別認証の設計アプローチ
- Getting Knowledge from Django Hits: Using Grafana and Prometheus
- Culture Eats Strategy for Breakfast: Why Psychological Safety Matters in Open Source
- µDjango. The next step in the evolution of asynchronous microservices technology.
A public viewing of the event will also be held in Tokyo. A reception will also be held, so please check the following connpass page if you plan to attend.
Registration (connpass page): DjangoCongress JP 2025パブリックビューイング
From The Django weblog at 2025-02-11 04:51:31
DSF member of the month - Lily Foote
For February 2025, we welcome Lily Foote (@lilyf) as our DSF member of the month! ⭐
Lily Foote is a contributor to Django core for many years, especially on the ORM. She is currently a member of the Django 6.x Steering Council and she has been a DSF member since March 2021.
You can learn more about Lily by visiting her GitHub profile.
Let’s spend some time getting to know Lily better!
Can you tell us a little about yourself (hobbies, education, etc)
My name is Lily Foote and I’ve been contributing to Django for most of my career. I’ve also recently got into Rust and I’m excited about using Rust in Python projects. When I’m not programming, I love hiking, climbing and dancing (Ceilidh)! I also really enjoying playing board games and role playing games (e.g. Dungeons and Dragons).
How did you start using Django?
I’d taught myself Python in my final year at university by doing Project Euler problems and then decided I wanted to learn how to make a website. Django was the first Python web framework I looked at and it worked really well for me.
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
I’ve done a small amount with Flask and FastAPI. More than any new features, I think the thing that I’d most like to see is more long-term contributors to spread the work of keeping Django awesome.
What projects are you working on now?
The side project I’m most excited about is Django Rusty Templates, which is a re-implementation of Django’s templating language in Rust.
Which Django libraries are your favorite (core or 3rd party)?
The ORM of course!
What are the top three things in Django that you like?
Django Conferences, the mentorship programme Djangonaut Space and the whole community!
You have been a mentor multiple times with GSoC and Djangonaut Space program, what is required according to you to be a good mentor?
I think being willing to invest time is really important. Checking in with your mentees frequently and being an early reviewer of their work. I think this helps keep their motivation up and allows for small corrections early on.
Any advice for future contributors?
Start small and as you get more familiar with Django and the process of contributing you can take on bigger issues. Also be patient with reviewers – Django has high standards, but is mostly maintained by volunteers with limited time.
You are now part of the Steering Council, congratulations again! Do you have any words to share related to that?
Yes! It’s a huge honour! Since January, we’ve been meeting weekly and it feels like we’ve hardly scratched the surface of what we want to achieve. The biggest thing we’re trying to tackle is how to improve the contribution experience – especially evaluating new feature ideas – without draining everyone’s time and energy.
You have a lot of knowledge in the Django ORM, how did you start to contribute to this part?
I added the Greatest and Least expressions in Django 1.9, with the support of one of the core team at the time. After that, I kept showing up (especially at conference sprints) and finding a new thing to tackle.
Is there anything else you’d like to say?
Thanks for having me on!
Thank you for doing the interview, Lily!
From The Django weblog at 2025-02-05 12:00:00
Django bugfix releases issued: 5.1.6, 5.0.12, and 4.2.19
Today we've issued 5.1.6, 5.0.12, and 4.2.19 bugfix releases.
The release package and checksums are available from our downloads page, as well as from the Python Package Index. The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E.
From The Django weblog at 2025-01-23 22:20:00
Djangonaut Space - New session 2025
We are thrilled to announce that Djangonaut Space, a mentorship program, is open for applicants for our next cohort! 🚀
Djangonaut Space is holding a fourth session! This session will start on February 17th, 2025. We are currently accepting applications until January 29th, 2025 Anywhere on Earth. More details can be found in the website.
Djangonaut Space is a free, 8-week group mentoring program where individuals will work self-paced in a semi-structured learning environment. It seeks to help members of the community who wish to level up their current Django code contributions and potentially take on leadership roles in Django in the future.
“I'm so grateful to have been a part of the Djangonaut Space program. It's a wonderfully warm, diverse, and welcoming space, and the perfect place to get started with Django contributions. The community is full of bright, talented individuals who are making time to help and guide others, which is truly a joy to experience. Before Djangonaut Space, I felt as though I wasn't the kind of person who could become a Django contributor; now I feel like I found a place where I belong.” - Eliana, Djangonaut Session 1
Enthusiastic about contributing to Django but wondering what we have in store for you? No worries, we have got you covered! 🤝
From The Django weblog at 2025-01-19 20:30:00
Django earns the CHAOSS DEI Bronze badge 🫶
We’re excited to announce that Django has been awarded the CHAOSS Diversity, Equity, and Inclusion (DEI) Bronze Badge!

This badge reflects our ongoing commitment to fostering a diverse, equitable, and inclusive community for all Djangonauts. It’s part of the CHAOSS DEI Project Badging initiative.
Our new Diversity, Equity, and Inclusion Project Statement details all the ways in which we want to create an environment where everyone can participate and thrive, and complements our pre-existing Django Community Diversity Statement. From inclusive leadership structures to Django events, we strive to ensure our community is welcoming, transparent, and supportive.
Thank you to everyone in the Django community who contributes to making our project inclusive, accessible, and welcoming 🫶. Thank you to Sarah Boyce, who led the work for us to be awarded this badge as part of . We view this milestone as part of a continuous journey for our project and community to improve, and look forward to building an even more vibrant and supportive community together.
From The Django weblog at 2025-01-16 12:00:00
Hello from the new Steering Council; and a quick temporary voting process change
Hello Django community! The Steering Council is officially in action and we want to give you a heads up on a change we're making for the short-term.
The process for formal Steering Council votes (documented in DEP 10) has not been working. It's our goal for the community to refresh Django's governance during the upcoming release cycle. In order to allow us to move forward now, and under supervision of the DSF Board, we are suspending use of the +1, 0, -1 public voting system in cases where a Steering Council consensus clearly exists. Instead, we will deliberate internally, summarize our opinions, and share that publicly (location and full details TBD).
We hope that this allows us to move faster on the smaller things we have in front of us currently. We appreciate all of your patience and look forward to what we all do together!
-- The Django Steering Council: Carlton, Emma, Frank, Lilly, and Tim
From The Django weblog at 2025-01-16 06:15:00
Django 5.2 alpha 1 is now available. It represents the first stage in the 5.2 release cycle and is an opportunity for you to try out the changes coming in Django 5.2.
Django 5.2 brings a composite of new features which you can read about in the in-development 5.2 release notes.
This alpha milestone marks the feature freeze. The current release schedule calls for a beta release in about a month and a release candidate about a month from then. We'll only be able to keep this schedule if we get early and often testing from the community. Updates on the release schedule are available on the Django forum.
As with all alpha and beta packages, this is not for production use. But if you'd like to take some of the new features for a spin, or to help find and fix bugs (which should be reported to the issue tracker), you can grab a copy of the alpha package from our downloads page or on PyPI.
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
From The Django weblog at 2025-01-14 14:00:00
Django security releases issued: 5.1.5, 5.0.11, and 4.2.18
In accordance with our security release policy, the Django team is issuing releases for Django 5.1.5, Django 5.0.11, and Django 4.2.18. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2024-56374: Potential denial-of-service vulnerability in IPv6 validation
Lack of upper bound limit enforcement in strings passed when performing IPv6 validation could lead to a potential denial-of-service attack. The undocumented and private functions clean_ipv6_address and is_valid_ipv6_address were vulnerable, as was the django.forms.GenericIPAddressField form field, which has now been updated to define a max_length of 39 characters.
The django.db.models.GenericIPAddressField model field was not affected.
Thanks to Saravana Kumar for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.1
- Django 5.0
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.1, 5.0, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2024-56374: Potential denial-of-service vulnerability in IPv6 validation
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.1.5 (download Django 5.1.5 | 5.1.5 checksums)
- Django 5.0.11 (download Django 5.0.11 | 5.0.11 checksums)
- Django 4.2.18 (download Django 4.2.18 | 4.2.18 checksums)
The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum, nor via the django-developers list. Please see our security policies for further information.
From The Django weblog at 2025-01-09 00:43:00
DSF member of the month - Hiroki Kiyohara
This month marks the start of a new year, and the Django Software Foundation would like to wish you all a very happy new year. New year, new resolutions, but also the start of a new blog post series, with DSF members presented each month through an interview. A great way to learn more about the people behind Django, recognized for their contribution to the DSF mission.
For January 2025, we welcome Hiroki Kiyohara (@hirokiky) as our DSF member of the month! ⭐
Hiroki is the creator and a staff member of DjangoCongress JP. The CFP is still open!
He has done a lot for the Django Japan community which exist for many years and he has been a DSF member since October 2024.
You can learn more about Hiroki by checking out his website or visiting Hiroki’s GitHub Profile.
Let’s spend some time getting to know Hiroki better!
Can you tell us a little about yourself (hobbies, education, etc)
My name is Hiroki Kiyohara and I am the CEO of an AI Startup named ZenProducts. I like techno music, cars, drinking and VRChat!
How did you start using Django?
I started learning Python around 2010 after reading an essay "How to become a Hacker", which had a big impact on my life. I created a web service using Django, which has been a great project since then.
What other framework do you know and if there is anything you would like to have in Django if you had magical powers?
One thing I wanted to include in Django was an asynchronous worker, but it was already discussed as a future plan!
What projects are you working on now?
We are developing Shodo (https://shodo.ink/), an AI proofreading service for Japanese texts. The AI we developed in-house (by using transformers lib) and the server are all in Python. Of course we use Django with Async!
Which Django libraries are your favorite (core or 3rd party)?
We often use django-storages, DjangoRestFramework and pytest-django
What are the top three things in Django that you like?
Admin, Migration and ORM, and the last thing is the community (i.e. you!)
What made you decide to create DjangoCongress JP? Do you have any advice for someone who would like to create a local Django conference?
There was PyCon JP, but as Python became more widely used in different areas, there were fewer Django and web talks. So we created a Django-only event so that we could cover in-depth stuff.
I think if there is 1 person to join, you can start your event. Not just a big conference, we can create a community.
Do you have a quote or proverb in Japanese that you personally love?
I love 色即是空. It means that form is emptiness. So everything is not an absolute object or form and everything can be changed and something like flow. I also love "The times they are a changin’" by Bob Dylan. Both of them gave us a great perspective on the world.
Is there anything else you’d like to say?
I'm very glad to be here, thank you!
Thank you for doing the interview, Hiroki!
From The Django weblog at 2024-12-24 14:00:00
Welcome to our new Django accessibility team members - Eli, Marijke, Saptak, Tushar
Sarah Abderemane, Thibaud Colas and Tom Carrick are pleased to introduce four new members in the Django Accessibility team ❤️.
Marijke (pronounced Mah-Rye-Kuh) is a freelance web developer who creates human-friendly applications. She is based in Groningen, The Netherlands, specializing in Django, Python, HTML, SCSS, and vanilla JavaScript. She helps companies expand their existing projects, think about new features, train new developers, and improve developer team workflows. She is aDdjango contributor from the first session of Djangonaut Space program and she loves tea. You can learn more about Marijke on her website.
Eli is a full-stack developer from Uruguay who loves using Django and React. She is a Django contributor from the first session of the Djangonaut Space program. She is passionate about good quality code, unit testing, and web accessibility. She enjoys drinking Maté (and talking about it!) and watching her football team play.
Tushar is a software engineer at Canonical, based in India. He got involved on open source during his studies loving the the supportive community. Through fellowships like Major League Hacking, Tushar dove into Django and took part in Djangonaut Space. Learn more about Tushar on his personal website.
Saptak is a self-proclaimed Human Rights Centered Developer Web. He focuses on security, privacy, accessibility, localization, and other human rights associated with websites that makes websites more inclusive and usable by everyone. Learn more about Saptak on his personal website.
Listen to them talking about their work¶
Here are recent talks or podcasts from our new team members if you want to get to know them better.




What’s next¶
In truth, our four new accessibility team members joined the team months ago – shortly after we published our 2023 accessibility team report. Up next, a lot of the team will be present at FOSDEM 2025, organizing, volunteering, or speaking at the Inclusive Web Devroom.
From The Django weblog at 2024-12-18 19:38:28
Django 6.x Steering Council Election Results
The Steering Council for the Django 6.x release cycle will be:
- Carlton Gibson
- Emma Delescolle
- Frank Wiles
- Lily Foote
- Tim Schilling
Voting breakdown:
- 400 eligible voters
- 215 votes received (54%)
We had 400 eligible voters, and received 215 votes (54%). See the full voting breakdown on RankedVote.
Congratulations to the new council members! And thank you to all 12 candidates who stood for election, and everyone who took part in the voting.
—
For anyone looking for further opportunities to have their say on the future of Django, consider submitting our 2024 Django Developers survey, closing in 3 days.
From The Django weblog at 2024-12-11 02:00:00
Django 6.x Steering Council Candidates
Thank you to the 12 individuals who have chosen to stand for election. This page contains their candidate statements submitted as part of the Django 6.x Steering Council elections.
To our departing Steering Council members, Adam Johnson, Andrew Godwin, James Bennett, Simon Charette – thank you for your contributions to Django and its governance ❤️.
Those eligible to vote in this election will receive information on how to vote shortly. Please check for an email with the subject line “Django 6.x Steering Council Voting”. Voting will be open until 23:59 on December 17, 2024 Anywhere on Earth.
Any questions? Reach out via email to foundation@djangoproject.com.
All candidate statements ¶
To make it simpler to review all statements, here they are as a list of links. Voters: please take a moment to read all statements before voting!
- Andrew Miller (he/him) — Cambridge, UK
- Carlton Gibson (he/him) — Spain
- Emma Delescolle (she/her) — Belgium
- Frank Wiles (he/him) — Lawrence, Kansas, USA
- Jake Howard (he/him) — UK
- Lily Foote (she/her) — United Kingdom
- Mark Walker — Chester, UK
- Ryan Cheley (he/him) — California, US
- Ryan Hiebert —
- Sage Abdullah (he/him) — Jakarta, Indonesia / Bristol, UK
- Tim Graham — Philadelphia, PA USA
- Tim Schilling (he/him) — United States
Andrew Miller (he/him) Cambridge, UK ¶
Hi there, for those that haven’t come across me yet, I’m very active on the Discord, joining a couple of years ago, I serve as a moderator and generally helping out. I have also authored a Working Group proposal that is almost ready to go live, pending Board approval. Finally I organise the monthly Django Social in Cambridge.
However perhaps what is most relevant to my nomination for the Steering Council are the blog posts I have written this year. They have been short & snappy where I have prodded and explained different aspects of using Django, the contributing process and other aspects of the community.
I am nominating myself for the Steering Council to ensure that Django has a secure future. Personally I have used Django for the last 12 years and it has been integral to my software engineering career. The last two and half years have been the best in terms of getting involved in the community and has increased my passion for improving Django itself and seeing it have a future beyond my personal usage.
While there is energy in the community, the technical vision has stagnated and needs a reboot. As Django is about to celebrate it’s 20th birthday, I want to see Django celebrate it’s 30th & 40th birthday’s and still be relevant to the world of web development. But what does that mean for us now as a community and how to do we ensure that future? In short I believe the next Steering Council needs to experiment with a range of ideas and gauge the community reaction to them. These ideas will form the first iteration of processes that future Steering Council’s can progress and mature.
To me these ideas need to focus on the following high level goals:
- Transparency & Consistency of communication
- Clearer, simpler Governance
- Vision of where Django could be in 10 or 20 years from now.
- Strengthening the community through teams that provides growth for each and every member
Each of these goals have plenty of actionable items… for example:
- Communication: Coordinate with the Board to recognise the work of the wider ecosystem of packages on the website and in other resources.
- Governance: Deeply examine the DEP process, simplify it where needed so we can normalise the process of writing a DEP to be closer to Forum post.
- Vision: Identify potential landmark features for the 6.X release cycle and beyond. Even propose what features might be in the Django 11.X cycle (10 years time).
- Teams: Start to create career tracks within the community, this would include Djangonaut space, Google Summer of Code, existing teams and new teams yet to be formed.
Do I expect this next Steering Council to achieve all of these goals above in one go? While these goals are idealistic, I expect this next Council to lay the foundations for futures Council’s to thrive and creating the on-ramps for a larger vibrant community of Djangonauts, ensuring the Django’s future is bright and secure.
Feel free to reach out to me if you have further questions about anything above.
Carlton Gibson (he/him) Spain ¶
I'm running for the Steering Council to help push Django forward over the 6.x release cycle.
We’re at an exciting time for the framework. There’s a whole fresh wave of new contributors keen to experiment. I think we should lean into that. My particular interest here is in helping to support, promote, and leverage the third party ecosystem better that we have done. I wrote at some length on that in my recent Thoughts on Django’s Core, if you’d like the details.
Beyond that, I want to help our mentoring effort. There’s a big gap between starting to contribute and staying to maintain. We’ve got all the resources we need to turn the new generation of Django’s contributors into its next generation of maintainers. That’s where I increasingly see my time and focus being spent over the coming years.
I was unsure whether to run for election or not. Whilst I was never part of the old Django Core, as a former Fellow, and maintainer of packages such DRF, django-filter, and crispy forms, I’m certainly towards the older-guard side of things, that we’ve heard much about in recent posts. We’re at a delicate time. With the governance updates needed, I feel that I still have lots to offer, and can be helpful in advancing those. As I say, I think we’re at an exciting time for the framework. I’d be honoured to serve if chosen.
Emma Delescolle (she/her) Belgium ¶
For a longer version of this statement you can read this post on my blog
For a video on similar topics, you can watch my recent Djangonaut Space session on YouTube
As a member of the Django community for the past 10 years, I've had the privilege of witnessing firsthand the project's growth and evolution.
Over the decade, I've seen many exciting changes and improvements that have shaped Django into the powerful tool it is today. However, I've also noticed a gradual slowing down of this evolution in recent years.
I have also benefited from said growth and Django's reliability and stability as I have been running a business who's main activity revolves around Django for that same amount of years. Whether it be creating, reviewing, maintaining or updating software. My application to the steering council is one of the ways in which I can give back to the community.
With my candidacy as a member of the Django Steering Council, I want to highlight my focus on ensuring Django remains relevant and sustainable for the next 20 years.
Lowering the barrier to contribution and involving a more diverse set of contributors
Most code contributions merged into Django are bug fixes or cleanups. I believe this trend is not due to an unusual abundance of bugs within the project but rather due to an unsustainable barrier to contributing new features or code improvements. Contributing to Django requires a significant amount of time, mental energy and effort, which can be discouraging to most. And often, those who have bit the bullet and gone through it once do not go through it a second or third time.
Myself and others have noted, more or less recently, that the process of contributing code to Django, including but not limited to DEPs, is daunting. The words "brutal" and "bureaucratic" have been used by myself and others to describe the process.
If elected, I aim to identify areas that hinder effective code contributions to Django and work towards simplifying the process of contributing code to the project; while keeping the right balance to also protect the time, energy and sanity of the Fellows and the review team.
Dealing with the realities of an aging code-base
As Django approaches its 20th anniversary, it's essential to acknowledge the aging code-base and technical debt accumulated over time. My goal is to initiate a review process of the existing code-base, carefully evaluating technical debt and identifying areas where improvements can be made without disrupting existing functionality.
Missing batteries and deadlines
One of the core principles of Django has always been its commitment to being a "batteries included" framework. However, in recent years, I've noticed that many of these essential features and tools have remained stagnant, without new additions or replacements emerging to support the evolving needs of our community.
Furthermore, the third-party application ecosystem that was once thriving and a jewel of the community, has become harder and harder to navigate and discover. It has also become more time-consuming for developers to have to evaluate a large set of third-party applications to solve a specific need.
As a member of the steering council I would like to work on bringing better visibility and discoverability of those 3rd-party packages and evaluate whether any such package should be brought into Django, either Django core or a spiritual successor to
contribor some other way. Some packages that come to mind aredjango-csp,django-corsanddjango-upgradebut this is in no way an exhaustive list.Feature requests and Roadmap
I plan to use my position to champion "feature requests" – a critical aspect of the council's role that has never been utilized to this date. Feature requests being also a key part in being able to set a roadmap for Django and provide guidance to potential contributors on where to get started on their journey.
Code ownership and groups
My belief is that, as an unexpected side-effect of the dissolution of the core team and the high barrier to contribution, expertise in specific areas of Django has begun to erode. However, it can be regained through targeted efforts. People involved in the aforementioned code review process would be perfect candidates for these roles, as they'd already have taken a deep dive in thoroughly understanding specific areas of the framework.
Moreover, frequent contributors to an area of the framework are often well-positioned to take on a leading role in "owning" that part of the project. However, this implies recurring contributions to said area. I believe that we need to find ways to incentivize people to become area specialists. Which brings us back to need for lowering the barrier to contribution.
More generally, I think that the project can benefit from those specialized groups, starting with an ORM group.
Closing thoughts
I believe that everything listed here can technically be achieved during the 6.x cycle if I'm elected but... things take time in the Django world. So, I don't want to over-promise either.
Frank Wiles (he/him) Lawrence, Kansas, USA ¶
The community does a really great job of reaching consensus post-BDFLs but occasionally decisions do need to be made and a direction chosen.
I would like to think my long history with Django and my wide and varied use of it as a consultant gives me a unique perspective not just as a consumer of Django but as a manager/executive helping others to make decisions around how and when to use Django. The decisions that are made impact many people and organizations in sometimes subtle and non-obviously ways. I have a ton of skin in this particular game personally.
Django has been a huge part of what has driven my career and I would be honored to help steer for a bit.
Jake Howard (he/him) UK ¶
For those who don't know me, I've been using Django professionally for almost a decade, spending over half of that focusing on performance and security. I'm also on the Core team for Wagtail CMS.
Django has a great reputation for being "batteries included" and for "perfectionists", however that reputation is starting to age. Now, people think of Django and clunky, slow, and only useful for building big monoliths. Many developers choose leaner frameworks, and end up having to re-implement Django's batteries themselves, instead of starting with Django and focusing on building their application.
For Django to progress, it needs to recharge its batteries. The ticket backlog, as well as many developer's dreams are filled with great feature ideas just looking for a little push in the right direction. Not just the big features like 2FA, Background Tasks or even type hints, but also quality of life improvements to templates, views or even the user model. To achieve this, it requires more than just code - it takes people.
From personal experience, I've seen the friction from trying to add even small features to Django, and the mountains to climb to contribute large features. To encourage new contributors, that needs to change - just because it's the way it's always been, doesn't mean it has to continue. Django is a big, complex, highly depended on project, but that doesn't mean it needs to move at a snail's pace for everything, nor does every contribution need to be 100% perfect first time. Open source projects are built on passion, which is built up over time but destroyed in seconds. By fostering and enabling that passion, the Django contributor community can flourish.
By the time Django hits 7.0, I'd love to see it more modern, more sustainable, and living up to the ideas we all have for it.
Lily Foote (she/her) United Kingdom ¶
Hi! I'm Lily and I've been a contributor to Django for about a decade, mainly working on the ORM. My biggest contributions were adding check constraints and db_default. I've also contributed as a mentor within the Django Community. I was a navigator for the pilot of Djangonaut Space (and a backup navigator in following sessions) and a Google Summer of Code mentor for the Composite Primary Keys project. I also joined the triage and review team in 2023.
As a member of the Steering Council I want to enable more people to contribute to the Django codebase and surrounding projects. I think in recent years there has been too much friction in getting a change to Django agreed. I have seen several forum threads fail to gain consensus and I've experienced this frustration myself too. I also think the DEP process needs an overhaul to make creating a DEP much easier and significantly less intimidating, making it easier to move from a forum discussion to a decision when otherwise the status quo of doing nothing would win.
I believe a more proactive Steering Council will enable more proposals to move forward and I look forward to being a part of this. I will bring my years of experience of the Django codebase and processes to the Steering Council to provide the technical leadership we need.
Mark Walker Chester, UK ¶
I'm running for the Steering Council so that I might be able to help others. I wouldn’t be in the position I am today without someone very helpful on StackOverflow many years ago who took the time to help me with my first endeavour with python.
Over the years I’ve strived to help others in their journey with python & django, an aim aided by becoming a navigator for djangonaut space and the technical lead of the Django CMS Association. Through all of this I’ve acted as a facilitator to help people both professionally and in open source, something which ties in with discussions going on about the SC being the facilitator for the continued growth of the Django community and framework itself.
Ryan Cheley (he/him) California, US ¶
Hello, I’m Ryan Cheley and I’ve decided to stand for the Django 6.x Steering Council.
My journey with the Django community began in March 2022 when I started contributing pull requests to DjangoPackages. My initial contributions quickly led to deeper involvement, and I was grateful and honored to be asked to be a maintainer following DjangoCon US 2022.
At the DjangoCon US 2022 Sprints, I worked on a SQLite-related bug in Django's ORM. This proved so valuable that I was was able to give a talk about my experience at DjangoCon US 2023, where I delivered my talk “Contributing to Django or How I learned to stop worrying and just try to fix a bug in the ORM”.
Building on this experience, I returned to DCUS 2024 to present on “Error Culture” where I took a deep dive into the widespread but often overlooked issue of how organizations manage error alerts in technology and programming domains.
My commitment to the Django ecosystem extends beyond code contributions. I've served as a Navigator for two sessions of Djangonaut Space, helping guide newcomers through their first contributions to Django. This role has allowed me to give back to the community while developing my mentorship skills.
As one of the admins for Django Commons I work with some amazing folks to help provide an organization that works to improve the maintainer experience.
Additionally, I've made various contributions to Django Core, including both code improvements and documentation enhancements.
Throughout my involvement with Django, I've consistently shown a commitment to both technical excellence and community building. My experience spans coding, documentation, mentorship, and public speaking, reflecting my holistic approach to contributing to the Django ecosystem.
My focus will be in creating sustainable and inclusive leadership structures. This would, in turn, not only provide help and support for current Django leadership, but also develop and empower future leaders.
The avenues to meet these goals include gathering diverse candidates, providing mentorship opportunities, clearly communicating expectations, and removing financial barriers to participation.
As a member of the Django Steering Council (SC) for the 6.x series, I hope to be able to accomplish the following with my fellow SC Members:
- Establish a governance structure that allows the SC to be successful going forward by:
- Providing Mentorship for future potential SC members from the Community
- Reviewing the 18-month requirements for eligibility for SC
- Communicating the expectations for SC role in Community
- Working to increase the diversity of those that are willing and able to stand for the SC in the 7.x series and going forward
- Collaborate with Working Groups to
- ease burden of fellows in a meaningful way via the Fellowship Working Group
- work with Social Media Working Group to promote new or upcoming features
- Write up weekly / monthly reports, similar to the fellows reports
- Work with the Django Software Foundation(DSF) Board to establish a stipend for 7.x SC members going forward to support their work and allow more diverse participation
- Implement a road map for Django drawing input and inspiration from the Community, specifically from these sources
- Adam G Hill post
- Thibaud Colas Forum post
- Paolo Melichiore post
- Timo Zimmerman post
- Roadmap work from early 2024
- Work on and complete a DEPs to
- Remove Dead Batteries, similar to Python PEP 594
- Determine the long term viability of Trac, research alternatives, and come up with triggers that would lead to a migration if/when necessary.
- Review and approve or reject all current draft DEPs
The Django community has done so much for me. I’m hoping that with my involvement on the Steering Council I’m able to work to do my part to ensure the long term success and viability of the Django community and leave it in a better place than I found it.
Ryan Hiebert ¶
I've worked professionally with Django and Python for the past 13 years. I've mostly lurked on the mailing lists and forums, but I have been around maintaining some smaller projects, most notably among them being django-safemigrate, aldjemy, hirefire, tox-travis, and backports.csv. I had the privilege of giving a talk at DjangoCon 2024 about Passkeys and Django.
Django has excelled in three areas. We take a batteries-included approach that empowers new developers, we have strong community governance, and we are conservative about the changes we make to maintain stability. These have been critical to Django's success, but the combination has made it challenging for Django to keep up with the changing technology landscape.
To allow Django meet the changing needs of our users both now and for the future, we need to think carefully about the important parts of each of those priorities, and tune the tension between them to allow the Django community to thrive.
Django should transition away from including batteries directly, and toward enabling add-on batteries. We should favor proposals that empower interoperability between a variety of third party batteries (e.g. the Background Workers DEP), and disfavor proposals that wish to bless a particular solution in core, no matter how wonderful the solution is (e.g. HTMX).
Django should be encouraging work that aims to expose third-party packages in our official documentation and communication channels, especially those that implement core interoperability interfaces. This will make room for new ideas and more approaches.
Django should seek to make a clear boundary around a smaller core where our preference for stability is the more important factor in empowering our diverse community.
Django should favor changes that bring it into alignment with Python community standards. It should favor this even over the "one way to do it" principle. By encouraging using Python standards, Django will better meet its responsibility as an entryway for new Python developers to be better equipped to grow in Python generally. For example, Django could encourage using appropriate standards in the pyproject.toml over extending Django-centric idioms like adding to the settings.py.
Django should encourage proposals that seek to lower the footprint of a new project. Projects like Nanodjango should inspire us to make starting with Django trivial and minimal, and make each step a newcomer might take to grow be as small as possible, so they only need to meet only the challenges required by the work they are needing to do.
Django should favor proposals to begin to include correct types, even to the point of carefully making any necessary breaking changes to help make the types correct and usable.
The DSF should, when financially feasible, fund non-core batteries that can empower the community. It may be appropriate for the DSF to make some requirements about the necessary governance required of these projects in order to qualify for funding.
The Steering Council should strongly consider recommending changes to its decision making process to make it more feasible to make and reverse decisions as it faces new challenges. Stability is maintained by active, careful, and persistent effort, not indecision.
By making decisions with these principles in mind, we can help our community maintain the root of our goals: A stable community-governed base, empowering a diverse community that excels in the fast-paced world of web development, and being a gateway for new developers.
Sage Abdullah (he/him) Jakarta, Indonesia / Bristol, UK ¶
Django's best strength is that it's built by its community – but that's also a weakness. The reality of a project of Django's scale that's been around for so long, and has so many contributors, is that making substantial changes becomes increasingly difficult. You may have heard talks about how daunting it can be to get a PR merged into Django, or how hard it is to get a feature accepted.
It doesn't have to be that way.
In 2019, I added the cross-database JSONField as part of Google Summer of Code (GSoC). Many of Django's big features have come from GSoC, and some of the contributors stay involved in the community – this year, I became a GSoC mentor for Django. As a core team member of Wagtail (a Django-based CMS), I have seen the same pattern with our participations in such outreach programs. Django can do a lot more in making community contributions more accessible and sustainable, and I think I can help.
Here's what I think the steering council should do:
- Organize a living roadmap for Django. Rather than waiting for a DEP to be proposed and acted on, the steering council should actively help the community in highlighting issues and feature requests that are high priority or most wanted.
- Maximize the potential of mentorship programs. With a roadmap in place, the steering council could help find mentors and contributors who can take on the work. Programs like GSoC, Djangonaut Space, or other initiatives can flourish if we connect the ideas with the right people.
- Communicate and document progress. To allow continuous feedback and improvement, the steering council should engage with the community and document the progress of their activities, as well as the current state of Django.
Django is at a turning point. It's time for the steering council to take a more active role with the community in shaping the future of Django, and I believe I can help make that happen.
Tim Graham Philadelphia, PA USA ¶
My deep knowledge of Django comes as a user and documentation contributor since 2009, and from working on Django as a Django Fellow from 2014-2019.
Since 2019, I've been contracted to develop and maintain several third-party database backends for Django, including CockroachDB, Google Cloud Spanner, Snowflake, and MongoDB.
I remain active on the Django Internals section of the forum and the Django ticket tracker, as well as writing and reviewing patches for Django.
Tim Schilling (he/him) United States ¶
If elected to the Steering Council, I would strive to grow our contributor base and improve the support structures in the community. I'd like to do the work to make everyone else's lives easier.
I expect this to move slowly, but I do expect this to move. The three most important goals to me are the following:
Meet as the Steering Council regularly and post a record of the discussion and actions.
To check in on our various teams and individuals. For example, the Translations team isn't a formal team yet, but it should be.
To encourage and support feature development based on community recommendations.
I will need help with this role in understanding the context and history of technical decisions in Django. The community can support me and others like me by continuing to engage in those technical discussions on the forum. Having folks provide context and clarity will be invaluable.
If elected, I would step down from the DEFNA board and step away as a DjangoCon US organizer. That would leave me being involved with the Steering Council, Djangonaut Space, and Django Commons, all of which overlap in my goal to foster community growth.
I expect there to be technical change in the next term of the Steering Council. However, my particular focus will be on the people. By engaging the community more and encouraging new people, we can strengthen the foundation of our community to support our ambitious goals of the future.
More detailed opinions can be found at: Steering Council 6.x Thoughts · Better Simple.
A list of my involvements can be found at: Tim Schilling · Better Simple
Your move now
That’s it, you’ve read it all 🌈! Be sure to vote if you’re eligible, by using the link shared over email. To support the future of Django, donate to the Django Software Foundation on our website or via GitHub Sponsors.
From The Django weblog at 2024-12-04 15:40:17
Django security releases issued: 5.1.4, 5.0.10, and 4.2.17
In accordance with our security release policy, the Django team is issuing releases for Django 5.1.4, Django 5.0.10, and Django 4.2.17. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2024-53907: Potential denial-of-service in django.utils.html.strip_tags()
The strip_tags() method and striptags template filter are subject to a potential denial-of-service attack via certain inputs containing large sequences of nested incomplete HTML entities.
Thanks to jiangniao for the report.
This issue has severity "moderate" according to the Django security policy.
CVE-2024-53908: Potential SQL injection in HasKey(lhs, rhs) on Oracle
Direct usage of the django.db.models.fields.json.HasKey lookup on Oracle is subject to SQL injection if untrusted data is used as a lhs value. Applications that use the jsonfield.has_key lookup through the __ syntax are unaffected.
Thanks to Seokchan Yoon for the report.
This issue has severity "high" according to the Django security policy.
Affected supported versions
- Django main
- Django 5.1
- Django 5.0
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.1, 5.0, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2024-53907: Potential denial-of-service in django.utils.html.strip_tags()
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
CVE-2024-53908: Potential SQL injection in HasKey(lhs, rhs) on Oracle
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.1.4 (download Django 5.1.4 | 5.1.4 checksums)
- Django 5.0.10 (download Django 5.0.10 | 5.0.10 checksums)
- Django 4.2.17 (download Django 4.2.17 | 4.2.17 checksums)
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum, nor via the django-developers list. Please see our security policies for further information.
From The Django weblog at 2024-12-04 08:53:10
And just like that, 2024 is almost over! If your finances allow, donate to the Django Software Foundation to support the long-term future of Django.
Of our US $200,000.00 goal for 2024, as of December 4th, 2024, we are at:
- 83.6% funded
- $167,272.85 donated
Other ways to give
- Official merchandise store - Buy official t-shirts, accessories, and more to support Django.
- Sponsor Django via GitHub Sponsors.
- Benevity Workplace Giving Program - If your employer participates, you can make donations to the DSF via payroll deduction.
Why give to the Django Software Foundation?
Our main focus is direct support of Django's developers. This means:
- Organizing and funding development sprints so that Django's developers can meet in person.
- Helping key developers attend these sprints and other community events by covering travel expenses to official Django events.
- Providing financial assistance to community development and outreach projects such as Django Girls.
- Providing financial assistance to individuals so they can attend major conferences and events.
- Funding the Django Fellowship program, which provides full-time staff to perform community management tasks in the Django community.
Still curious? See our Frequently Asked Questions about donations.
From The Django weblog at 2024-11-27 07:00:00
Django 6.x Steering Council Candidate Registration
Following our announcement of the 6.x Steering Council elections, today we open candidate registrations. Registrations will be open until December 4 2024 at 23:59 Anywhere on Earth.
Register as a Steering Council candidate
Eligibility
Candidate eligibility requirements are defined in DEP 12: The Steering Council. To be qualified for elections, we require both of the following:
- A history of substantive contributions to Django or the Django ecosystem. This history must begin at least 18 months prior to the individual's candidacy for the Steering Council, and include substantive contributions in at least two of these bullet points:
- Code contributions on Django projects or major third-party packages in the Django ecosystem
- Reviewing pull requests and/or triaging Django project tickets
- Documentation, tutorials or blog posts
- Discussions about Django on the django-developers mailing list or the Django Forum
- Running Django-related events or user groups
- A history of engagement with the direction and future of Django. This does not need to be recent, but candidates who have not engaged in the past three years must still demonstrate an understanding of Django's changes and direction within those three years.
If you have questions about the election please contact foundation@djangoproject.com or ask on the Django forum.
From The Django weblog at 2024-11-24 18:39:32
2024 Malcolm Tredinnick Memorial Prize awarded to Rachell Calhoun
This year it was hard to decide, and we wanted to also show who else got nominated, because they also deserve recognition, so it took a bit longer than we expected.
The Django Software Foundation Board is pleased to announce that the 2024 Malcolm Tredinnick Memorial Prize has been awarded to Rachell Calhoun.
Rachell Calhoun is an influential figure within the Django community, well known for being cheerful and always willing to help others. She consistently empowers folks behind the scenes.
Rachell got her start in the Django community through a Django Girls Seoul event. Being an educator, she started organizing Django Girls Seoul events. Her contributions to Django Girls Seoul and Django Girls Grand Rapids exemplify her commitment to sharing knowledge, spreading Django and lifting others up. Rachell is now a trustee for Django Girls +, contributing to its mission of helping women and other underrepresented groups around the world learn programming with Django.
In 2022, Rachell co-founded Djangonaut Space, an initiative designed to support new contributors to the Django ecosystem, encouraging leadership and growth. Rachell’s willingness to help people achieve their goals and celebrate their achievements has been imprinted in Djangonaut Space’s culture. Rachell and Djangonaut Space have done a stellar job on helping people become contributors and Django community members.
Her commitment to fostering diversity and inclusion extends beyond her organizational work; she has volunteered at multiple DjangoCon US events, bringing her welcoming and inclusive spirit to the community. A long-time volunteer and speaker at DjangoCon US and DjangoCon Europe from 2016 to 2024, she has shared her expertise and insights on various topics related to Django and web development.
Rachell has contributed to Django for many years, she has been instrumental in creating spaces where people of all backgrounds can thrive, making her a beloved and respected member of the global Django ecosystem.
Some quotes from the thirteen people who nominated Rachell had this to say about her:
Rachell advocates for others constantly through sponsorship, inclusivity, and connection. She is extremely empathic and seeks to not only welcome others in, but to actively bring them into the group.
She has been one of the core members of Djangonaut Space which has done a lot for bringing new contributors into the Django community. This program has done a lot to excite and energize the Django community and Rachell is one of the major reasons why. --
Throughout her career she's been involved in Django Girls starting about a decade ago in South Korea. She was a major organizer of the Grand Rapids, MI branch, before moving into the trustee role she occupies now.Rachell is one of my favorite people and she's been doing an excellent job at growing Django and helping others feel more welcome here. Rachell is an excellent choice for the Malcolm Tredinnick 2024 award!
— Tim Shilling
Rachell is an extremely skillful leader who is always nurturing newcomers into leaders. She has been pivotal to my experience with the Djangonaut Space Program.
I started out as a nervous Djangonaut who didn’t schedule my 1:1s until Rachell checked in with me and made sure I knew the program was a safe space to discuss anything.When I joined the program organizers as a Navigator Coordinator, I was initially much more of a follower. Rachell knew to step back while continuing to provide her support, so I could step into the leadership role and get my job done.
Rachell shows people that she believes in them. She does this in a friendly, gentle, and encouraging manner. She never forces anyone to make decisions that they don’t feel comfortable with. The community is really lucky to have Rachell.
— Lilian
Rachell Calhoun, one of the organizers and founders of Djangonaut Space, has been an open, supportive, and educational help on my Django journey. Her contributions to the Djangonaut Space program are invaluable—a program I hold quite dearly as a cornerstone of my technical interactions and growth.
Rachell's ideals of nurturing and guiding have shone through the program, for which I am grateful. Encouraging wonderful conversations, organizing and fostering mentorship, and being a great person!
I believe Rachell is an embodiment of the Malcolm Tredinnick spirit and am confident that should she win the prize, she would go on to create more impact for the Django community and the world at large.
— Emmanuel Katchy
Other nominations for this year included:
Anna Makarudze, Fundraising Coordinator at Django Girls+ Foundation, chair of the first DjangoCon Africa, previously served the DSF board as president.
Benjamin Balder Bach, chair of the DSF social media working group, organizer of Django Day Copenhagen for many years.
Black Python Devs, community founded by Jay Miller, to increase diversity and inclusion of typically underrepresented people.
Bhuvnesh Sharma, co-chair of the DSF social media working group, and co-founded and organized Django India.
Carlton Gibson, previously a Django fellow, co-host of Django Chat, volunteers in DjangoCon Europe and provides useful advice in forum and discord.
Christoph Bulter, active helper of the official and unofficial Django Discord.
Django Girls+, a non-profit organization and a community that empowers and helps women to organize free, one-day programming workshops by providing tools, resources and support.
Django Discord moderators and helpers, which are moderating the discord and provide help to keep the place welcoming and inclusive to everyone.
Daniel Moran, active contributor in various open-source projects, including django-tasks-scheduler. He is an administrator of the Django Commons organization.
Ester Beltrami, PyCon Italia and Django London organizer, is also a volunteer and a speaker in events such as EuroPython or DjangoCon Europe.
Felipe de Morais, co-founder of AfroPython, participant of Djangonaut Space program, organized and advised multiple Django Girls workshops across Brazil and Chile.
Jake Howard, speaker and contributor to Django, known for his work around background tasks.
Matt Westcott, frequent speaker and lead the development of Wagtail.
Russel Keith-Magee, python core contributor and previously Django core contributor and also served in the DSF board as President.
Ryan Cheley, django contributor and mentor (navigator) in Djangonaut Space program.
Simon Charette, long-time django contributor, previously member of the Django 5.x steering council
Sheena O’Connell, frequent speaker and DjangoCon Africa organizer.
Tom Carrick, Django Accessibility team creator and member, django contributor for many years and mentor (navigator) in Djangonaut Space program.
Tim Schilling, DEFNA secretary, DjangoCon Us organizer and co-founder of Djangonaut Space.
Will Vincent, former board member of the DSF, co-host of Django Chat and co-writer of Django News.
Each year we receive many nominations, and it is always hard to pick the winner. This year, as always, we received many nominations for the Malcolm Tredinnick Memorial Prize with some being nominated multiple times. Some have been nominated in multiple years. If your nominee didn’t make it this year, you can always nominate them again next year.
Malcolm would be very proud of the legacy he has fostered in our community!
Congratulations Rachell on the well-deserved honor!
From The Django weblog at 2024-11-24 16:57:43
DjangoCon Europe 2026 call for organizers completed
The DjangoCon Europe 2026 call for organizers is now over. We’re elated to report we received three viable proposals, a clear improvement over recent years.
We’ll let the successful team decide when and how to make their announcement, but in the meantime – thank you to everyone who took part in this process ❤️ We’re elated to have such a strong community in Europe. And for now, look forward to DjangoCon Europe 2025 in Dublin, Ireland! 🍀
What about 2027?
We’re not ready to plan that yet, but if you’re interested in organizing – take a moment to add your name and email to our DjangoCon Europe 2027 expression of interest form. We’ll make sure to reach out once the time is right.
From The Django weblog at 2024-11-21 17:00:00
The DSF is once again partnering with JetBrains to run the 2024 Django Developers Survey 🌈
Please take a moment to fill it out! It should only take about 10 minutes to complete. It’s an important metric of Django usage, and is immensely helpful to guide future technical and community decisions.
The survey will be open until December 21st, 2024. After the survey is over, we will publish the aggregated results. JetBrains will also randomly choose 10 winners (from those who complete the survey in its entirety with meaningful answers), who will each receive a $100 Amazon Gift Card or a local equivalent.
How you can help
Take a moment to re-share the survey on socials, and with your respective communities? The more diverse the answers, the better the results for all of us.
Thank you for taking the time to contribute to this community effort, and thank you to JetBrains for their consistent support over the years!
From The Django weblog at 2024-11-21 08:00:00
Announcing the 6.x Steering Council elections 🚀
Today, we’re announcing early elections for the Django Software Foundation Steering Council over the 6.x Django release cycle. Elected members will be on the Steering Council for two years, from the end of those elections in December, until April 2027 with the scheduled start of the Django 7.x release cycle.
Why we have early elections
The DSF Board of Directors previously shared Django’s technical governance challenges, and opportunities. Now that the Board elections are completed, we’re ready to proceed with this other, separate election, following existing processes. We will want a Steering Council who strives to meet the group’s intended goals:
-
To safeguard big decisions that affect Django projects at a fundamental level.
-
To help shepherd the project’s future direction.
We expect the new Steering Council will take on those known challenges, resolve those questions of technical leadership, and update Django’s technical governance. They will have the full support of the Board of Directors to address this threat to Django’s future. And the Board will also be more decisive in intervening, should similar issues keep arising.
Elections timeline
Here are the important dates of the Steering Council elections, subject to change:
- 2024-11-21: announcenemnt & opening of voter registration
- 2024-11-26 23:59 AoE (Anywhere on Earth): voter registration closes
- 2024-11-27: opening of Steering Council candidates registration
- 2024-12-04 23:59 AoE: candidates registration closes
- (one week gap per defined processes)
- 2024-12-10: voting starts
- 2024–12-17 23:59 AoE: voting ends
- 2024-12-18: results ratification by DSF Board of Directors
- 2024-12-19: results announcement
Voter registration
If you’re an Individual Member of the Django Software Foundation, you’re already registered to vote. There’s nothing further for you to do. If you aren’t, consider nominating yourself for individual membership. Once approved, you will be registered to vote for this election.
Alternatively, for members of our community who want to vote in this election but don’t want to become Individual Members, you can register to vote from now until 2024-11-26 23:59 Anywhere on Earth, use our form: Django 6.x Steering Council Voter Registration.
Candidate registration
If you’re interested, don’t wait until formal candidate registration. You can already fill in our 6.x Steering Council expression of interest form. At the end of the form, select “I would like what my submissions to this form to be used as part of my candidate registration for the elections”.
Django 6.x Steering Council elections - Expression of interest
Voting
Once voting opens, those eligible to vote in this election will receive information on how to vote via email. Please check for an email with the subject line “6.x Steering Council elections voting”. Voting will be open until 23:59 on December 17, 2024 Anywhere on Earth.
—
Any questions? Ask on our dedicated forum discussion thread, or reach out via email to foundation\@djangoproject.com.
From The Django weblog at 2024-11-17 23:56:08
2025 DSF Board Election Results
The 2025 DSF Board Election has closed, and the following candidates have been elected:
- Abigail Gbadago
- Jeff Triplett
- Paolo Melchiorre
- Tom Carrick
They will all serve two years for their term.
Directors elected for the 2024 DSF Board, Jacob, Sarah, and Thibaud are continuing with one year left to serve on the board.
Therefore, the combined 2025 DSF Board of Directors are:
- Jacob Kaplan-Moss
- Sarah Abderemane
- Thibaud Colas
- Abigail Gbadago*
- Jeff Triplett*
- Paolo Melchiorre*
-
Tom Carrick*
-
Elected to a two (2) year term
Congratulations to our winners, and a huge thank you to our departing board members Çağıl Uluşahin Sonmez, Chaim Kirby, Kátia Yoshime Nakamura, Katie McLaughlin.
Thank you again to everyone who nominated themselves. Even if you were not successful, you gave our community the chance to make their voices heard in who they wanted to represent them.
Please join us in celebrating this news on the forum thread: 2025 DSF Board Election Results or on social media (@djangopproject on X, @django@fosstodon.org on Mastodon, Django Software Foundation on LinkedIn).
From The Django weblog at 2024-11-14 17:00:00
Django’s technical governance challenges, and opportunities
As of October 29th, two of four members of the Django Software Foundation Steering Council have resigned from their role, with their intentions being to trigger an election of the Steering Council earlier than otherwise scheduled, per our established governance processes.
To our departing members, Simon and Adam, thank you for your contributions to Django and its governance ❤️. The framework and our community owes a lot to your dedication, and we’re confident our community will join us in celebrating your past contributions – and look forward to learning about your future endeavors in the Django ecosystem. And thanks to the remaining members, James and Andrew, for their service over the years.
Our governance challenges
Governance in open source is hard, and community-driven open source even more so. We’re proud that Django’s original two Benevolent Dictators For Life (BDFLs) both retired from the role and turned things over to community governance ten years ago now. The BDFL model can provide excellent technical governance, but also has its flaws. So the mantle of technical governance then went on to the Core Developers and the Technical Board (renamed to Steering Council) was introduced.
However, time has revealed flaws in the Steering Council’s governance model and operations. The Steering Council was able to provide decision-making – tiebreaking when the developer community couldn’t lead to consensus – but didn’t provide more forward-looking leadership or vision. Disagreements over how – or if – the Steering Council should approach this part of leadership led us to the current situation, with no functioning technical governance as of a few weeks ago. Even before those recent events, those flaws were also a common source of frustration for our contributors, and a source of concern for Django users who (rightly or not) might have expectations of Django’s direction – such as the publication of a “roadmap” for Django development.
The Django Software Foundation Board of Directors is and was aware of those issues, and recently made attempts to have the Steering Council rectify them, in coordination with other established community members. The DSF Board has tried to be hands-off when it comes to technical leadership, but in retrospect we should have been getting involved sooner, or more decisively. The lack of technical leadership is an existential threat to Django – a slow moving one, but a threat nonetheless. It’s our responsibility to address this threat.
Where we’re heading
We now need new Steering Council members. But we also need governance reform. There’s a lot about the Steering Council that is good and might only need minimal changes. However, the overall question of the Steering Council’s remit, and how it approaches technical leadership for the Django community, needs to be resolved.
We’re going to hold early elections of the Steering Council, as soon as we’ve completed the ongoing 2025 DSF Board elections. Those elections will follow existing processes, and we will want a Steering Council who strives to meet the group’s intended goals:
- To safeguard big decisions that affect Django projects at a fundamental level.
- To help shepherd the project’s future direction.
We expect the new Steering Council will take on those known challenges, resolve those questions of technical leadership, and update Django’s technical governance. They will have the full support of the Board of Directors to address this threat to Django’s future. And the Board will also be more decisive in intervening, should similar issues keep arising.
How you can help
We need contributors willing to take on those challenges and help our community come out ahead. It’s a big role, impactful but demanding. And there are strict, often annoying eligibility rules for the Steering Council.
To help you help us, we’ve set up a form: Django 6.x Steering Council elections - Expression of interest.
If you’re interested in stepping up to shepherd Django’s technical direction, fill in our expression of interest form. We’ll let you know whether or not you meet those eligibility rules, take the guesswork out of the way. You get to focus on your motivation for taking on this kind of high-purpose, high-reward governance role.
Django 6.x Steering Council elections - Expression of interest
How everyone can help
Those elections will be crucial for the future of Django, and will be decided thanks to the vote of our Django Software Foundation Individual Members. If you know people who contribute to the DSF’s mission but aren’t Individual Members already -- use our form to nominate them as Individual Members, so they’re eligible to vote. If you’re that person, do nominate yourself. We consider all contributions towards our mission: advancing and promoting Django, protecting the framework’s long-term viability, and advancing the state of the art in web development.
Any questions? Reach out via email to foundation@djangoproject.com.
From The Django weblog at 2024-11-11 06:01:01
Announcing DjangoCon Europe 2025 in Dublin, Ireland! 🍀
We're thrilled to announce the much-anticipated return of DjangoCon Europe, set to take place in the vibrant city of Dublin, Ireland, in 2025! DjangoCon Europe has been a cornerstone of the Django community, bringing together developers and enthusiasts from all over Europe and beyond to celebrate and advance the Django web framework.
Save the Dates
Mark your calendars for DjangoCon Europe 2025, which will be held from April 23th to 27th. The conference will host a balanced mix of insightful talks, hands-on workshops, and ample opportunities for networking and socialising with fellow Django enthusiasts.
Explore Dublin
With its rich history and vibrant tech scene, Dublin is the perfect backdrop for this year's conference. Dublin's thriving tech community and innovative spirit make it an ideal host for DjangoCon Europe. Plus, the city's lively culture, breathtaking architecture, and friendly locals are sure to provide an unforgettable experience.
Call for Proposals
DjangoCon Europe wouldn't be the same without the insightful and diverse talks contributed by our community. We encourage you to consider submitting a proposal to share your knowledge, experiences, and insights with the Django community. Keep an eye out for the Call for Proposals (CFP) announcement. This is your chance to contribute to the conference program and help make DjangoCon Europe 2025 exceptional.
Get Involved
DjangoCon Europe is a community-driven event, and we rely on the active participation and support of our community members. Here are a few ways you can get involved:
- Attend: Join us in Dublin for a week of learning, networking, and fun.
- Speak: Share your expertise by submitting a talk proposal when the CFP opens.
- Sponsor: Support the conference financially and gain visibility in the Django community (email us at sponsors@djangocon.eu)
- Volunteer: Help us make the conference run smoothly by volunteering your time and skills (https://forms.gle/xmwxssiheMa1oCvPA)
Stay tuned for updates on registration, sponsorship opportunities, and more by following DjangoCon Europe on Twitter and Linkedin.
Stay Informed
To stay up-to-date with the latest DjangoCon Europe 2025 news, visit our website and follow us on Twitter & Linkedin. We will be sharing details about the schedule, speakers, and more in the coming months, so make sure you're on the list!
We can't wait to see you in Dublin for DjangoCon Europe 2025. Get ready for a week of learning, networking, and celebrating all things Django. It's going to be an unforgettable event, and we look forward to sharing this experience with you. Thank you for being a part of our amazing Django community!
See you in Dublin! 🍀
PS: Keep an eye on our social media for special offer we will have during the upcoming holiday season 😉
From The Django weblog at 2024-11-05 06:04:59
Django bugfix release issued: 5.1.3
Today we've issued the 5.1.3 bugfix release.
The release package and checksums are available from our downloads page, as well as from the Python Package Index. The PGP key ID used for this release is Mariusz Felisiak: 2EF56372BA48CD1B.
From The Django weblog at 2024-10-29 02:36:53
Thank you to the 21 individuals who have chosen to stand for election. This page contains their candidate statements submitted as part of the 2025 DSF Board Nominations.
Our deepest gratitude goes to our departing board members, Çağıl Uluşahin Sonmez, Chaim Kirby, Katie McLaughlin; for your contributions and commitment to the Django community ❤️
Those eligible to vote in this election will receive information on how to vote shortly. Please check for an email with the subject line “2025 DSF Board Voting”. Voting will be open until 23:59 on November 15, 2024 Anywhere on Earth.
Any questions? Reach out via email to foundation@djangoproject.com.
All candidate statements ¶
To make it simpler to review all statements, here they are as a list of links. Voters: please take a moment to read all statements before voting! It will take some effort to rank all candidates on the ballot. We believe in you.
- Abigail Gbadago — Accra, Ghana
- Alex Gómez — Barcelona, Spain
- Amir Tarighat — New York
- Ariane Djeupang Jocelyne — Yaounde, Cameroon
- Bhuvnesh Sharma — India
- Chris Achinga — Mombasa, kenya
- Cory Zue — Cape Town, South Africa
- David Vaz — Porto, Portugal
- Gabriel Arias Romero — Mexico
- Jeff Triplett — Lawrence, KS USA
- Julius Nana Acheampong Boakye — Accra Ghana
- Keanya Phelps — Chicago IL US
- Kevin Renskers — The Netherlands
- Kátia Yoshime Nakamura — Berlin, Germany
- Lilian — United States
- Marcelo Elizeche Landó — Paraguay
- Paolo Melchiorre — Italy
- Patryk Bratkowski — Patryk Bratkowski
- Priya Pahwa — India, Asia
- Tom Carrick — Amsterdam, Netherlands
- Vitaly Semotiuck — Rzeszow, Poland
Abigail Gbadago Accra, Ghana ¶
Hi,
I am Abigail(Afi), a DSF member who has contributed to the Django Ecosystem for about four years. I have held the following positions in the community:
- Leadership council member for Black Python Devs (current)
- Open Source Program Manager for Black Python Devs - I am managing 39 of our community members make their first steps in open source (current)
- Programs Team member for DjangoCon US 2024
- Contributed in organizing Django Girls Zanzibar (2023) ahead of the first DjangoCon Africa, co-organiser of Django Girls in Kwahu-Ghana (2019), and coach at Django Girls Ho-Ghana; 2018, 2024 and Zanzibar (2023)
- DjangoCon US Speaker 2023, you can watch my talk here: Strategies for Handling Conflicts and Rollbacks with Django
I have extensive experiences with the community, which have contributed to my growth, and I believe serving on the board is a good way to give back. As such, I am positive that I would bring a refreshing perspective to the board and be a good match for community integration with Django.
As a board member, I plan to increase interactions between the DSF and its user base by providing an official mailing list highlighting non-technical and technical updates that will keep Django users up-to-date with current developments and build a relationship with our user base. Through this, I aim to gather djangonauts from everywhere to support creating the next leaders of the Django community.
In addition, I would like to use my experience in fostering Strategic Partnerships and Fundraising in the nonprofit space to help the DSF Fundraising WG find more sponsors for the DSF. While working with a community, I fostered vital partnerships with about 10 organisations, which contributed to reaching our Fundraising and Partnerships goal despite most organisations slashing nonprofit donations.
As such, I believe those skills, coupled with my community experience, will contribute to the growth of the Django Community, especially when we attract sponsors and increase their efforts and visibility on our social media.
Alex Gómez Barcelona, Spain ¶
I began developing with Django at version 1.11 and have been an avid user since. I am a member of Djangonaut Space and was previously a Djangonaut in the program. I’m also an active member of Python Spain and Python Barcelona and have coached at multiple DjangoGirls workshops.
I believe the next few years will be crucial for Django's future. It’s important for us to remain relevant and ensure that Django continues to be a choice for new projects, not just for maintaining existing ones.
The DSF needs an executive director, we’ve reached the limit of what a volunteer board can do or be asked to do. This is my first and main priority for 2025 and I believe without such a change we will struggle to meaningfully advance.
An obstacle to enacting an executive director is the need to expand the foundation's funding and pool of sponsors, and I propose that one of our most effective ways to achieve this is by expanding our communications. Too little of the Django user base is reached by the DSF and other non-official Django communications, leaving a wide userbase who may be very willing to support the project but do not know they can.
In support of these goals, I will also make the website a priority. We’re years into attempting to revamp it, the last successful attempt being a decade ago. The website working group is not yet finalized, an executive director will help us push this forward.
The DSF needs fresh perspectives, and with your support I believe I will bring positive changes to the Django community.
Amir Tarighat New York ¶
Hi DSF board members! My name is Amir Tarighat and I’m a software engineer and long time user of Django. I think since version ~1.8. I live in NYC.
I’m 3x VC backed founder and an active investor, currently I am the CEO of Agency which is a Y Combinator backed company.
I’m an expert in cybersecurity and compliance, and have served on several boards including one non-profit and an elected neighborhood council position.
I would love to serve the Django community and help grow its use by helping with fundraising, community events and sponsorships, and with anything security or compliance related. I’d also love to help with anything startup related.
Ariane Djeupang Jocelyne Yaounde, Cameroon ¶
I am Ariane Djeupang, a junior project manager, Community builder and freelance Machine Learning Engineer from Cameroon.
As a young Black African woman in STEM from the francophone region of Africa and an active DSF member, I’ve dedicated my career to fostering inclusivity and representation in the tech community and I am confident that I bring a unique perspective to the table. My extensive experience organizing major events like:
- DjangoCon US 2024,
- DjangoCon Africa 2023, and
- PyCon Africa 2020 (as a volunteer) | 2024 (as an IOC member ) has equipped me with the skills and insights needed to drive inclusivity and community engagement.
My journey has been fueled by a passion for diversity and representation. I have seen firsthand the incredible impact that inclusive environments can have on underrepresented communities, especially in Africa, and I am dedicated to amplifying these voices within the Django ecosystem. As a mentor in the both the Python and the Django Community, as well as a mentor and community manager at BEL'S AI Initiative in Cameroon, I have empowered many young technologists, fostering a supportive and inclusive community.
I aim to bridge the gap between the DSF Board and our vibrant African community, ensuring that our unique perspectives and needs are heard and addressed. I am committed to being the voice of Africa within the board and representing the board within my community. By voting for me, you are supporting a vision of inclusivity, innovation, and growth for the Django community.
To achieve this, I plan to:
- Launch official DSF multilingual mentoring programs, targeted at underrepresented groups from Africa, with plans to expand globally.
- Introduce the Django Diversity Incubator, offering resources, workshops, scholarships, and global hackathons to underrepresented groups around the world.
- Create a Django Open Source Fellows interns role, to welcome new people into code and non-code contributions.
Thank you for your consideration.
Bhuvnesh Sharma India ¶
Hi everyone! I'm excited to throw my hat in the ring for the DSF Board of Directors.
To me, there appears to be a critical component that could benefit from increased attention: social media and marketing. And I believe It's time we start giving Django the social media attention it deserves.
Let's be real: If we master this social media game, Django's reach will explode, and the entire ecosystem will thrive.
The more we boost Django’s presence online, the more up-and-coming developers will flock to it. And with that surge in usage comes the rise of Django-focused communities—stronger, more engaged, and constantly growing.
Now, here’s where it gets exciting: more visibility leads to a snowball effect.
- Visibility drives growth: More eyes on Django → more users → more contributors
- Quality fuels adoption: More contributors → better Django → increased commercial usage
- Success attracts support: Increased usage → more sponsors → resources for further expansion
Then guess what? We loop back to the start: Django gets bigger, stronger, and better.
Here are few-of-many pointers that I am aiming to start with during my tenure as a board member:
- Boost Django's presence in Asia through targeted outreach and events.
- Launch Django Ambassadors program to recognize influential community members.
- Facilitate non-coding contributions to Django (design, content, event organizing).
- Create a volunteer layer between the DSF and interested individuals who are eager to contribute to specific working groups (WGs).
- Produce engaging social media content similar to Feature Fridays.
I am highly motivated to lead Django’s social media and marketing as a Board member. I have more high-level plans and ideas in mind, and I’m focused on finding the right time and people for their execution. Additionally, I would represent the Asia region and bring valuable diversity in the DSF board. You can read more about my plans in the blog here: Making Django Unstoppable: My Plan to Boost Visibility and Drive Growth
Now talking about myself, I am a django core contributor and have been involved with DSF for around past 1.5 years as a DSF member. I also did Google Summer of Code with Django in 2023 and mentored in Google Summer of Code 2024 with Django. Apart from code contributions I have contributed to Django in various others ways:
- I am Co-Chair at the social media WG at DSF. (all the Feature Fridays posts are created by me :) )
- I was a navigator at Djangonaut Space’s first session.
- I recently started a community called Django India with an aim to popularize Django in India.
Excited for what lies ahead!
Chris Achinga Mombasa, kenya ¶
My journey as a software developer has been profoundly shaped by the power of community. From the outset, participating in developer meetups and events, particularly DjangoCon Africa, has not only strengthened my technical skills but also reshaped my understanding of growth—both personal and professional.
Driven by a desire to make a meaningful difference, I am pursuing a position on the Django Software Foundation Board. I bring a commitment to promoting diversity, inclusivity, and accessibility within the Django ecosystem. As a vocal advocate for African and minority communities, I believe my presence on the Board would add a valuable perspective to the DSF’s mission, ensuring that emerging developers from underrepresented backgrounds find opportunities, resources, and community support in Django.
My experience with the Swahilipot Hub Foundation, a Kenyan NGO supporting youth along the coast, has equipped me with essential skills in community engagement and in applying technology for social good. Through this role, I have developed Django-based solutions that empower community self-management—an experience that has reinforced my belief in Django’s potential to uplift communities around the globe. On the DSF Board, I aim to serve not only as a representative for these communities but also as a mentor and technical guide.
Cory Zue Cape Town, South Africa ¶
I’m running for the board because I love Django, I’ve built my career on it, I want to see it succeed for another 20 years, and I think I can help.
My background is as a Django user and educator. I’ve built several successful products on Django, spoken at multiple DjangoCons and PyCons and have published many popular articles and videos about using Django. I currently run a Django boilerplate product that helps people build apps and start businesses on top of Django. I’m also a member of the DSF and the social media working group.
My platform is relatively simple. I don’t want Django to get left behind. I’ve seen old frameworks like Rails and Laravel continually reinvent themselves, bringing new cohorts of web developers into the fold, while Django has largely stayed the same.
Part of the issue is Django’s reluctance to adopt modern technologies— with better front end being at the top of my list. But I don’t have unrealistic aspirations of adding HTMX, Tailwind, or React to Django, so much as starting the conversation about how the Django ecosystem can have a better story for people who want to use those things.
The other part—and the part I hope to help with more—is cultural. Specifically, getting Django to do a better job at selling itself. This means working harder to pitch and position Django as a great, modern framework for building apps. As well as creating more opportunities and incentives for funding Django.
If elected, I’ll try to be a voice on the board that pushes Django forwards, while understanding that I will often get pushed back. Let’s keep Django great for another 20 years!
David Vaz Porto, Portugal ¶
I am a software developer with over 20 years of experience and have been passionate about Django since 2007, starting with version 0.96. Over the years, I have not only built my career around Django and Python, but I have also actively contributed to expanding the Django community. My journey has led me to found a consultancy firm focused on these technologies, and I’ve dedicated my efforts to bringing new developers into the community and fostering its growth.
In 2019, during DjangoCon Europe in Copenhagen, I strongly desired to take my community involvement to the next level. I proposed to organize DjangoCon Europe 2020 in Portugal. Though the pandemic reshaped those plans, I co-organized the first virtual-only DjangoCon Europe in 2020, another virtual edition in 2021, and the first hybrid event in 2022. Our 2022 edition set a new record, with over 500 in-person attendees and 200+ online participants. The experience has been gratifying, and I continue to be actively involved in the community by co-organizing DjangoCon Europe 2024 in Vigo, Spain, and preparing for DjangoCon Europe 2025 in Dublin, Ireland.
In addition to my work with Django, I am deeply committed to the growth of the Python community in Portugal. In 2022, I co-founded PyCon Portugal, intending to host the conference in a different city each year to maximize its reach and impact. The first edition in Porto succeeded, followed by Coimbra in 2023, which attracted participants from over 25 countries. By the time of this election, PyCon Portugal 2024 in Braga will have concluded, furthering our goal of uniting and strengthening the Portuguese Python community.
I am enthusiastic, committed, and pragmatic. In every initiative I’ve taken, I strive to make a positive and meaningful impact, influencing and empowering those around me. My experience organizing large-scale events, building communities, and fostering collaboration can be valuable to the Django Software Foundation.
I look forward to contributing my skills and dedication to help guide the DSF’s efforts in the years ahead.
Gabriel Arias Romero Mexico ¶
solo soy un fan y me encanta el framework
Jeff Triplett Lawrence, KS USA ¶
I'm running for the Django Software Foundation board of directors to help serve the community and reshape the board and foundation.
The key to making the DSF more sustainable is the stability that hiring an Executive Director brings. From day-to-day communications to supporting the Django Fellows to improving our ability to fundraise, everything revolves around having someone whose job is to run and support the foundation. I believe an ED will help Django get a seat to more conversations involving open source and web standards that we get passed over today.
I bring over two decades of non-profit experience, including co-founding DEFNA (the other Django non-profit) and serving on the Python Software Foundation, including leadership roles (Treasurer and Vice Chair). I have also helped organize DjangoCon US for over a decade, and we have seen many community members and leaders grow through that community-building experience. I'm an advisor for Black Python Devs and have been a mentor through the Djangonaut Space project.
I want to revise and revisit our sponsorship plans and fundraising goals. They have not changed much over the years despite companies' needs changing significantly. We did this with the PSF, and it increased the number of developers in resident roles (the PSF's version of Fellows) we could fund. It's time for the DSF to revise our plans.
I want to revise our approach to DjangoCons and other "why aren't they called DjangoCon" community events. Why aren't more of these promoted or listed through the Django website?
I firmly believe in the Campsite Rule: "Always leave the campground cleaner than you found it." I feel good about the mark I have left on the Django and Python communities over this past decade, and I am happy to serve the Django community in a more significant role if given the opportunity.
Julius Nana Acheampong Boakye Accra Ghana ¶
I'm excited to nominate myself for the Django Software Foundation's Board of Directors. With 4 years of experience in the tech industry, I've seen the impact Django can have on a project's success. I've contributed to the community through speaking at conferences, organizers global DjangoCon conference , teaching Django on campuses and am committed to using my skills to help the board make informed decisions.
My goals are to increase diversity and inclusion within the community and improve the overall health and stability of the Django project. If elected, I promise to be an active and engaged member, always putting the needs of the community first.
Thank you for considering my nomination. I'm excited to serve the Django community and contribute to its continued success.
Keanya Phelps Chicago IL US ¶
I am excited to submit my candidacy for the Django Software Foundation (DSF) board. Having transitioned into software development after a career change, I feel like I bring a unique perspective to the challenges and opportunities within the Django ecosystem. I am deeply passionate about diversity, inclusion, and mentorship,
My journey into tech by way of Django, has been shaped by collaboration, continuous learning, and the support of mentors, which is why I am eager to give back to the Django community. I am particularly enthusiastic about contributing to initiatives that promote diverse voices and create inclusive environments where everyone feels empowered too contribute and to leave things better than how they found them.
In addition to my commitment to diversity, I am driven by a love of running projects, research, and collaboration.
As a member of the DSF board, I would bring fresh ideas, a collaborative spirit, and a dedication to making Django an even more inclusive, forward-thinking community.
Kevin Renskers The Netherlands ¶
I’ve been using Django since 2009, and apart from blogging about Django for 15 years, I’ve always been mostly on the sidelines. It’s about time to get more involved with the community, share my experience and expertise, offer my time. I’m mainly interested in the enforcement of the Django trademark and code of conduct, ensuring a healthy community.
Kátia Yoshime Nakamura Berlin, Germany ¶
I am a Software Engineer with over 10 years of experience, working with Django both personally and professionally since 2015. My journey with Django started in 2015 when I attended my first Django Girls event in Brazil. Since then, I’ve built my career around Django, contributing to the community while actively attending, participating in and helping organize Python and Django conferences/events.
In 2018 and 2019, I helped organize PyCon Balkan in Belgrade (Serbia). Since 2016, I've coached and organized Django Girls workshops around the world, including in Rio de Janeiro (Brazil), Budapest (Hungary), Brno (Czechia), Belgrade (Serbia), Porto (Portugal), and Vigo (Spain).
Over the past few years, I've been deeply involved in DjangoCon events, particularly in Europe, where I’ve volunteered and organized Django Girls workshops.
Since 2020, I’ve had the privilege of serving as a board member of the Django Software Foundation (DSF). The pandemic brought us significant challenges, but we've built a resilient team, eager to push Django forward with fresh perspectives and new solutions. I’ve also been involved in the early efforts to shape a long-term plan for future conferences across Europe, focusing on engaging more organizers and selecting host teams earlier - up to two years in advance - for better flexibility and planning. However, there's still more we aim to achieve.
I’d love to keep supporting our Django community as a board member, promoting more diversity and inclusiveness while encouraging collaboration and exciting initiatives.
Lilian United States ¶
I’m Lilian 👋, a DSF Member, Django ORM contributor, and Djangonaut Space Coordinator.
Lots of talent is locked up in the industry simply due to gatekeeping. Let’s improve processes and tap into this pool of talent, so we can move Django forward in the right direction.
The DSF should do more to facilitate the connection between newcomers and maintainers. Let’s create a space where we provide the support system they need to collaborate productively, for technical teams and working groups alike.
We also need to facilitate bolder decision making. For the framework: sponsored features and fundamentals like async support, JIT, type annotations. For the Foundation: more transparency, an Executive Director, a newsletter.
How can we achieve this?
- Coordination with the Steering Council for tech decisions, via a Board Liaison role.
- Gather feedback from program organizers to determine gaps that need support.
- Facilitate collaboration among newcomers and maintainers.
- Better marketing: such as promoting community initiatives.
- Documented playbooks! To scale the Working Groups concept.
Frustrated by the status quo in the industry, and yet inspired by changes happening to Django, I’m motivated to help more people get involved with Django as code contributors and leaders.
Marcelo Elizeche Landó Paraguay ¶
Why I’m Running
Before assisting to DjangoCon US, I saw Django as just part of the larger Python community. But seeing how this community goes above and beyond to support both longtime members and newcomers changed that for me. When others suggested I run for the board, it felt like a way I could give back and share what makes Django special on a global scale.
A Bit About Me
I co-founded and organized the Python Paraguay community, starting with our first PyDay in 2015, which was a huge success and sparked a lasting momentum. Since then, I’ve organized meetups, events, workshops, and grown our community to almost two thousand members—the most active tech group in Paraguay! I also used Django for projects that make a difference: AyudaPy.org, a mutual aid platform during COVID-19 (which I presented at DjangoCon US 2022), and Lista Hũ, a tool to protect against scammers, both of which highlight Django’s potential for social good.
Ideas for Django
- Learning Curve: Improving the Django tutorial and expanding learning resources can make Django more accessible and less intimidating for newcomers. Creating more comprehensive, step-by-step guides will empower new developers and ease their journey into Django.
- Supporting Global Accessibility: Expanding Django’s reach by focusing on language accessibility and gathering regional feedback is key. Adding questions to the Django Developers Survey on preferred languages and translation quality could help the community prioritize localization efforts, ensuring developers worldwide feel supported in their native languages.
I believe this community is on the right path, and it would be an honor to contribute as a board member
Paolo Melchiorre Italy ¶
The Django community is the best one I could be a part of, and since I started using Django, I have seen wonderful initiatives born and thrive within it (e.g., Django Girls+, Djangonaut Space, Django Fellow). We should bring this momentum to other areas as well: fundraising, the website, development sprints, content translations, self-promotion (e.g., release videos), multimedia content (e.g., videos, books, podcasts, photos, …), feedback from Django users, Django's environmental impact.
I think that the Django Software Foundation has the potential to facilitate and promote these initiatives. It also has the authority to relate to other Open Source communities, to seek synergies, and with big corporations, to grow from an economic point of view, being able to pay more people (e.g., Django Fellows, Directors, UI/UX experts, …)
I believe I can give a boost to these initiatives, with my experience in the Django community, and with an original point of view in the Board, as a member of the Italian Python community, and founder of a local community.
Patryk Bratkowski Patryk Bratkowski ¶
Hello, Djangonauts!
If you are one of the regulars on the official Django Discord server, my passion and dedication to both the Django community and framework should be no secret. As a helper, I have helped countless other developers use Django successfully. As a moderator, I do my best to ensure that we have a community that we can all be proud to consider our own, regardless of our background. An environment that is inclusive, diverse, and welcoming. To me, it feels like home, and I hope you all feel the same way.
For those I haven't yet had the pleasure to meet on Discord or elsewhere, I hope we do soon.
About me:
- I have been building on the web since the Geocities days, and have over 17 years of professional experience, meaning I know how to get things done.
- I have experience building and managing communities, including forums and subreddits, meaning I can readily help with the technical and human aspects.
- I am proactive, and lucky enough to have a lot of flexibility in how I spend my time, meaning I can help turn decisions into action.
- I am open-minded, and eager to learn, meaning I am looking forward to working for the community, with the board, rather than wanting to impose my own ideas.
- I am a polyglot speaking more than four languages fluently, meaning I feel connections to others, regardless of geographical borders.
If elected, my goals will be:
- Collaborating with the other board members. Django's popularity and stability is a testament to the fantastic work current and past board members and developers have done, and while I may have my own ideas, I would first want to know more about any backlog, plans, or other issues that need to be resolved rather than bring about drastic changes.
- Efficiently implementing board decisions. While plans may sometimes forcibly change, they at least need someone to take charge of them. I am happy to lend my technical expertise when required, and deal with other roadblocks.
- Community representation. As a fairly visible member of the Django community, I am looking forward to ensuring the community feels represented and heard, and seeing what more we can do to help the community grow.
- Increase representation of non-English speakers. While English is the de facto business language, there are other large markets that would benefit from better support.
As Django nears twenty years of existence, becoming a board member certainly gives us some big shoes to fill, but between my passion, this amazing community's support, and the time I can dedicate to the position, I am confident that I can help the community continue to thrive, make a tangible difference, and better serve the community we all know and love.
Best regards, and best of luck to all the other applicants,
Pat
Priya Pahwa India, Asia ¶
Balancing code, community, and collaboration, I am actively holding the following position of responsibilities:
- Co-Chair of the Fundraising Working Group at the Django Software Foundation
- Session Organizer of Djangonaut Space
- Software Development Engineer (Django backend and Infra) at a wealth tech startup.
- 2023 SWE intern (Django techstack) under the GitHub Octernships program.
Having had the experience of building inclusive student tech communities and organizing numerous meetups and global hackathons as a GitHub Campus Expert, I can bring fresh perspectives to the DSF Board and bridge the currently huge gap between the student community and the potential Django leadership positions. As a DSF Board of Directors, I will push for initiatives to:
- Build a Django Evangelist Program or a Django Developer Advocacy Working Group
- Introduce a dedicated Django track at student hackathons to increase the framework’s visibility amongst budding developers.
- Establish a robust DEIB (Diversity, Equity, Inclusion, and Belonging) framework in both theory and practice for DSF
- Include subtle subconscious yet impactful details, such as designing the assets of custom merchandise—like stickers—that represent diverse races and backgrounds to ensure everyone feels valued.
- Continue driving fundraising efforts to engage potential corporate sponsors with a structured funding roadmap and prospectus that aligns with our community needs.
- Develop a one-stop-solution DSF community handbook - an easily accessible guide for newcomers
I’m dedicated to bringing the voice of the Asian Indian community to the DSF Board. The lack of DjangoCons and a strong local Django network in this region limits talented individuals from essential growth opportunities. I aim to foster a sense of belonging at the table, expand rewards in exchange for volunteering, and ensure the Django community thrives everywhere, especially in underserved areas with psychological safety and welcoming ways for one and all.
Tom Carrick Amsterdam, Netherlands ¶
Hello! For those that don't know me, I've also been actively contributing features for most of the last decade. I help run the Discord, the accessibility team, and I'm on the fundraising working group. If that sounds like a lot of time commitment already, you're right. If you vote for me I might have to become dormant in some other roles.
But I don't really want to talk about my perspective as a contributor, I want to talk about my experience as a user. I've been using Django since around 2008. We have great batteries for 2008. For 2024? I am not so sure. I feel like we are missing things like:
- Built in 2FA with WebAuthn / passkeys.
- Better serialization to make APIs without needing a second framework.
- A better frontend story, whether that's tutorials on integrating frameworks or how to use simpler solutions like HTMX, template components (or all of the above).
- A more modern, accessible admin interface with better UX.
- Simpler project setup for small projects, including deployment and static files (integrating white noise?).
- (type hints maybe?)
- I could increase the size of this Wishlist by several factors and still not be done.
The reason I believe we're missing these things is simple (and possibly wrong). Django is getting bigger, more mature, and prioritises stability. These are all great things, but they do slow down development when almost all new features are contributed by people volunteering their time.
To fix this, Django needs money, which is why I joined the fundraising group, and then there is the question of spending that money. And for the me the priorities are clear:
- Spend money to make more money.
- Hire more fellows and widen their remit to contributing new features.
And that's my "manifesto", if you like.
Vitaly Semotiuck Rzeszow, Poland ¶
Your move now
That’s it, you’ve read it all 🌈! Be sure to vote if you’re eligible, by using the link shared over email. To support the future of Django, donate to the Django Software Foundation on our website or via GitHub Sponsors.
From The Django weblog at 2024-10-16 15:27:59
Announcing weekly DSF office hours
For the last year, Thibaud Colas and I have had a weekly DSF co-working session — we get on a video call and spend an hour quietly working together on DSF things. It's worked well to help us carve out time to work on DSF initiatives, so we'd like to expand into an open-to-everyone weekly "office hours" format.
These will be Wednesdays at 6PM UTC (convert to other time zones). (Yes, that means the first one will be in just about 4 hours, short notice I know, so maybe mark it down for next week.)
All you need to do is bring something DSF-related to work on. This is intentionally broad, as long as it's vaguly DSF-related you're welcome to come. It's not a general-purpose Django coding session (you're welcome to be writing code but it should be related the DSF, e.g. working on djangoproject.com or something.)
This week and next, we'll probably be focusing on nominations for the DSF Board -- nominations close October 25th.
For now, we're deliberately not publishing the video call information publicly — we're a bit worried about spammers and scammers. So if you want to join, you'll need to contact the board, or someone on the board, to get the info. You can use the DSF contact form, and anyone's welcome to contact me directly: — email jacob@djangoproject.com, Signal jacobian.01, or @jacob@jacobian.org on Mastodon.
(Yes, this introduces some friction which is at odds with the "everyone's welcome" ethos. If/when we figure out a better way to moderate these calls, we'll change this.)
I look forward to seeing you there!
From The Django weblog at 2024-10-09 04:26:40
Why Django supports the Open Source Pledge
We at the Django Software Foundation are pleased to share that Sentry, alongside other partners, has launched the Open Source Pledge — an initiative designed to address sustainability challenges in open source.
The Open Source Pledge is a commitment for member companies to pay OSS maintainers meaningfully for their work. When maintainers are adequately supported, they can better sustain their projects, ensuring the growth, stability, and security of the broader ecosystem.
The sustainability challenge in the Django community
In our community and OSS at large, the challenge is real and significant. Django packages are often maintained by small teams or even individuals, often unpaid. As the demands on these projects grow, so too does the pressure on the maintainers. And without financial support, maintainers often move on without a clear succession plan. The potential failure of these projects not only impacts the developers involved but also the thousands of companies and millions of users who rely on these critical pieces of infrastructure.
Here are a few assorted examples from Django packages in the top 10 by download counts:
- Is DRF still considered alive?, Moving REST framework forward
- Lots of open PRs with no feedback or action
- Recruiting maintainers
- We need more roadies in jazzband
The case for joining the pledge
The Open Source Pledge is simple but impactful: member companies commit a minimum of $2,000 per year, per developer on staff, to support open source maintainers. Additionally, companies are encouraged to publish an annual report detailing their payments, creating transparency and accountability within the community.
We encourage companies of all sizes to join the Pledge and contribute to the sustainability of the software we all depend on. By making a financial commitment, you are not just supporting maintainers—you are investing in the stability, security, and growth of the entire tech ecosystem.
If you're interested in joining the Open Source Pledge or learning more about the sustainability issues facing OSS, please visit the initiative’s page. Together, we can build a stronger, more sustainable open source future. And if you believe in this cause, we encourage you to share this post to help broaden awareness and inspire further commitments from peers and partners.
From The Django weblog at 2024-10-08 12:00:00
Django bugfix release issued: 5.1.2
Today we've issued the 5.1.2 bugfix release.
The release package and checksums are available from our downloads page, as well as from the Python Package Index. The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E.
From The Django weblog at 2024-09-25 17:03:45
Nominations are open for the 2025 Django Software Foundation Board of Directors.
In 2023 we introduced a staggered term for directors. Of our 7 directors, there are 4 positions currently open, with each position serving for two years.
Decisions around the 2025 officer roles will be made during the meeting of the new board. You don’t need to specify which position you are nominating for.
As you know, the Board guides the direction of the marketing, governance and outreach activities of the Django community. We provide funding, resources, and guidance to Django events on a global level. Further we provide support to the Django community with an established Code of Conduct and make decisions and enforcement recommendations for violations. We work with our corporate and individual members to raise funds to help support our great community.
In order for our community to continue to grow and advance the Django Web framework, we need your help. The Board of Directors consists of seven volunteers who are elected to two year terms. This is an excellent opportunity to help advance Django. We can’t do it without volunteers, such as yourself. Anyone including current Board members, DSF Members, or the public at large can apply to the Board. It is open to all.
2025 DSF Board Nomination Form
If you are interested in helping to support the development of Django we’d enjoy receiving your application for the Board of Directors. Please fill out the 2025 DSF Board Nomination form by October 25, 2024 Anywhere on Earth to be considered.
If you have any questions about applying, the work, or the process in general please don’t hesitate to reach out via email to foundation@djangoproject.com.
Thank you for your time and we look forward to working with you in 2025.
The 2024 DSF Board of Directors.
From The Django weblog at 2024-09-23 12:43:13
PyCharm & Django Campaign 2024 - encore
The Django Software Foundation's biggest fundraising event of the year is here!
Get 30% off PyCharm, Support Django
Each year, our friends at JetBrains, the creators of PyCharm, run an incredible deal. You get a 30% discounted year of PyCharm, AND the DSF gets 100% of the money. Yes, 100%! It's making a donation and directly getting a great product in return! This is available for new users, and those who had used PyCharm in the past, stopped, and want to try again.
The fundraiser
The fundraiser started during DjangoCon Europe in June, and is now back on from September 22nd to October 6th. Buy PyCharm and support Django!
In the past, JetBrains through the PyCharm fundraiser has provided approximately one quarter of the Django Software Foundation's budget!
Donations like this fundraiser allow the DSF to function. Our two wonderful Fellows, Natalia Bidart and Sarah Boyce keep Django running smoothly, picking up pieces that would otherwise not happen.
The other side of the DSF is our support for Django groups across the globe. We supported every DjangoCon, particularly with donating funding towards opportunity grants for more people to be able to attend these conferences. The DSF also supports smaller events around the world, including DjangoGirls events.
PyCharm
Finally, I want to tell you about PyCharm itself.
PyCharm is an integrated development environment (IDE) that helps professional Python web developers be more productive, be more confident, and write better code. It supports the full Python web workflow out of the box, including popular Python web frameworks, such as Django, frontend technologies, and databases.
Here are the main benefits of using PyCharm in your Django development:
- Django (including templates), Flask, FastAPI
- Database management (Postgres, Redis)
- JS, React, Node.js, TailwindCSS
- Built-in HTTP Client and endpoint tools
Get Django work done with PyCharm, a powerful IDE tailored for Django web development!
Consider this the easiest charitable donation you will ever make, when you get such a great product in return!
Get 30% off PyCharm, Support Django
Other ways to donate
If you would like to donate in another way, especially if you are already a PyCharm customer, here are other ways to donate to the DSF:
- On our website via credit card
- Via GitHub Sponsors
- For those able to make a larger donation, particularly corporate sponsors ($2000+), more information is here: Corporate membership
From The Django weblog at 2024-09-18 13:00:00
Last call for DjangoCon US 2024 tickets!
DjangoCon US starts next week in Durham, NC on September 22nd!
If you aren't able to join in person, please consider purchasing an online ticket: https://ti.to/defna/djangocon-us-2024
The conference is full of a variety of talks with excellent keynote speakers! It's shaping up to be an event you'll want to experience live.
If you'd like to learn more about DjangoCon US visit them at their website or reach out to them at hello@djangocon.us.
From The Django weblog at 2024-09-16 06:01:01
Nominate a Djangonaut for the 2024 Malcolm Tredinnick Memorial Prize
Hello Everyone 👋 It is that time of year again when we recognize someone from our community in memory of our friend Malcolm.
Malcolm was an early core contributor to Django and had both a huge influence and impact on Django as we know it today. Besides being knowledgeable he was also especially friendly to new users and contributors. He exemplified what it means to be an amazing Open Source contributor. We still miss him to this day.
The prize
The Django Software Foundation Prizes page summarizes it nicely:
The Malcolm Tredinnick Memorial Prize is a monetary prize, awarded annually, to the person who best exemplifies the spirit of Malcolm’s work - someone who welcomes, supports, and nurtures newcomers; freely gives feedback and assistance to others, and helps to grow the community. The hope is that the recipient of the award will use the award stipend as a contribution to travel to a community event -- a DjangoCon, a PyCon, a sprint -- and continue in Malcolm’s footsteps.
Please make your nominations using our form: 2024 Malcolm Tredinnick Memorial Prize.
We will take nominations until Monday, September 30th, 2024, Anywhere on Earth, and will announce the winner(s) soon after the next DSF Board meeting in October. If you have any questions please reach out to the DSF Board at foundation@djangoproject.com.
From The Django weblog at 2024-09-06 17:33:15
Djangonaut Space - New session 2024
We are thrilled to announce that Djangonaut Space, a mentorship program, is open for applicants for our next cohort!
Djangonaut Space is holding a third session this year! This session will start on October 14th, 2024. We are accepting applications until September 14th, 2024. More details can be found in the website.
Djangonaut Space is a free, 8-week group mentoring program where individuals will work self-paced in a semi-structured learning environment. It seeks to help members of the community who wish to level up their current Django code contributions and potentially take on leadership roles in Django in the future.
“I signed up for this program with the goal of starting my journey as a contributor, but I ended up gaining so much more. In this community, I found incredible people who not only guide you toward solutions but also encourage and celebrate every achievement along the way.” - Raffaella, Djangonaut
If you have questions, they are holding an AMA session on Zoom next week. See their social media account for more details:
From The Django weblog at 2024-09-03 12:00:00
Django security releases issued: 5.1.1, 5.0.9, and 4.2.16
In accordance with our security release policy, the Django team is issuing releases for Django 5.1.1, Django 5.0.9, and Django 4.2.16. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2024-45230: Potential denial-of-service vulnerability in django.utils.html.urlize()
urlize and urlizetrunc were subject to a potential denial-of-service attack via very large inputs with a specific sequence of characters.
Thanks to MProgrammer for the report.
This issue has severity "moderate" according to the Django security policy.
CVE-2024-45231: Potential user email enumeration via response status on password reset
Due to unhandled email sending failures, the django.contrib.auth.forms.PasswordResetForm class allowed remote attackers to enumerate user emails by issuing password reset requests and observing the outcomes.
To mitigate this risk, exceptions occurring during password reset email sending are now handled and logged using the django.contrib.auth logger.
Thanks to Thibaut Spriet for the report.
This issue has severity "low" according to the Django security policy.
Affected supported versions
- Django main branch
- Django 5.1
- Django 5.0
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.1, 5.0, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2024-45230: Potential denial-of-service vulnerability in django.utils.html.urlize()
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
CVE-2024-45231: Potential user email enumeration via response status on password reset
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.1.1 (download Django 5.1.1 | 5.1.1 checksums)
- Django 5.0.9 (download Django 5.0.9 | 5.0.9 checksums)
- Django 4.2.16 (download Django 4.2.16 | 4.2.16 checksums)
The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum, nor via the django-developers list. Please see our security policies for further information.
From The Django weblog at 2024-08-28 13:59:23
Could you host DjangoCon Europe 2026? Call for organizers
We are looking for the next group of organizers to own and lead the 2026 DjangoCon Europe conference. Could your town - or your football stadium, circus tent, private island or city hall - host this wonderful community event?
DjangoCon Europe is a major pillar of the Django community, as people from across the world meet and share. This includes many qualities that make it a unique event - unconventional and conventional venues, creative happenings, a feast of talks and a dedication to inclusion and diversity.
Hosting a DjangoCon is an ambitious undertaking. It's hard work, but each year it has been successfully run by a team of community volunteers, not all of whom have had previous experience - more important is enthusiasm, organizational skills, the ability to plan and manage budgets, time and people - and plenty of time to invest in the project.
For 2026, we want to kickstart the organization much earlier than in previous years to allow more flexibility for the organizing team, and open up more opportunities for support from our DjangoCon Europe support working group.
Step 1: Submit your expression of interest
If you’re considering organizing DjangoCon Europe (🙌 great!), fill in our DjangoCon Europe 2026 expression of interest form with your contact details. No need to fill in all the information at this stage if you don’t have it all already, we’ll reach out and help you figure it out.
Express your interest in organizing
Step 2: We’re here to help!
We've set up a DjangoCon Europe support working group of previous organizers that you can reach out to with questions about organizing and running a DjangoCon Europe.
The group will be in touch with everyone submitting the expression of interest form, or you can reach out to them directly: european-organizers-support@djangoproject.com
We'd love to hear from you as soon as possible, so your proposal can be finalized and sent to the DSF board by October 6th 2024. The selected hosts will be publicly announced at DjangoCon Europe 2025 by the current organizers.
Step 3: Submitting the proposal
The more detailed and complete your final proposal is, the better. Basic details include:
- Organizing committee members: You won’t have a full team yet, probably, naming just some core team members is enough.
- The legal entity that is intended to run the conference: Even if the entity does not exist yet, please share how you are planning to set it up.
- Dates: See “What dates are possible in 2026?” below. We must avoid conflicts with major holidays, EuroPython, DjangoCon US, and PyCon US.
- Venue(s), including size, number of possible attendees, pictures, accessibility concerns, catering, etc.
- Transport links and accommodation: Can your venue be reached by international travelers?
- Budgets and ticket prices: Talk to the DjangoCon Europe Support group to get help with this, including information on past event budgets.
We also like to see:
- Timelines
- Pictures
- Plans for online participation, and other ways to make the event more inclusive and reduce its environmental footprint
- Draft agreements with providers
- Alternatives you have considered
Have a look at our proposed DjangoCon Europe 2026 Licensing Agreement for the fine print on contractual requirements and involvement of the Django Software Foundation.
Submit your completed proposal by October 6th 2024 via our DjangoCon Europe 2026 expression of interest form, this time filling in as many fields as possible. We look forward to reviewing great proposals that continue the excellence the whole community associates with DjangoCon Europe.
Q&A
Can I organize a conference alone?
We strongly recommend that a team of people submit an application.
I/we don’t have a legal entity yet, is that a problem?
Depending on your jurisdiction, this is usually not a problem. But please share your plans about the entity you will use or form in your application.
Do I/we need experience with organizing conferences?
The support group is here to help you succeed. From experience, we know that many core groups of 2-3 people have been able to run a DjangoCon with guidance from previous organizers and help from volunteers.
What is required in order to announce an event?
Ultimately, a contract with the venue confirming the dates is crucial, since announcing a conference makes people book calendars, holidays, buy transportation and accommodation etc. This, however, would only be relevant after the DSF board has concluded the application process. Naturally, the application itself cannot contain any guarantees, but it’s good to check concrete dates with your venues to ensure they are actually open and currently available, before suggesting these dates in the application.
Do we have to do everything ourselves?
No. You will definitely be offered lots of help by the community. Typically, conference organizers will divide responsibilities into different teams, making it possible for more volunteers to join. Local organizers are free to choose which areas they want to invite the community to help out with, and a call will go out through a blog post announcement on djangoproject.com and social media.
What kind of support can we expect from the Django Software Foundation?
The DSF regularly provides grant funding to DjangoCon organizers, to the extent of $6,000 in recent editions. We also offer support via specific working groups:
- The dedicated DjangoCon Europe support working group.
- The social media working group can help you promote the event.
- The Code of Conduct working group works with all event organizers.
In addition, a lot of Individual Members of the DSF regularly volunteer at community events. If your team aren’t Individual Members, we can reach out to them on your behalf to find volunteers.
What dates are possible in 2026?
For 2026, DjangoCon Europe should happen between January 5th and April 27th, or June 4th and June 28th. This is to avoid the following community events’ provisional dates:
- PyCon US 2026: May 2026
- EuroPython 2026: July 2026
- DjangoCon US 2026: September - October 2026
- DjangoCon Africa 2026: August - September 2026
We also want to avoid the following holidays:
- New Year's Day: Wednesday 1st January 2026
- Chinese New Year: Tuesday 17th February 2026
- Eid Al-Fitr: Friday 20th March 2026
- Passover: Wednesday 1st - Thursday 9th April 2026
- Easter: Sunday 5th April 2026
- Eid Al-Adha: Tuesday 26th - Friday 29th May 2026
- Rosh Hashanah: Friday 11th - Sunday 13th September 2026
- Yom Kippur: Sunday 20th - Monday 21st September 2026
What cities or countries are possible?
Any city in Europe. This can be a city or country where DjangoCon Europe has happened in the past (Vigo, Edinburgh, Porto, Copenhagen, Heidelberg, Florence, Budapest, Cardiff, Toulon, Warsaw, Zurich, Amsterdam, Berlin), or a new locale.
References
Past calls
From The Django weblog at 2024-08-07 14:00:00
The Django team is happy to announce the release of Django 5.1.
The release notes showcase a kaleidoscope of improvements. A few highlights are:
- Easier guardrails for authentication: the new and shiny LoginRequiredMiddleware, when added to MIDDLEWARE, enforces authentication for all views by default.
- A more inclusive framework: Django 5.1 includes several accessibility enhancements, such as improved screen reader support in the admin interface, more semantic HTML elements, and better association of help text and labels with form fieldsets.
- The second oldest ticket fixed in this release provides the long awaited querystring template tag, which greatly simplifies the handling of query strings when building URLs in templates.
(If you are curious about the oldest ticket fixed in this release, check out Ticket #10743.)
You can get Django 5.1 from our downloads page or from the Python Package Index. The PGP key ID used for this release is Natalia Bidart: 2EE82A8D9470983E.
With the release of Django 5.1, Django 5.0 has reached the end of mainstream support. The final minor bug fix release, 5.0.8, was issued yesterday. Django 5.0 will receive security and data loss fixes until April 2025. All users are encouraged to upgrade before then to continue receiving fixes for security issues.
See the downloads page for a table of supported versions and the future release schedule.
From The Django weblog at 2024-08-06 14:39:29
Django security releases issued: 5.0.8 and 4.2.15
In accordance with our security release policy, the Django team is issuing releases for Django 5.0.8 and Django 4.2.15. These releases address the security issues detailed below. We encourage all users of Django to upgrade as soon as possible.
CVE-2024-41989: Memory exhaustion in django.utils.numberformat.floatformat()
The floatformat template filter is subject to significant memory consumption when given a string representation of a number in scientific notation with a large exponent.
Thanks to Elias Myllymäki for the report.
This issue has severity "moderate" according to the Django security policy.
CVE-2024-41990: Potential denial-of-service in django.utils.html.urlize()
The urlize() and urlizetrunc() template filters are subject to a potential denial-of-service attack via very large inputs with a specific sequence of characters.
Thanks to MProgrammer for the report.
This issue has severity "moderate" according to the Django security policy.
CVE-2024-41991: Potential denial-of-service vulnerability in django.utils.html.urlize() and AdminURLFieldWidget
The urlize and urlizetrunc template filters, and the AdminURLFieldWidget widget, are subject to a potential denial-of-service attack via certain inputs with a very large number of Unicode characters.
Thanks to Seokchan Yoon for the report.
This issue has severity "moderate" according to the Django security policy.
CVE-2024-42005: Potential SQL injection in QuerySet.values() and values_list()
QuerySet.values() and values_list() methods on models with a JSONField are subject to SQL injection in column aliases via a crafted JSON object key as a passed *arg.
Thanks to Eyal Gabay of EyalSec for the report.
This issue has severity "moderate" according to the Django security policy.
Affected supported versions
- Django main branch
- Django 5.1 (currently at release candidate status)
- Django 5.0
- Django 4.2
Resolution
Patches to resolve the issue have been applied to Django's main, 5.1, 5.0, and 4.2 branches. The patches may be obtained from the following changesets.
CVE-2024-41989: Memory exhaustion in django.utils.numberformat.floatformat()
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
CVE-2024-41990: Potential denial-of-service in django.utils.html.urlize()
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
CVE-2024-41991: Potential denial-of-service vulnerability in django.utils.html.urlize() and AdminURLFieldWidget
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
CVE-2024-42005: Potential SQL injection in QuerySet.values() and values_list()
- On the main branch
- On the 5.1 branch
- On the 5.0 branch
- On the 4.2 branch
The following releases have been issued
- Django 5.0.8 (download Django 5.0.8 | 5.0.8 checksums)
- Django 4.2.15 (download Django 4.2.15 | 4.2.15 checksums)
The PGP key ID used for this release is Sarah Boyce: 3955B19851EA96EF
General notes regarding security reporting
As always, we ask that potential security issues be reported via private email to security@djangoproject.com, and not via Django's Trac instance, nor via the Django Forum, nor via the django-developers list. Please see our security policies for further information.